Table of Contents
The Domain 5: Identity and Access Management (IAM) of CISSP exam holds a total weightage of 13% in the exam.
Below are the summaries of key objectives of Domain 5: Identity and Access Management (IAM).
- Identity and Access Provisioning: This objective covers the processes and technologies for creating, maintaining, and terminating user accounts and access rights. It also discusses identity lifecycle management, provisioning and deprovisioning, and identity repositories.
- Authentication Methods: This objective explains the different types of authentication factors and methods, such as passwords, tokens, biometrics, and federated identity management. It also covers the concepts of single sign-on, multi factor authentication, and session management.
- Access Control Technologies: This objective describes the various technologies and protocols for implementing access control, such as centralized and decentralized access control, SAML, OAuth, OpenID Connect, and Identity as a Service. It also covers the advantages and disadvantages of each technology and the security considerations involved.
- Access Control Models: This objective introduces the different models and frameworks for defining and enforcing access control policies, such as discretionary access control, mandatory access control, role-based access control, and attribute-based access control. It also covers the concepts of least privilege, separation of duties, and access control matrix.
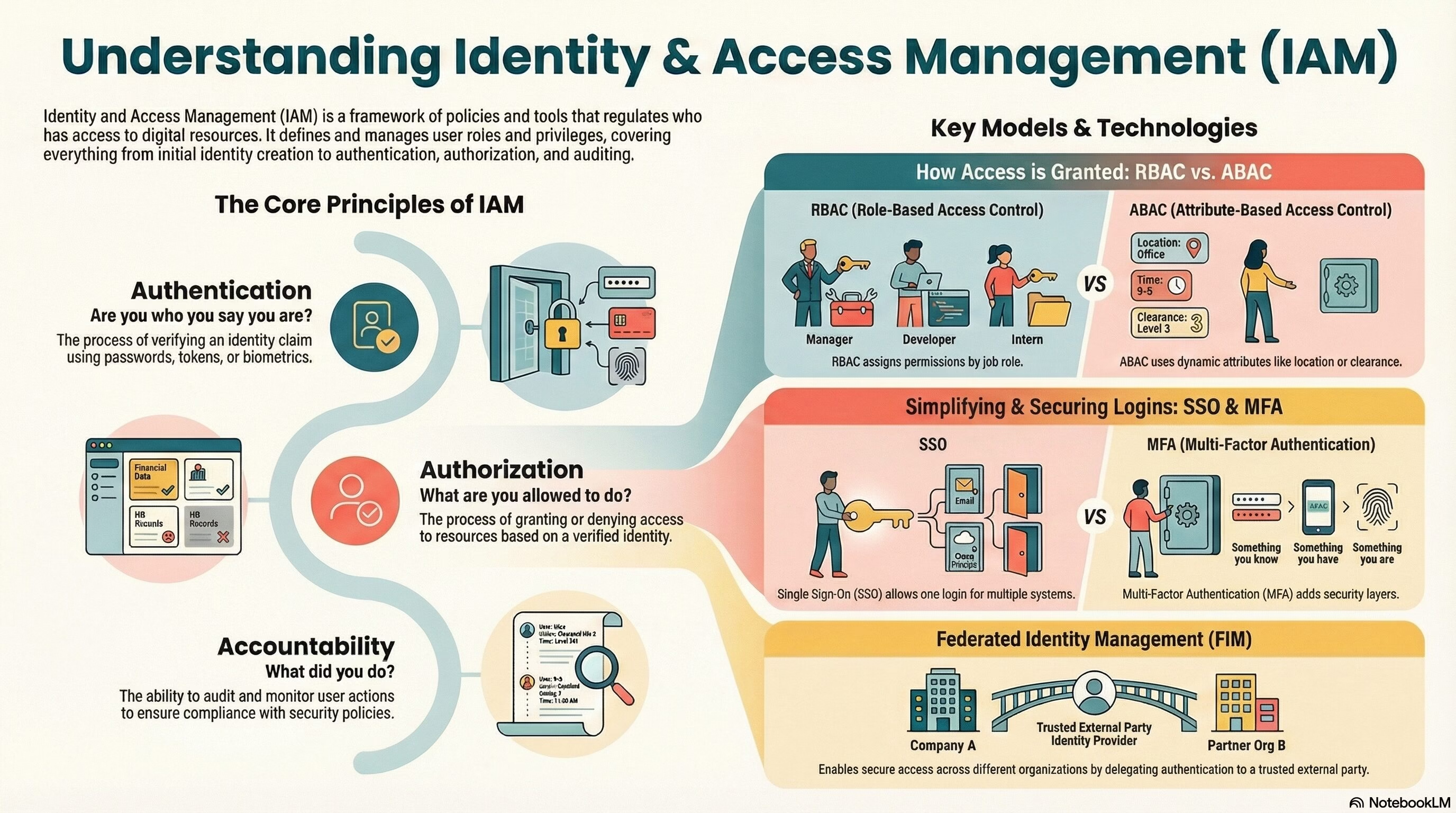
- Federated Identity Management (FIM): This objective explores the benefits and challenges of federating identity across multiple organizations and systems, such as enabling single sign-on, reducing administrative overhead, and enhancing user experience. It also covers the standards and protocols for FIM, such as SAML, OAuth, OpenID Connect, and Identity as a Service.
Unique Terms and Definitions from Domain 5: Identity and Access Management (IAM)
- Authentication Methods – the ways of verifying the identity of a subject, such as passwords, tokens, biometrics, etc.
- Access Control Technologies – the tools and mechanisms that implement access control policies, such as access control lists, role-based access control, single sign-on, etc.
- Access Control Models – the frameworks that define how access decisions are made, such as discretionary access control, mandatory access control, non-discretionary access control, etc.
- Identity Management – the process of creating, maintaining, and terminating digital identities for users and devices, and managing their attributes and credentials
- Access Management – the process of granting, restricting, and revoking access to resources based on the identity, role, or context of the users and devices
- Identity Federation – the process of delegating the responsibility of authenticating a user to a trusted external party, and sharing identity attributes across multiple organizations
- Identity-as-a-Service (IDaaS) – a cloud-based delivery model for identity and access management solutions, such as authentication, authorization, provisioning, etc.
- Credential Management Systems – systems that help harden user credentials by providing secure password generation, storage, rotation, and audit
- Federated Identity Management (FIdM) – a type of identity management that enables single sign-on across multiple systems and domains, using standards such as SAML or OpenID
- Lightweight Directory Access Protocol (LDAP) – a common open protocol for interfacing and querying directory service information provided by network operating systems, using port 389 via TCP or UDP
- Kerberos – a third-party authentication service that uses tickets and encryption to provide single sign-on and mutual authentication
- Security Association Markup Language (SAML) – an XML-based framework for exchanging security information, including authentication data, between different systems and domains
- Transitive Trust – a trust relationship that extends to other trust partners, such as if A trusts B, and B trusts C, then A trusts C
- Identity and Access Management (IAM): a set of processes, policies, and tools that regulate who or what has access to applications in the cloud or on-premises. IAM defines and manages the roles and privileges of each user or device that requests access to these applications.
- Authentication: the process of verifying an identity claim, such as a username and password, a token, or a biometric feature.
- Authorization: the process of granting or denying access to resources based on the authenticated identity and the access policies.
- Accountability: the ability to audit and monitor the actions of users or devices on a system and ensure compliance with security policies and regulations.
- Single Sign-On (SSO): a technique that allows users to authenticate once and then access multiple, different systems without re-authenticating. SSO simplifies the user experience and reduces the administrative overhead of managing multiple credentials.
- Multi-factor Authentication (MFA): a technique that requires users to provide more than one piece of evidence to prove their identity, such as a password, a token, a fingerprint, or a facial scan. MFA enhances the security of authentication by making it harder for attackers to compromise credentials.
- Role-Based Access Control (RBAC): a model that assigns access permissions to users based on their roles in an organization, such as manager, employee, or customer. RBAC simplifies the administration of access control by reducing the number of individual permissions that need to be managed.
- Attribute-Based Access Control (ABAC): a model that assigns access permissions to users based on their attributes, such as location, department, or clearance level. ABAC allows for more fine-grained and dynamic access control by considering various factors at the time of the access request.
- Privileged Access Management (PAM): a technique that controls and monitors the access of users or devices that have elevated privileges, such as administrators, root users, or service accounts. PAM helps prevent unauthorized or malicious use of privileged accounts by enforcing strict policies, such as password rotation, session recording, and just-in-time access.
Multiple Choice Questions quiz
|
Flashcard quiz
|