Table of Contents
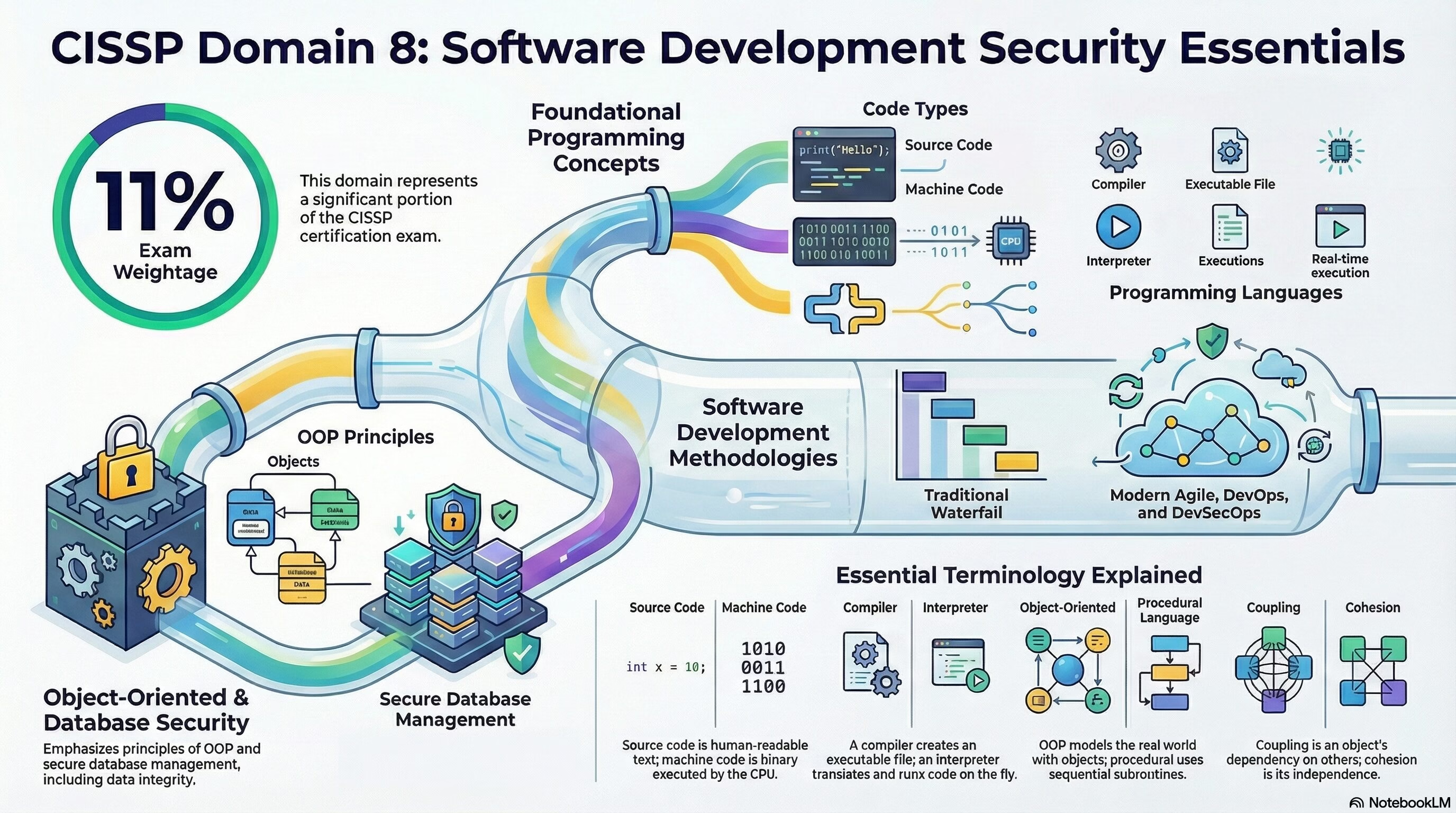
The Domain 8: Software Development Security of CISSP exam holds a total weightage of 11% in the exam.
Below are the summaries of key objectives of Domain 8: Software Development Security.
- Programming Concepts: This section covers the basics of programming, including machine code, source code, assemblers, compilers, interpreters, and bytecode. It also discusses procedural and object-oriented languages, fourth-generation programming languages, integrated development environments, and computer-aided software engineering.
- Application Development Methods: This part delves into various software development methodologies such as Waterfall Model, Sashimi Model, Agile Software Development, Scrum, Extreme Programming (XP), Spiral, Rapid Application Development (RAD), Prototyping, DevOps, DevSecOps, Continuous Integration and Continuous Delivery, Security Orchestration, Automation, and Response, Software Configuration Management, and Systems Development Life Cycle (SDLC).
- Databases: This section likely discusses the role and management of databases in software development, though the text provided does not provide specific details.
- Object-Oriented Design and Programming: This part explains the concept of object-oriented programming, which treats a program as a series of connected objects that communicate via messages. It contrasts this with procedural programming.
- Assessing the Effectiveness of Software Security: This section likely covers methods and frameworks for evaluating the security of software, though the text provided does not provide specific details.
- Artificial Intelligence: This part likely discusses the role of artificial intelligence in software development, though the text provided does not provide specific details.
Unique Terms and Definitions from Domain 8: Software Development Security
- Machine code – software that is executed directly by the CPU, consisting of a series of 1s and 0s that translate to instructions that are understood by the CPU.
- Source code – computer programming language instructions that are written in text and must be translated into machine code before execution by the CPU.
- Assembly language – a low-level computer programming language that uses short mnemonics, such as “ADD”, “SUB”, and “JMP”, that match to machine language instructions.
- Compiler – a program that takes source code, such as C or Basic, and compiles it into machine code, producing an executable file.
- Interpreter – a program that translates and executes source code on the fly, such as Python or shell code, without producing an executable file.
- Bytecode – an intermediary form of code, such as Java bytecode, that is platform-independent and must be converted into machine code by a virtual machine, such as the Java Virtual Machine (JVM).
- Procedural language – a computer programming language that uses subroutines, procedures, and functions, such as Basic, C, Fortran, and Pascal.
- Object-oriented language – a computer programming language that models the real world through the use of objects that combine methods and data, such as C++, Ruby, and Python.
- Fourth-generation programming language (4GL) – a computer programming language that is designed to increase a programmer’s efficiency by automating the creation of computer programming code, such as ColdFusion, Progress 4GL, and Oracle Reports.
- Integrated Development Environment (IDE) – a software application that provides a programmer with a single interface that can perform editing, debugging, syntax checking and highlighting, compiling, interpreting, and version control functions, such as Microsoft’s Visual Studio Code.
- Computer-Aided Software Engineering (CASE) – the use of software programs to assist in the creation and maintenance of other computer programs, such as 4GL, object-oriented languages, and GUIs.
- Top-Down programming – a programming approach that starts with the broadest and highest level requirements and works down towards the low-level technical implementation details.
- Bottom-Up programming – a programming approach that starts with the low-level technical implementation details and works up to the concept of the complete program.
- Closed source software – software that is typically released in executable form, keeping the source code confidential, such as Oracle and Microsoft Windows 11.
- Open source software – software that publishes source code publicly, allowing users to modify and share it, such as Ubuntu Linux and the Apache Web server.
- Proprietary software – software that is subject to intellectual property protections such as patents or copyrights, such as closed source software or some open source software.
- Free software – software that is free of charge to use (gratis) or free to use in any way (libre), or both (free squared), such as freeware, shareware, and GNU Public License (GPL) software.
- Software licensing – a legal agreement that defines the rights and obligations of the software provider and the software user, such as End-User License Agreements (EULAs), GPL, BSD, and Apache licenses.
- Application Development Model – a framework that defines the phases, activities, deliverables, and milestones of a software development project, such as the Waterfall Model, Spiral Model, Extreme Programming (XP), and DevOps.
- Configuration Management – a process that controls and documents the changes made to the software and hardware components of a system throughout its lifecycle, such as using a Configuration Management Plan (CM Plan), a Configuration Control Board (CCB), and a Configuration Monitoring process.
- Database – a structured collection of related data that allows queries, insertions, deletions, and other functions, managed by a Database Management System (DBMS), such as Oracle, MySQL, and MongoDB.
- Relational database – a database that contains two-dimensional tables of related data, where each table has rows (tuples or records) and columns (attributes or fields), and a unique value called the primary key in each tuple.
- Foreign key – a key in a related database table that matches a primary key in a parent database table, allowing the tables to be joined, such as the SSN attribute in the HR database table that matches the SSN attribute in the employee database table.
- Referential integrity – a database property that ensures that every foreign key in a secondary table matches a primary key in the parent table, preventing orphaned records, such as the tuple with the foreign key 467-51-9732 in the HR database table that has no matching entry in the employee database table.
- Semantic integrity – a database property that ensures that each attribute value is consistent with the attribute data type, preventing invalid data, such as the cell “Nexus 6” in the HR database table that violates the sick time attribute data type of days.
- Entity integrity – a database property that ensures that each tuple has a unique primary key that is not null, preventing duplicate or missing records, such as the last two tuples in the HR database table that have the same primary key 990-69-4771.
- Database normalization – a process that seeks to make the data in a database table logically concise, organized, and consistent, removing redundant data and improving the integrity and availability of the database, following three rules called forms: First Normal Form (1NF), Second Normal Form (2NF), and Third Normal Form (3NF).
- Database view – the result of a query on a database table, which may be used to provide a constrained user interface, such as showing only the employee tuples with the title attribute of “Detective”.
- Database replication – a database high availability option that mirrors a live database, allowing simultaneous reads and writes to multiple replicated databases by clients, using a two-phase or multiphase commit to ensure integrity.
- Database shadowing – a database high availability option that mirrors all changes made to a primary database, but clients do not access the shadow, serving as a live data backup of the primary.
- Data warehousing – the collection and storage of large amounts of data in a database, requiring large scalable storage solutions and high performance, allowing analysis and searches of the data.
- Data mining – the search for patterns in a data warehouse, using statistical or machine learning techniques, such as finding signs of fraud, customer preferences, or market trends.
- Object – a “black box” that combines code and data, and sends and receives messages, such as Addy, an object that adds two integers.
- Class – a template or blueprint that defines the attributes and methods of an object, such as mathematical operators, the parent class of Addy.
- Method – a function or procedure that is performed by an object, such as addition, the method of Addy.
- Inheritance – a mechanism that allows an object to acquire the attributes and methods of another object or class, such as Addy inheriting an understanding of numbers and math from his parent class mathematical operators.
- Message – an input or output that is sent or received by an object, such as 1 + 2, the input message of Addy, or 3, the output message of Addy.
- Delegation – a mechanism that allows an object to pass a message to another object if it does not know how to perform a requested function, such as Addy delegating the message 7 – 4 to Subby, another object that can subtract two integers.
- Polymorphism – a mechanism that allows an object to change its behavior based on the context of the message, such as Addy overloading the “+” operator to perform addition or concatenation, depending on the data type of the message.
- Polyinstantiation – a mechanism that allows two objects with the same name to contain different data, such as two Addy objects with secret and top secret data, respectively.
- Coupling – a measure of how much an object depends on other objects to perform its functions, such as Addy having high coupling and low cohesion, because he must delegate any message that does not contain a “+”.
- Cohesion – a measure of how independent an object is in performing its functions, such as Calculator having low coupling and high cohesion, because he can perform most mathematical operations without delegation.
- Artificial Intelligence – the science of programming electronic computers to “think” more intelligently, sometimes mimicking the ability of mammal brains, such as playing chess, recognizing faces, or driving cars.
- Expert system – a type of artificial intelligence that uses a knowledge base of “if/then” statements and an inference engine to make decisions based on rules, such as diagnosing diseases, recommending products, or planning routes.
- Genetic algorithm and programming – a type of artificial intelligence that uses evolutionary principles to generate code that solves a problem, such as creating a Pac-Man playing program, a robotic soccer team, or a network intrusion detection system
Multiple Choice Questions quiz
|
Flashcard quiz
|