Table of Contents
The Domain 4: Communication and Network Security of CISSP exam holds a total weightage of 13% in the exam.
Below are the summaries of key objectives of Domain 4: Communication and Network Security.
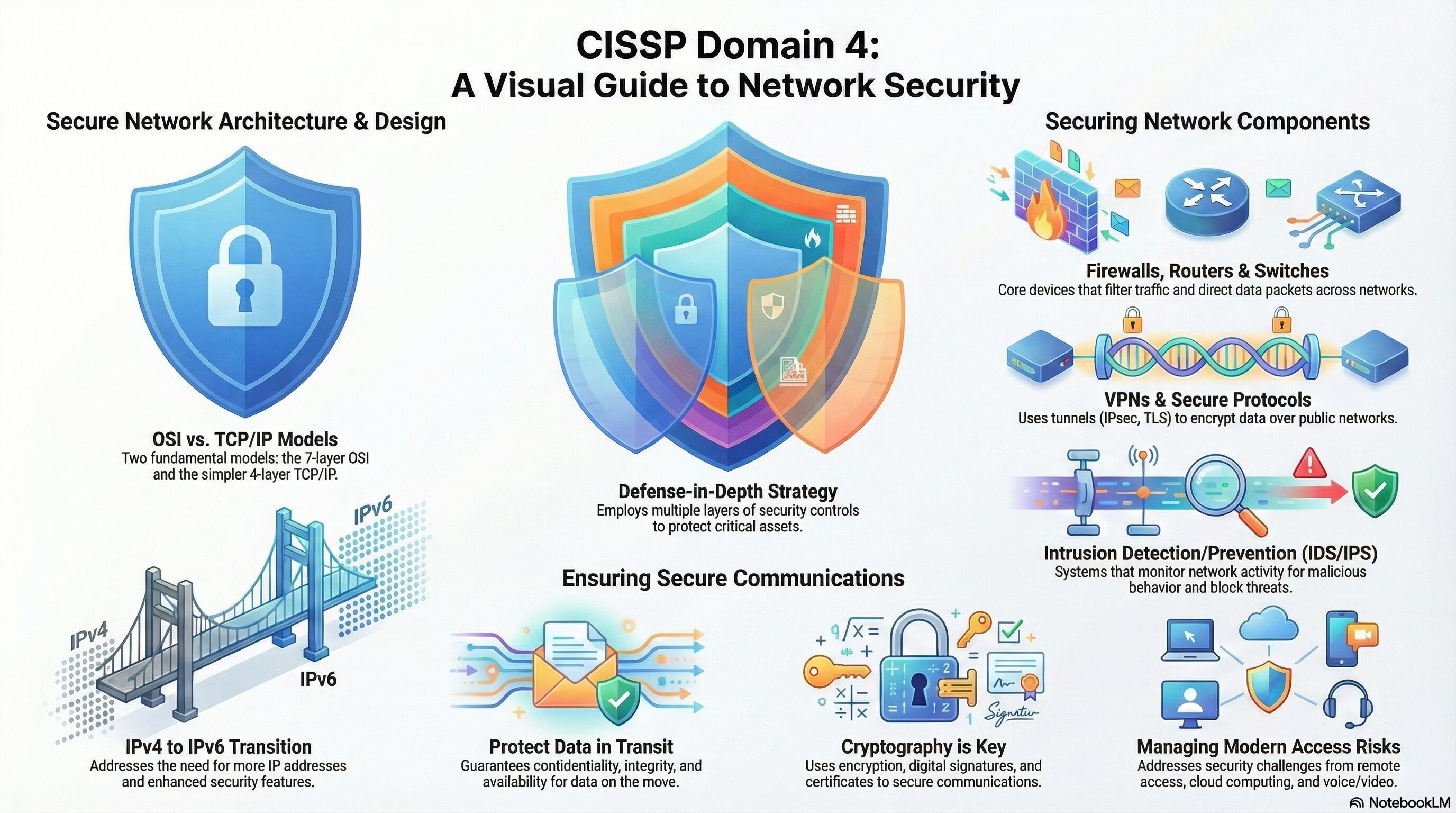
- Network Architecture and Design: This section covers the concepts and principles of network design, such as defense-in-depth, network models, network types, and network protocols. It also explains the differences between classful and classless networks, IPv4 and IPv6, and various types of network address translation.
- Secure Network Devices and Protocols: This section discusses the security features and functions of various network devices and protocols, such as routers, switches, firewalls, intrusion detection and prevention systems, VPNs, wireless networks, and secure protocols such as IPsec, SSL/TLS, SSH, and SFTP.
- Secure Communications: This section focuses on the methods and technologies for ensuring the confidentiality, integrity, and availability of data in transit, such as encryption, authentication, digital signatures, certificates, key management, and secure email. It also covers the security risks and challenges of remote access, voice and video communications, and cloud computing.
Unique Terms and Definitions from Domain 4: Communication and Network Security
- Packet-switched network – a form of networking where bandwidth is shared and data is carried in units called packets
- The OSI model – a network model with seven layers: physical, data link, network, transport, session, presentation, and application
- The TCP/IP model – a simpler network model with four layers: network access, Internet, transport, and application
- MAC address – a unique hardware address of an Ethernet network interface card (NIC), typically burned in at the factory
- Firewall – a device or software that filters traffic based on rules and policies, and blocks or allows traffic based on the source, destination, port, or protocol
- Proxy – a device or software that acts as an intermediary between a client and a server, and can perform functions such as caching, filtering, or modifying requests or responses
- VPN – Virtual Private Network, a secure tunnel that encrypts and protects data in transit over a public network, such as the Internet
- TLS and IPsec – two protocols that provide security for data in transit, by using encryption, authentication, and integrity mechanisms
- Authentication – the process of verifying the identity of a user, device, or other entity in a system
- Authorization – the process of granting or denying access to resources based on the identity or role of an entity
- Encryption – the process of transforming data into an unreadable form, using a secret key or algorithm, to protect its confidentiality
- Decryption – the process of reversing encryption, using the same or a different key or algorithm, to restore the original data
- Symmetric cryptography – a type of encryption that uses the same key for encryption and decryption
- Asymmetric cryptography – a type of encryption that uses a pair of keys, one public and one private, and uses one key for encryption and the other for decryption
- Digital signature – a cryptographic technique that uses asymmetric cryptography to verify the authenticity and integrity of a message or document
- Digital certificate – a digital document that contains information about an entity and its public key, and is signed by a trusted authority
- PKI – Public Key Infrastructure, a system that manages the creation, distribution, and verification of digital certificates and public keys
- Hashing – the process of applying a mathematical function to data, to produce a fixed-length output called a hash or digest, that uniquely identifies the data
- HMAC – Hash-based Message Authentication Code, a technique that uses hashing and a secret key to verify the integrity and authenticity of a message
- Malware – malicious software that performs harmful or unwanted actions on a system, such as viruses, worms, trojans, ransomware, spyware, etc.
- Antivirus – software that detects and removes malware from a system, by using signatures, heuristics, or behavior analysis
- IDS and IPS – Intrusion Detection System and Intrusion Prevention System, devices or software that monitor network or system activity for malicious or anomalous behavior, and alert or block the activity accordingly
- Honeypot – a decoy system or network that is designed to attract and trap attackers, and collect information about their techniques and motives
- Phishing – a type of social engineering attack that uses fraudulent emails or websites to trick users into revealing sensitive information or installing malware
- DDoS – Distributed Denial-of-Service, a type of attack that floods a target system or network with a large amount of traffic or requests, to overwhelm its resources and disrupt its normal functioning
- Zero-day – a vulnerability that is unknown to the vendor or the public, and can be exploited by attackers before a patch or fix is available
- Penetration testing – a method of evaluating the security of a system or network by simulating an attack, and identifying and exploiting vulnerabilities
- Vulnerability scanning – a method of assessing the security of a system or network by using automated tools to detect and report known vulnerabilities
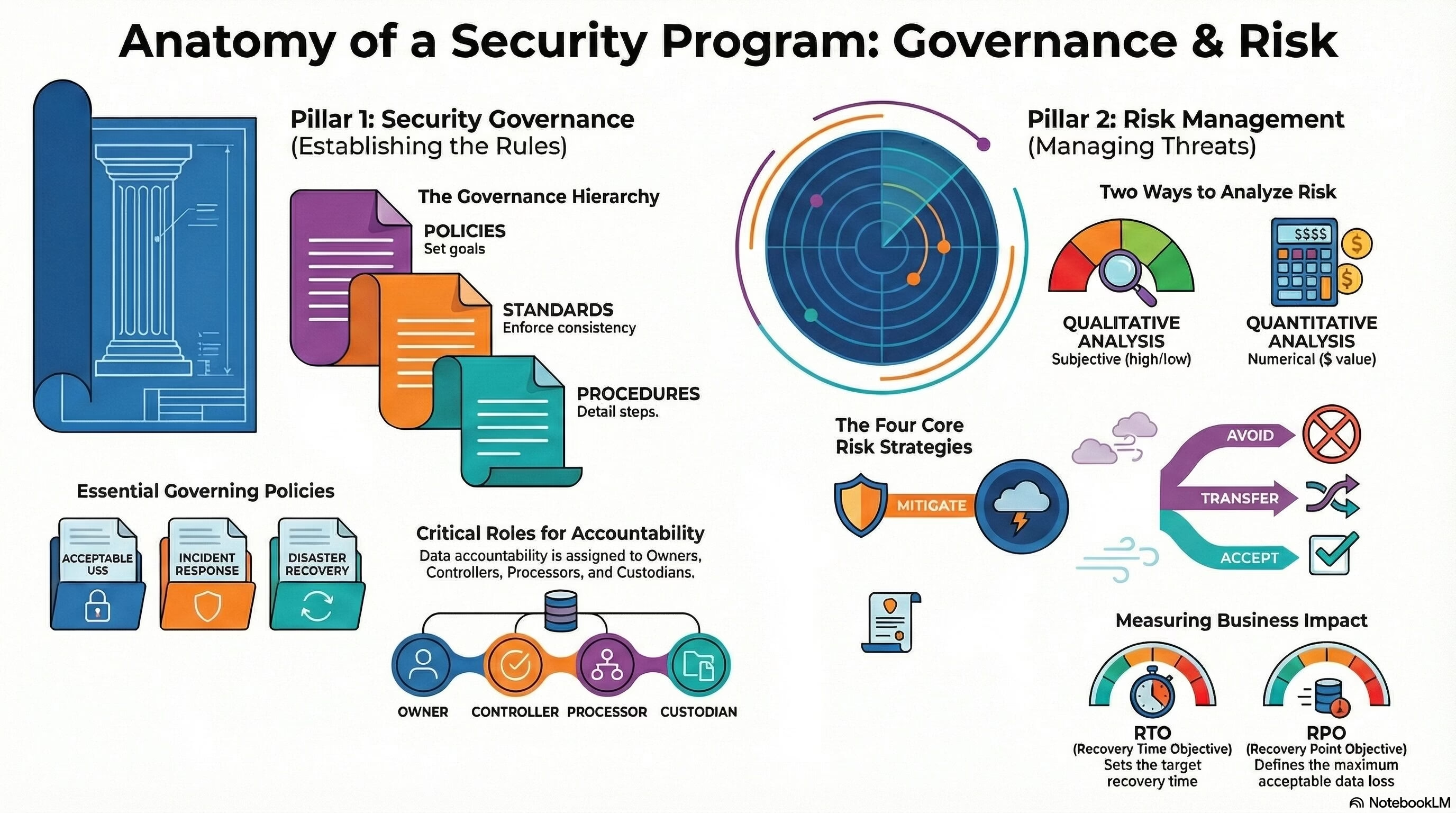
- Risk assessment – a process of identifying, analyzing, and evaluating the risks that an organization faces, and determining the appropriate controls to mitigate or accept them
- Incident response – a process of preparing for, detecting, containing, analyzing, and recovering from security incidents, and preventing or minimizing their impact
- Business continuity – the ability of an organization to maintain its essential functions and operations during and after a disruption, such as a natural disaster or a cyberattack
- Disaster recovery – the process of restoring the normal operations and functions of an organization after a disruption, by using backup systems, data, and resources.
- Defense-in-depth: A security strategy that employs multiple layers of controls to protect against possible attacks, so that the failure of any one control does not compromise the overall security.
- Packet: A unit of data that is transmitted over a packet-switched network, such as the Internet. A packet consists of a header and a payload, and may be fragmented and reassembled along the way.
- Router: A network device that routes packets from one network to another, based on their destination IP addresses. Routers operate at the network layer (Layer 3) of the OSI model.
- TCP: Transmission Control Protocol, a reliable, connection-oriented transport layer protocol that ensures the delivery and sequencing of packets. TCP uses acknowledgments, retransmissions, and flow control mechanisms to provide reliable service.
- UDP: User Datagram Protocol, an unreliable, connectionless transport layer protocol that does not guarantee the delivery or sequencing of packets. UDP is faster and more efficient than TCP, but does not provide any error recovery or congestion control.
- IP: Internet Protocol, a network layer protocol that provides logical addressing and routing for packets across the Internet. IP is responsible for fragmentation and reassembly of packets, as well as error detection and reporting. IP has two versions: IPv4 and IPv6.
- IPv4: Internet Protocol version 4, the most widely used version of IP, which uses 32-bit addresses to identify hosts and networks. IPv4 has a limited address space of about 4.3 billion addresses, which is insufficient for the growing number of devices connected to the Internet.
- IPv6: Internet Protocol version 6, the successor of IPv4, which uses 128-bit addresses to identify hosts and networks. IPv6 has a virtually unlimited address space of about 3.4 x 10^38 addresses, which allows for more efficient and secure communication. IPv6 also supports features such as stateless autoconfiguration, multicast, and mobility.
- NAT: Network Address Translation, a technique that allows private IP addresses to be translated into public IP addresses, and vice versa, when crossing network boundaries. NAT helps conserve the scarce IPv4 address space and enhance security by hiding the internal network structure from the outside world.
- CIDR: Classless Inter-Domain Routing, a method of dividing the IP address space into variable-sized networks, using a slash notation to indicate the network prefix length. For example, 192.0.2.0/24 represents a network with 256 addresses, where the first 24 bits are the network prefix and the remaining 8 bits are the host identifier. CIDR allows for more flexible and efficient allocation of IP addresses than the classful system.
Multiple Choice Questions quiz
|
Flashcard quiz
|