Table of Contents
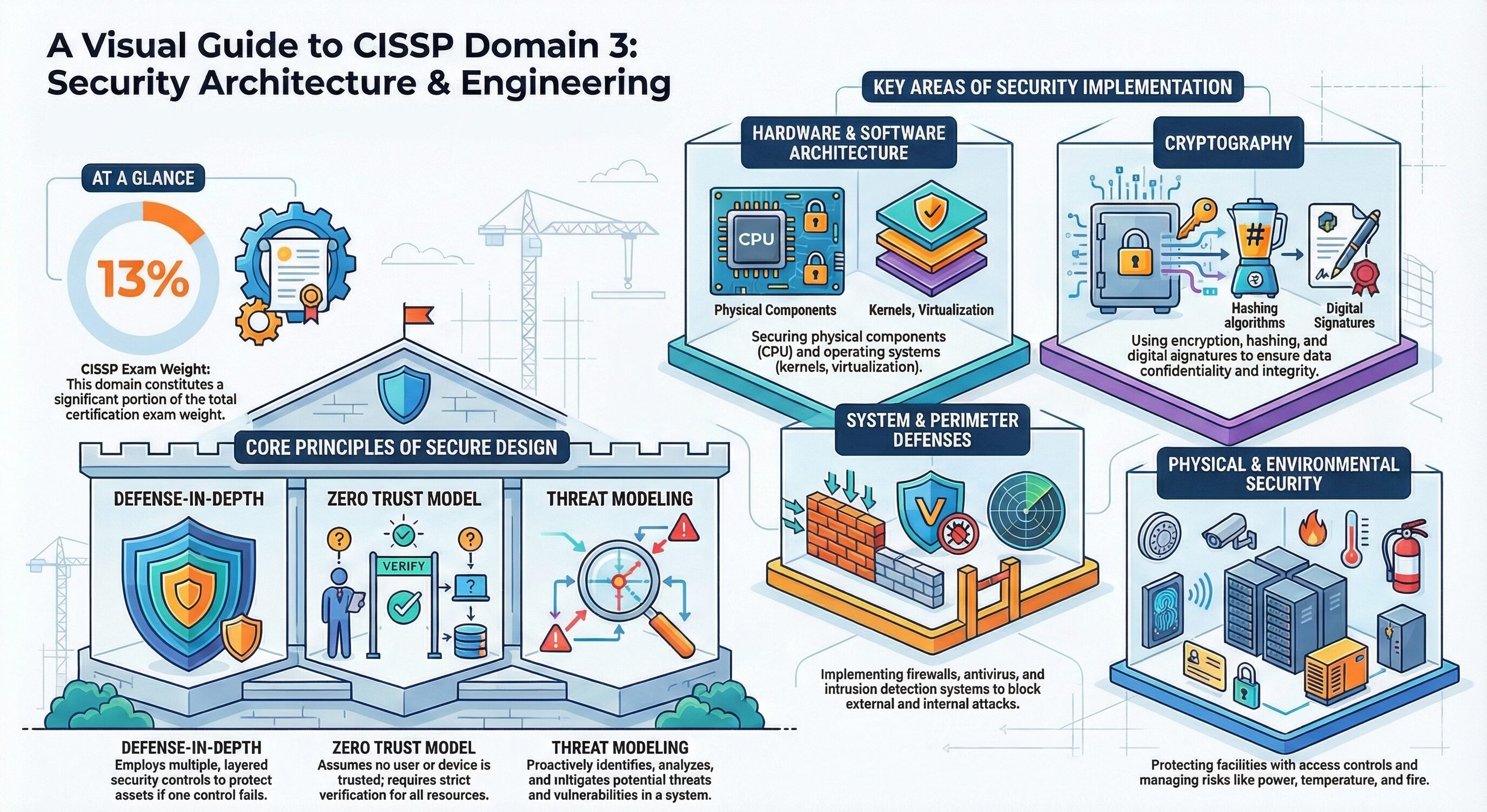
The Domain 3: Security Architecture and Engineering of CISSP exam holds a total weightage of 13% in the exam.
Below are the summaries of key objectives of Domain 3: Security Architecture and Engineering.
- Secure Design Principles: Understand the concepts and methods for designing secure systems, such as threat modeling, defense-in-depth, zero trust, privacy by design, fail securely, separation of duties, and others.
- Security Models: Learn about the formal frameworks and rules for implementing security policies and enforcing access control, such as Bell-LaPadula, Biba, Clark-Wilson, Chinese Wall, and others.
- Evaluation Methods, Certification, and Accreditation: Explore the standards and criteria for assessing the security of IT products and systems, such as the Common Criteria and its evaluation assurance levels.
- Secure System Design Concepts: Apply the general principles and techniques for building secure systems, such as layering, abstraction, security domains, the ring model, and others.
- Secure Hardware Architecture: Examine the physical components and features that support security, such as the system unit, the motherboard, the CPU, the bus, the watchdog timer, and others.
- Secure Operating System and Software Architecture: Analyze the structure and functionality of operating systems and software that provide security services, such as kernels, processes, threads, interrupts, virtualization, cloud, and distributed computing.
- System Vulnerabilities, Threats, and Countermeasures: Identify and mitigate the common risks and attacks that affect the security of systems, such as buffer overflows, race conditions, covert channels, malware, denial of service, and others.
- Cornerstone Cryptographic Concepts: Review the basic concepts and terminology of cryptography, such as encryption, decryption, cipher, key, plaintext, ciphertext, and others.
- Types of Cryptography: Compare and contrast the different types of cryptography, such as symmetric, asymmetric, hash, digital signature, and others.
- Cryptographic Attacks: Recognize and prevent the various types of attacks that target cryptographic systems, such as brute force, ciphertext-only, known-plaintext, chosen-plaintext, chosen-ciphertext, and others.
- Implementing Cryptography: Understand the methods and tools for applying cryptography to secure data and communications, such as algorithms, protocols, certificates, key management, and others.
- Perimeter Defenses: Implement the security measures that protect the boundaries of a system or network, such as firewalls, proxies, gateways, routers, switches, and others.
- Site Selection, Design, and Configuration: Choose and configure the physical location and layout of a system or network to enhance security, such as locks, doors, windows, lighting, cameras, alarms, and others.
- System Defenses: Deploy the security controls that protect the internal components and operations of a system or network, such as antivirus, antispyware, antispam, intrusion detection, intrusion prevention, and others.
- Environmental Controls: Manage the environmental factors that affect the security and availability of a system or network, such as temperature, humidity, power, fire, water, and others.
Unique Terms and Definitions from CISSP Domain 3: Security Architecture and Engineering
- Security Engineering – the discipline of designing, building, and maintaining secure systems that can resist attacks and recover from them.
- Security Models – formal frameworks that define the rules and principles for implementing and enforcing security policies in a system.
- Evaluation Methods, Certification and Accreditation – processes and standards for assessing the security level and compliance of a system or product.
- Secure System Design Concepts – principles and best practices for creating secure systems, such as defense-in-depth, least privilege, fail-safe defaults, etc.
- Secure Hardware Architecture – the design and implementation of hardware components and devices that support security functions and features, such as processors, memory, buses, input/output, etc.
- Secure Operating System and Software Architecture – the design and implementation of software components and applications that support security functions and features, such as kernels, drivers, services, middleware, etc.
- Virtualization and Distributed Computing – technologies and methods for creating and managing multiple virtual machines or systems that share resources and communicate over a network.
- System Vulnerabilities, Threats and Countermeasures – the identification and analysis of weaknesses, risks, and attacks that affect a system, and the implementation of solutions and controls to mitigate them.
- Cornerstone Cryptographic Concepts – the fundamental concepts and techniques of cryptography, such as encryption, decryption, hashing, digital signatures, etc.
- History of Cryptography – the origin and evolution of cryptography, from ancient ciphers to modern algorithms and standards.
- Types of Cryptography – the classification and comparison of different cryptographic methods and systems, such as symmetric, asymmetric, stream, block, etc.
- Cryptographic Attacks – the methods and techniques for breaking or compromising cryptographic systems, such as brute force, birthday, chosen plaintext, etc.
- Implementing Cryptography – the practical aspects and challenges of applying cryptography in real-world scenarios, such as key management, protocols, standards, etc.
- Perimeter Defenses – the security measures and devices that protect the boundary of a system or network from unauthorized access, such as firewalls, routers, proxies, etc.
- Site Selection, Design, and Configuration – the process and criteria for choosing, building, and setting up a secure facility or data center, such as topography, utility reliability, crime, site marking, etc.
- System Defenses – the security measures and devices that protect the internal components and data of a system or network from unauthorized access, such as antivirus, IDS, IPS, etc.
- Environmental Controls – the physical and technical controls that maintain the optimal environmental conditions for a system or facility, such as temperature, humidity, power, fire, etc.
- Threat Modeling: a process of identifying, analyzing, and mitigating the threats to a system or application.
- Zero Trust: a security model that assumes no network user, packet, interface, or device is trusted, and applies strict verification and enforcement mechanisms to all resources and transactions.
- State Machine Model: a mathematical model that represents all the possible states and transitions of a system, and proves its security by ensuring that every state is secure.
- Polyinstantiation: a technique that allows multiple records with the same primary key to exist in a multilevel secure database, preventing inference attacks based on the absence of data.
- Inference and Aggregation: two types of attacks that exploit the logical connections or mathematical calculations between lower-level data to derive higher-level information.
- Ring Model: a hardware-based security model that uses different privilege levels to isolate and protect domains, such as the kernel and the user applications.
- Digital Signature: a cryptographic technique that uses asymmetric encryption and hashing to provide non-repudiation, authentication, and integrity for a document or message.
- Key Clustering: a phenomenon that occurs when two different symmetric keys produce the same ciphertext for the same plaintext, reducing the effective key space and security of the cipher.
- Site Marking: a design decision that determines whether a facility or data center is externally labeled or identified, affecting its visibility and attractiveness to potential attackers.
- Smart Card: a physical access control device that contains an integrated circuit chip that can store and process data, such as cryptographic keys, certificates, or biometric information.
Multiple Choice Questions quiz
|
Flashcard quiz
|