Table of Contents
The Domain 6: Security Assessment and Testing of CISSP exam holds a total weightage of 12% in the exam.
Below are the summaries of key objectives of Domain 6: Security Assessment and Testing.
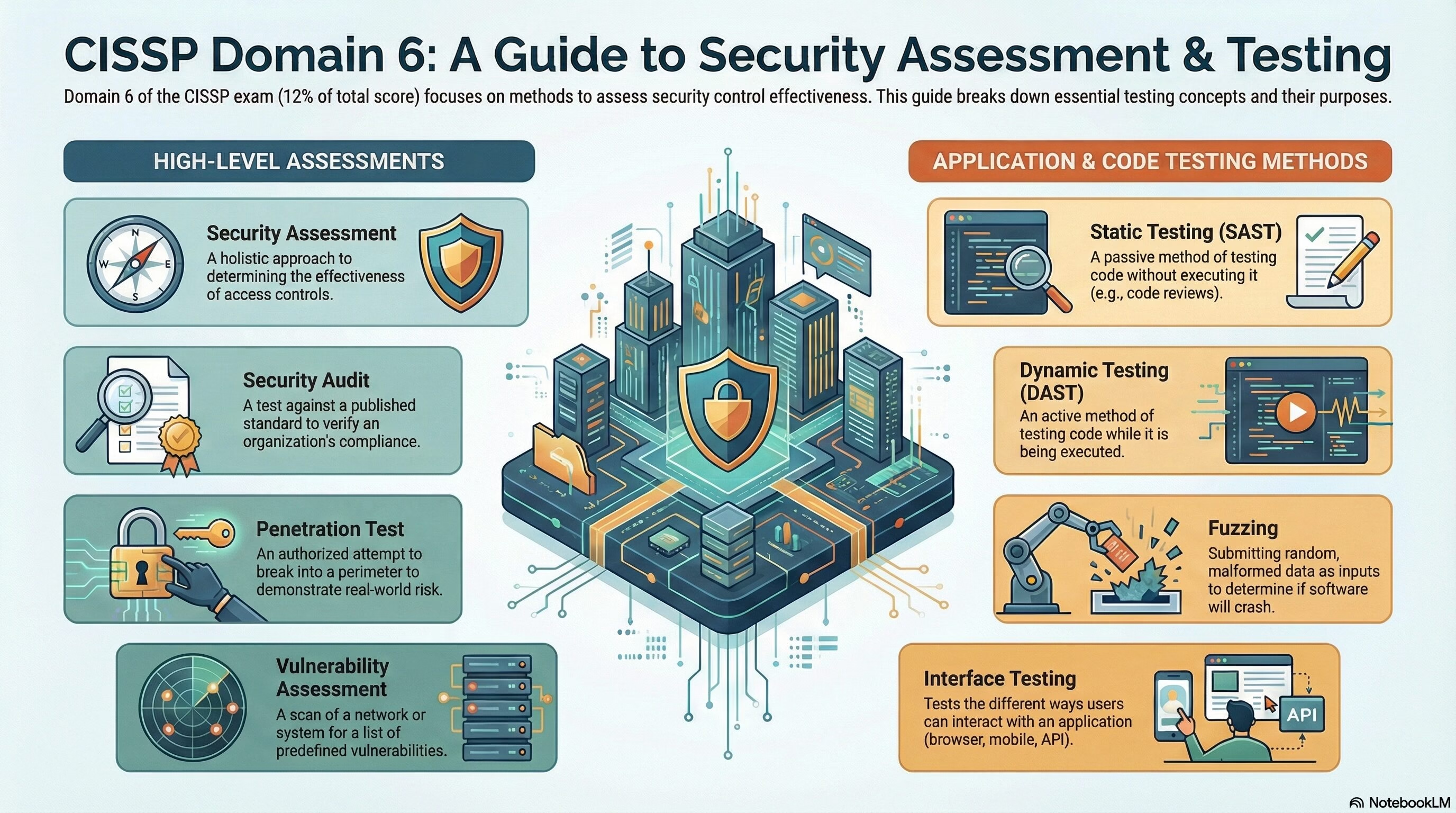
- Security Control Testing: This objective covers various methods to assess the effectiveness of security controls, such as penetration testing, vulnerability assessment, security audit, security assessment, log review, compliance check, synthetic transactions, application security testing, and fuzzing.
- Collecting Security Process Data: This objective covers the types of data that need to be collected to support the security processes and controls, such as account management, management review and approval, key performance and risk indicators, backup verification data, and tracking training and awareness.
- Analyzing and Reporting Test Outputs: This objective covers the steps to analyze the results of security testing and reporting them to the relevant stakeholders, such as prioritizing and triaging findings, managing exceptions, performing test coverage analysis, and using traceability matrix.
Unique Terms and Definitions from Domain 6: Security Assessment and Testing
- Security Assessment: A holistic approach to determining the effectiveness of access control, and has a broad scope. It may include other tests, such as penetration tests, vulnerability assessments, and security audits.
- Security Audit: A test against a published standard, such as PCI-DSS, to verify an organization’s compliance with the specified requirements.
- Penetration Test: An authorized attempt to break into an organization’s physical or electronic perimeter, and sometimes both, to demonstrate real-world risk. It may use different levels of knowledge, such as zero, partial, or full knowledge, and different techniques, such as network, wireless, physical, or social engineering attacks.
- Vulnerability Assessment: A scan of a network or system for a list of predefined vulnerabilities, such as system misconfiguration, outdated software, or a lack of patching. It only shows one half of the risk equation, and needs to be matched with threats to map true risk.
- Static Testing: A passive method of testing code without executing it. It includes walkthroughs, syntax checking, code reviews, and secure compilers. It can identify potential flaws in code that may not be exposed by dynamic testing.
- Dynamic Testing: An active method of testing code while executing it. It includes fuzzing, black box testing, combinatorial testing, and misuse case testing. It can validate the existence of vulnerabilities and measure the performance and functionality of the code.
- Traceability Matrix: A tool that maps customer use cases to test cases, to ensure that the software meets the customer’s operational requirements. It helps to track the coverage and completeness of the testing process.
- Synthetic Transactions: Scripts or tools that simulate activities normally performed in an application, such as checking balances, making transfers, or depositing checks. They are used to establish expected norms for the performance and functionality of the application, and to monitor any changes or deviations.
- Test Coverage Analysis: A method of measuring the degree to which code testing applies to the entire application. It helps to identify any gaps or areas that are not tested, and to improve the quality and reliability of the code.
- Interface Testing: A method of testing the different ways users can interact with the application, such as browser, mobile, or API. It helps to ensure that security is uniformly applied across the various interfaces, and to prevent any potential attack vectors.
- Security Assessment – A holistic approach to assessing the effectiveness of access control, and has a broad scope that may include other tests, such as penetration tests and audits.
- Security Audit – A test against a published standard, such as PCI-DSS, to verify compliance with the required controls.
- Penetration Test – An authorized attempt to break into an organization’s physical or electronic perimeter, and sometimes both, to demonstrate real-world risk.
- Vulnerability Assessment – A scan of a network or system for a list of predefined vulnerabilities, such as system misconfiguration, outdated software, or a lack of patching.
- Synthetic Transactions – Scripts or tools that simulate activities normally performed in an application, to establish expected norms for the performance and functionality of the application.
- Static Application Security Testing (SAST) – A passive method of testing code without executing it, such as walkthroughs, syntax checking, and code reviews.
- Dynamic Application Security Testing (DAST) – An active method of testing code while executing it, such as fuzzing and black box testing.
- Fuzzing – A type of black box testing that submits random, malformed data as inputs into software programs to determine if they will crash.
- Combinatorial Software Testing – A black box testing method that seeks to identify and test all unique combinations of software inputs, such as pairwise testing.
- Traceability Matrix – A tool that maps customer requirements to the software testing plan, to ensure that the software meets the customer’s operational needs.
Multiple Choice Questions quiz
|
Flashcard quiz
|