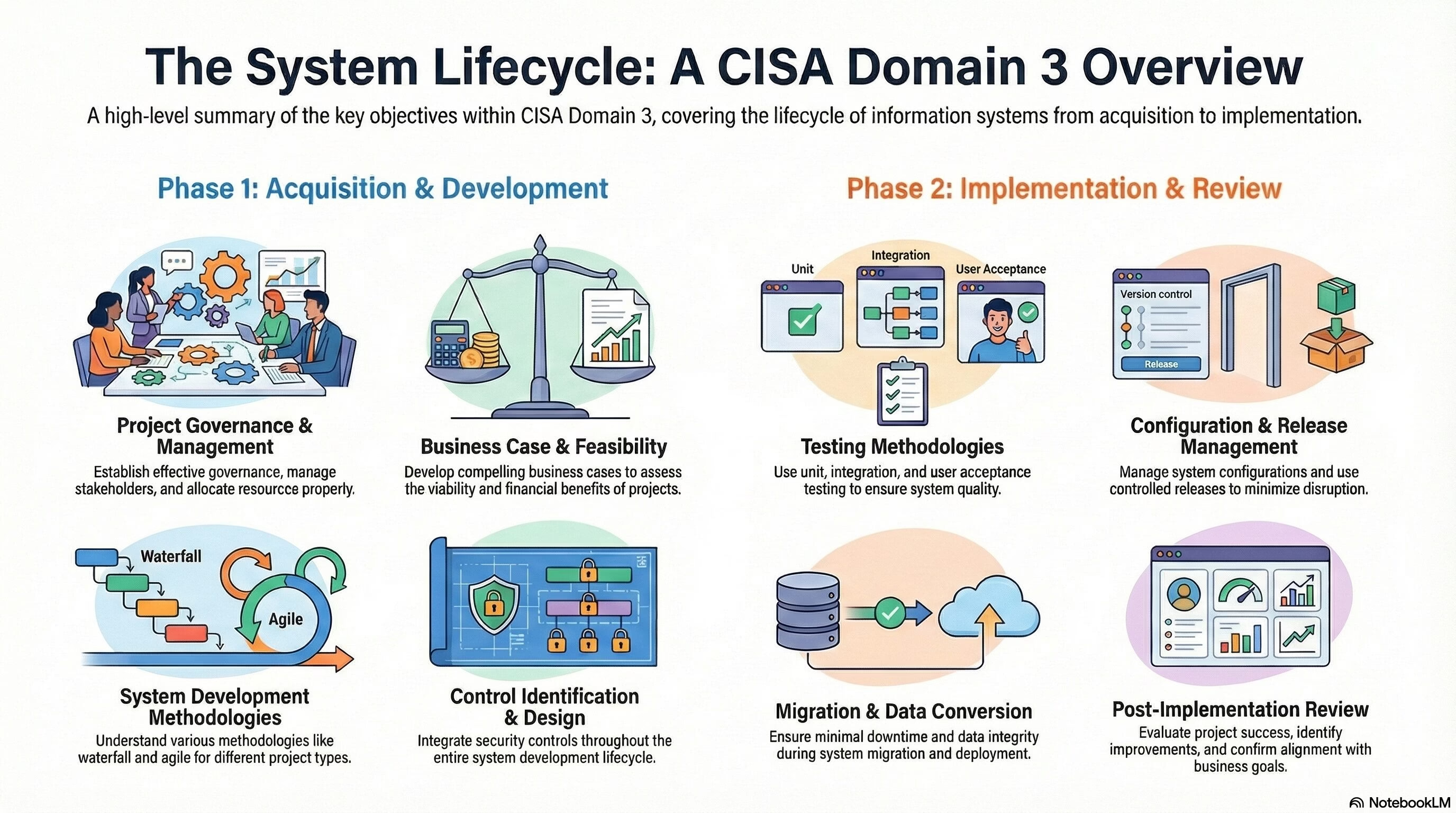
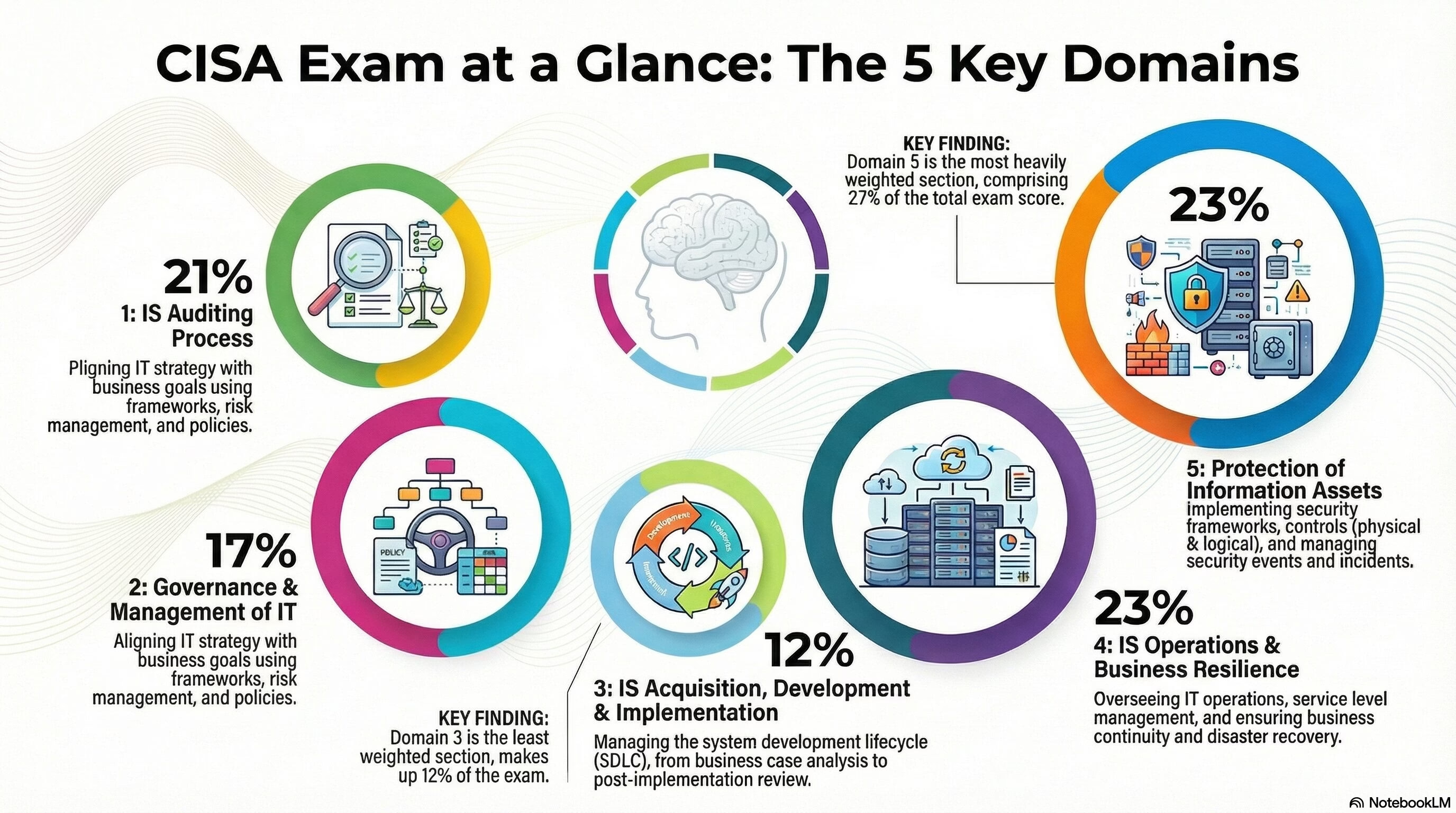
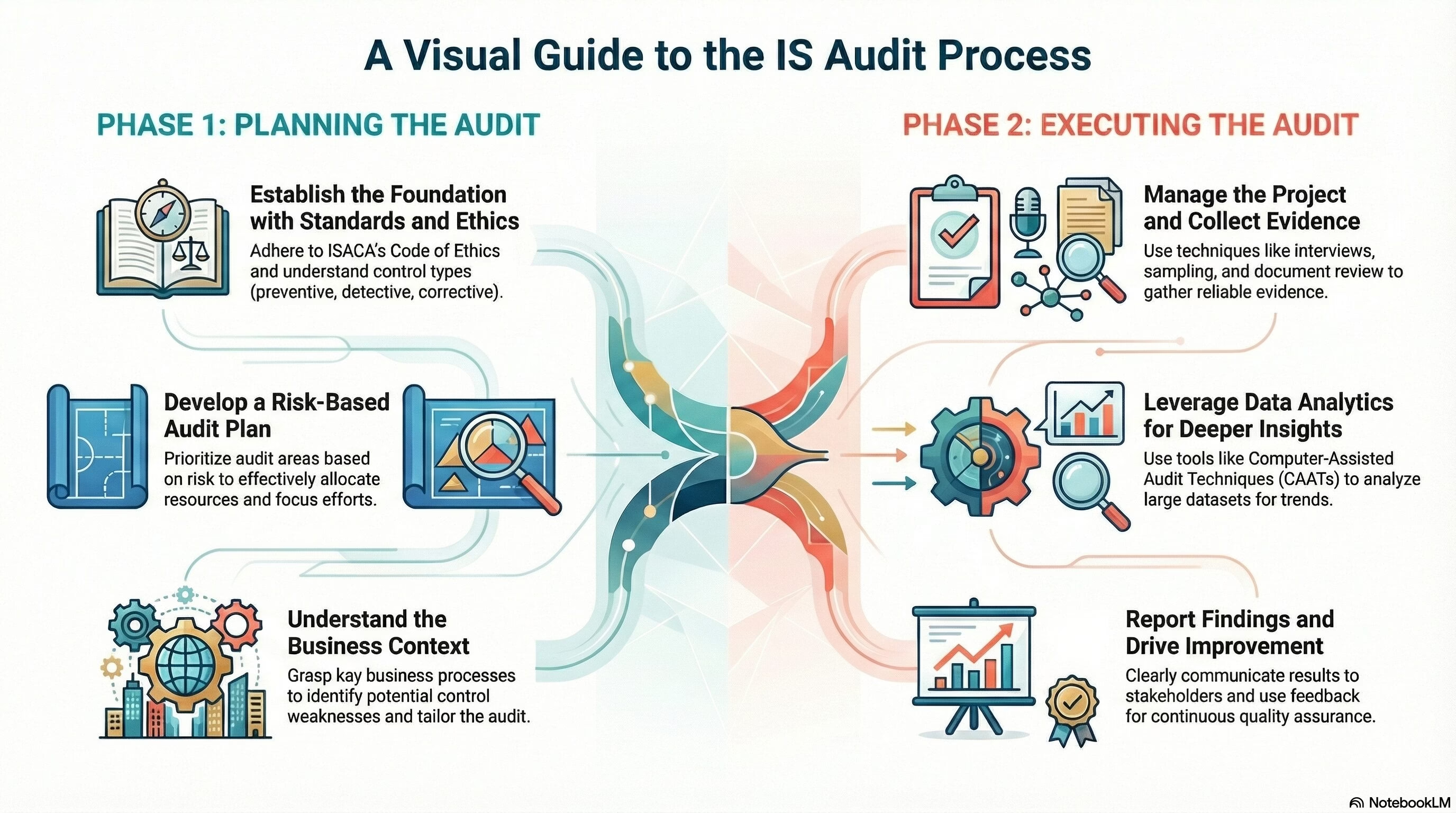
The Domain 3: Information Systems Acquisition, Development & Implementation of CISA exam holds a total weightage of 12% in the exam. Domain 3: Information Systems Acquisition, Development & Implementation of the CISA exam focuses on the lifecycle of information systems,… Read More "CISA Domain 3: Information Systems Acquisition, Development & Implementation"