Table of Contents
The Domain 2: Asset Security of CISSP exam holds a total weightage of 10% in the exam
Below are the summaries of key objectives of Domain 2: Asset Security.
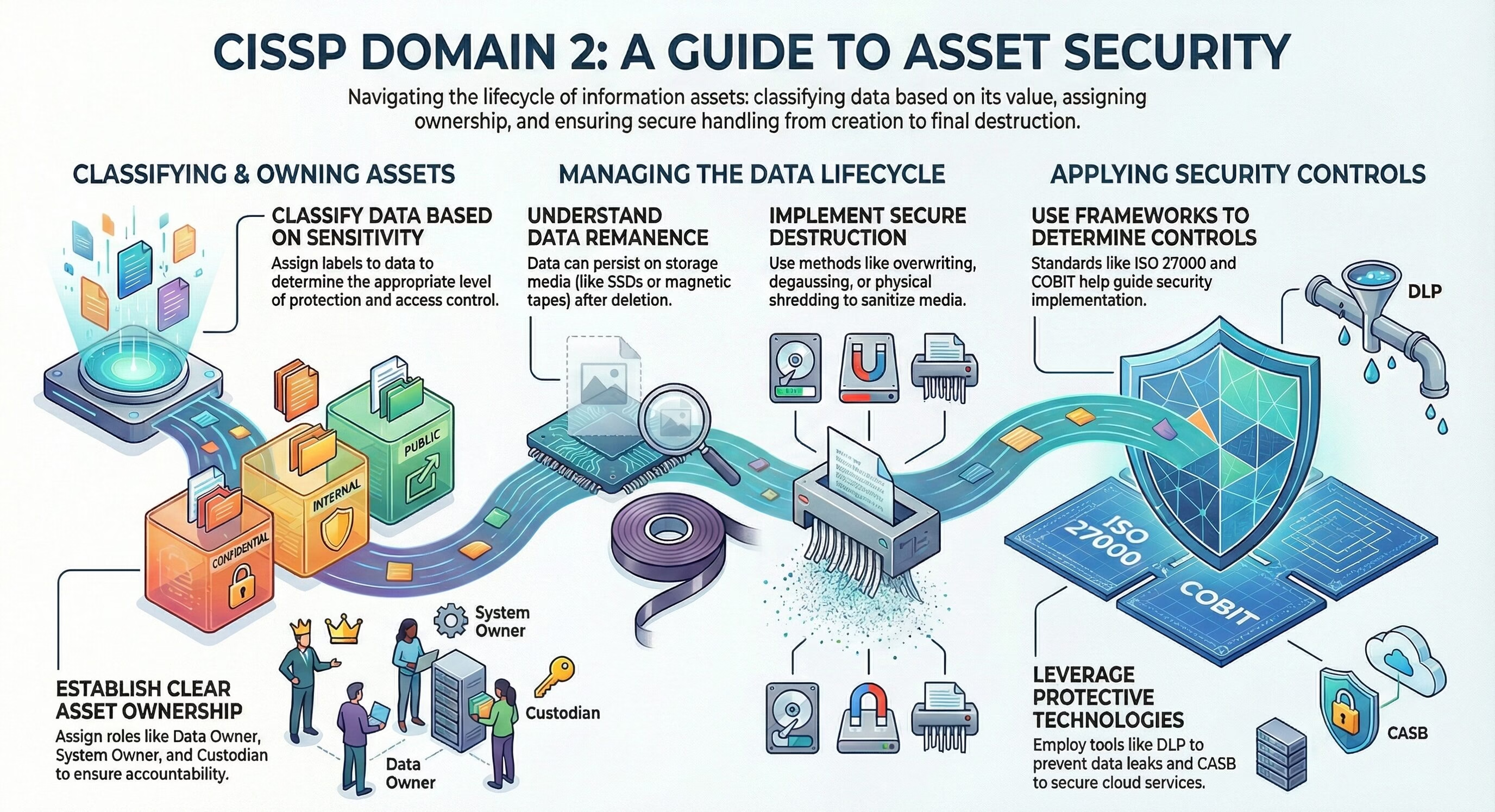
- Classifying Data: This objective explains the concepts and methods of data classification, such as labels, clearances, formal access approval, and need to know. It also discusses the security compartments and the data controllers and data processors roles.
- Ownership and Inventory: This objective covers the importance of identifying and managing the assets of an organization, such as data, systems, and hardware. It also describes the roles and responsibilities of business or mission owners, data owners, system owners, custodians, and users.
- Memory and Remanence: This objective explores the different types of memory and storage devices, such as RAM, ROM, flash memory, SSDs, and magnetic media. It also examines the data remanence properties of each type and the methods to securely erase or destroy data.
- Data Destruction: This objective reviews the various techniques and tools for sanitizing and disposing of media, such as overwriting, degaussing, shredding, and incineration. It also discusses the factors and policies that affect the data retention and destruction decisions.
- Determining Data Security Controls: This objective introduces the standards and frameworks that can help organizations implement and evaluate data security controls, such as PCI-DSS, OCTAVE®, ISO 27000 series, COBIT, and ITIL®. It also explains the concepts of certification and accreditation, baselines, scoping, and tailoring.
Unique Terms and Definitions from Domain 2: Asset Security
- ATA Secure Erase: A command that securely erases all data on an SSD by resetting all blocks to the factory default state and generating a new encryption key.
- Data controller: A person or entity that creates and manages sensitive data within an organization.
- Data processor: A person or entity that manages data on behalf of a data controller.
- Data classification: The process of assigning labels to data based on its sensitivity and value to an organization. Data classification helps to determine the appropriate level of protection and access control for data
- Data remanence: The persistence of data on a storage device after non-invasive attempts to delete it. Data remanence can pose a security risk if sensitive data is recovered by unauthorized parties
- Scoping: The process of determining which portions of a standard will be employed by an organization. Scoping allows an organization to exclude or modify certain controls that are not applicable or feasible for its environment
- Tailoring: The process of customizing a standard for an organization. Tailoring involves selecting, supplementing, and adjusting controls based on the organization’s specific needs and risk profile
- Solid State Drive (SSD): A type of storage device that uses flash memory and DRAM to store data. SSDs have no moving parts and offer faster performance, lower power consumption, and higher reliability than traditional hard disk drives. However, SSDs also have different data remanence properties and require special methods for secure data erasure
- Digital Rights Management (DRM): A set of technologies and techniques that restrict the use of copyrighted materials and other forms of intellectual property. DRM aims to prevent unauthorized copying, distribution, modification, or access of protected content. DRM may use encryption, watermarking, product keys, region locking, and other mechanisms to enforce restrictions
- Cloud Access Security Broker (CASB): A software tool or service that acts as an intermediary between cloud service consumers and cloud service providers. CASBs provide security policy enforcement, visibility, data security, threat protection, and compliance for cloud-based resources. CASBs can help organizations manage the risks and challenges of using cloud service
- Data Loss Prevention (DLP): A class of solutions that aim to detect or prevent data from leaving an organization in an unauthorized manner. DLP can help protect sensitive data from theft, leakage, or exposure due to malicious or negligent actions. DLP may use network-oriented, endpoint-oriented, or data-oriented approaches to monitor and control data flows
Multiple Choice Questions quiz
|
Flashcard quiz
|