Short-Answer Quiz Instructions: Answer the following questions in 2-3 sentences each. Your answers should be based on the concepts presented in the study materials. ——————————————————————————– Answer Key ——————————————————————————– Essay Questions Instructions: Prepare a detailed, essay-format response for each of the… Read More "Security+ Domains 1-5 Study Guide"
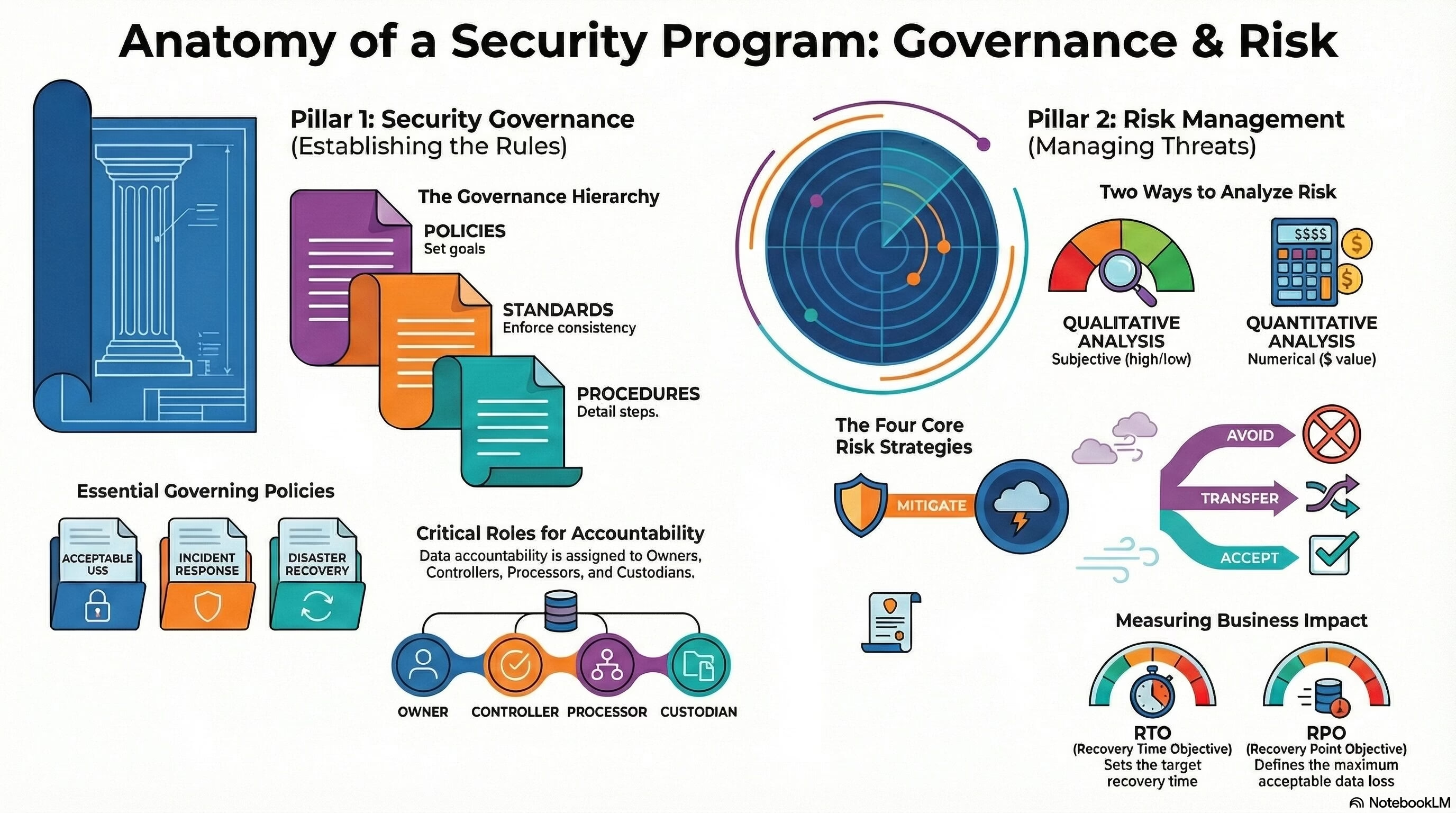
Security+ Domain 5 – Security Program Management and Oversight
Security+ Domain 5 – Security Program Management and Oversight (20% weightage) Key terms and definitions from this objective are given below: 5.1 Summarize elements of effective security governance. Policies: Standards: Procedures: External Considerations: Monitoring and Revision: Ongoing processes of reviewing,… Read More "Security+ Domain 5 – Security Program Management and Oversight"
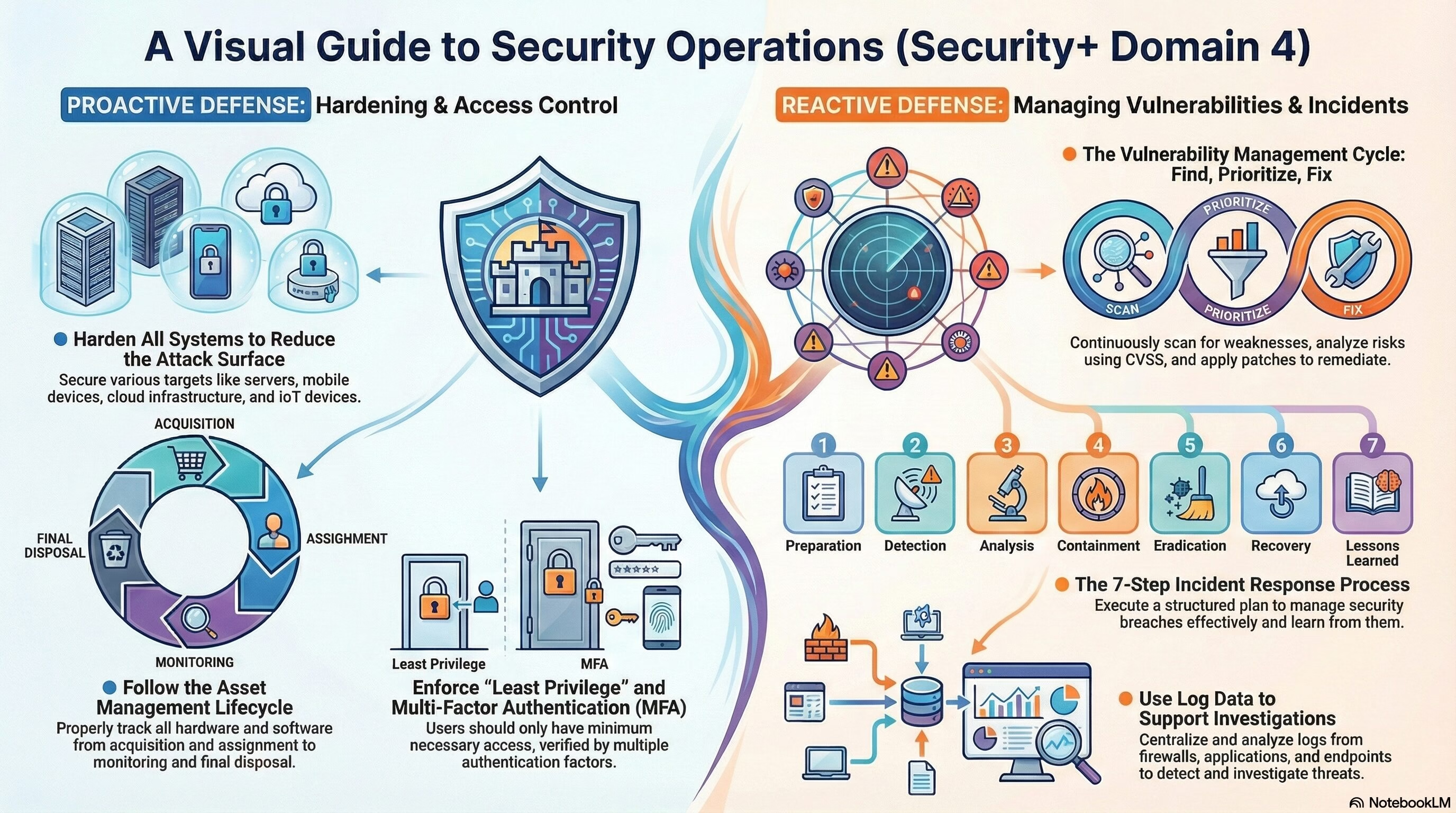
Security+ Domain 4 – Security Operations
Security+ Domain 4 – Security Operations (28% weightage) Key terms and definitions from this objective are given below: 4.1 Given a scenario, apply common security techniques to computing resources. Secure Baselines: Hardening Targets: Wireless Devices: Installation Considerations: Mobile Solutions: Mobile… Read More "Security+ Domain 4 – Security Operations"
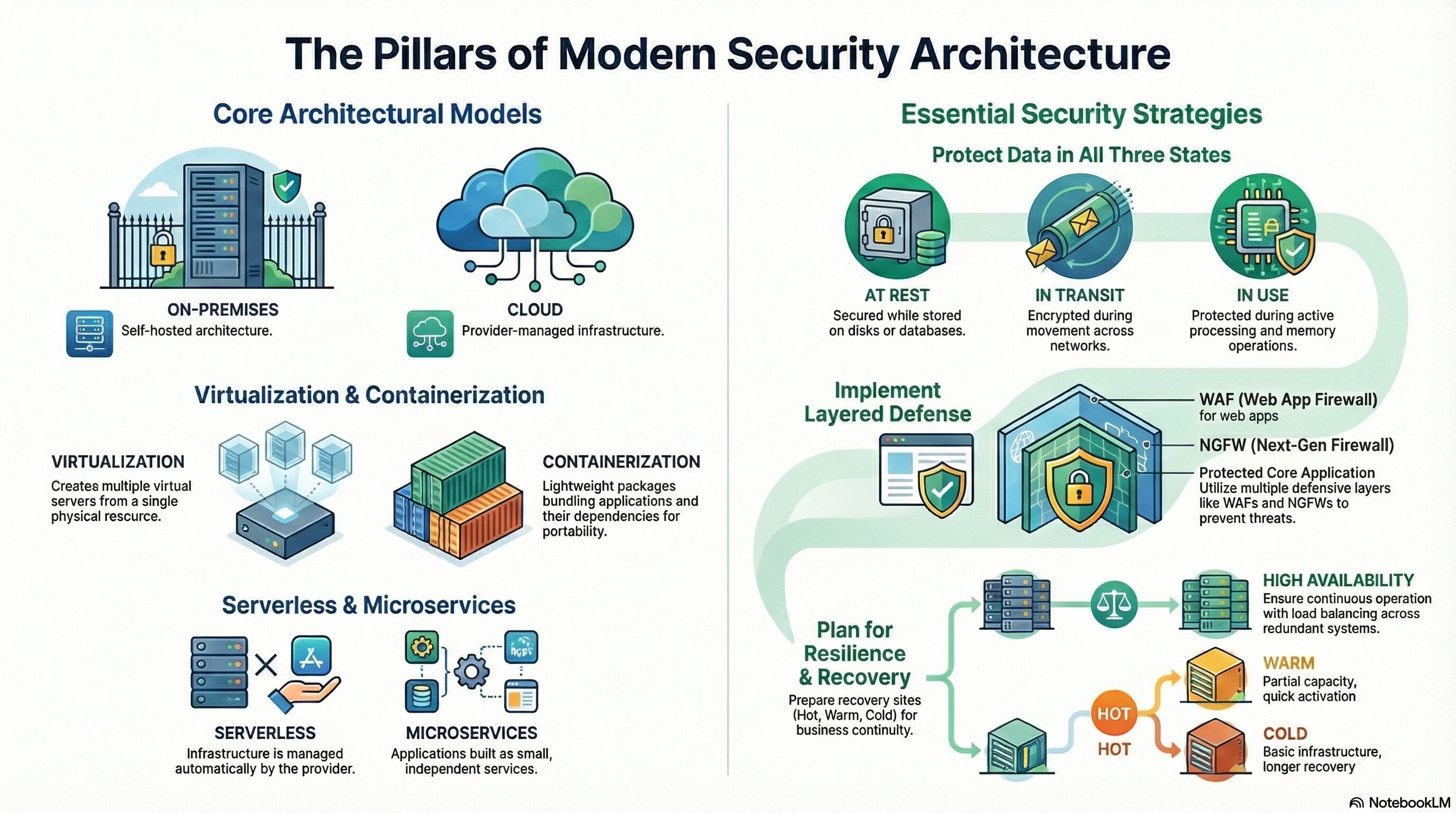
Security+ Domain 3 – Security Architecture
Security+ Domain 3 – Security Architecture (18% weightage) Key terms and definitions from this objective are given below: 3.1 Compare and contrast security implications of different architecture models. Architecture and Infrastructure Concepts: Cloud: Infrastructure as Code (IaC): IaC is a practice… Read More "Security+ Domain 3 – Security Architecture"
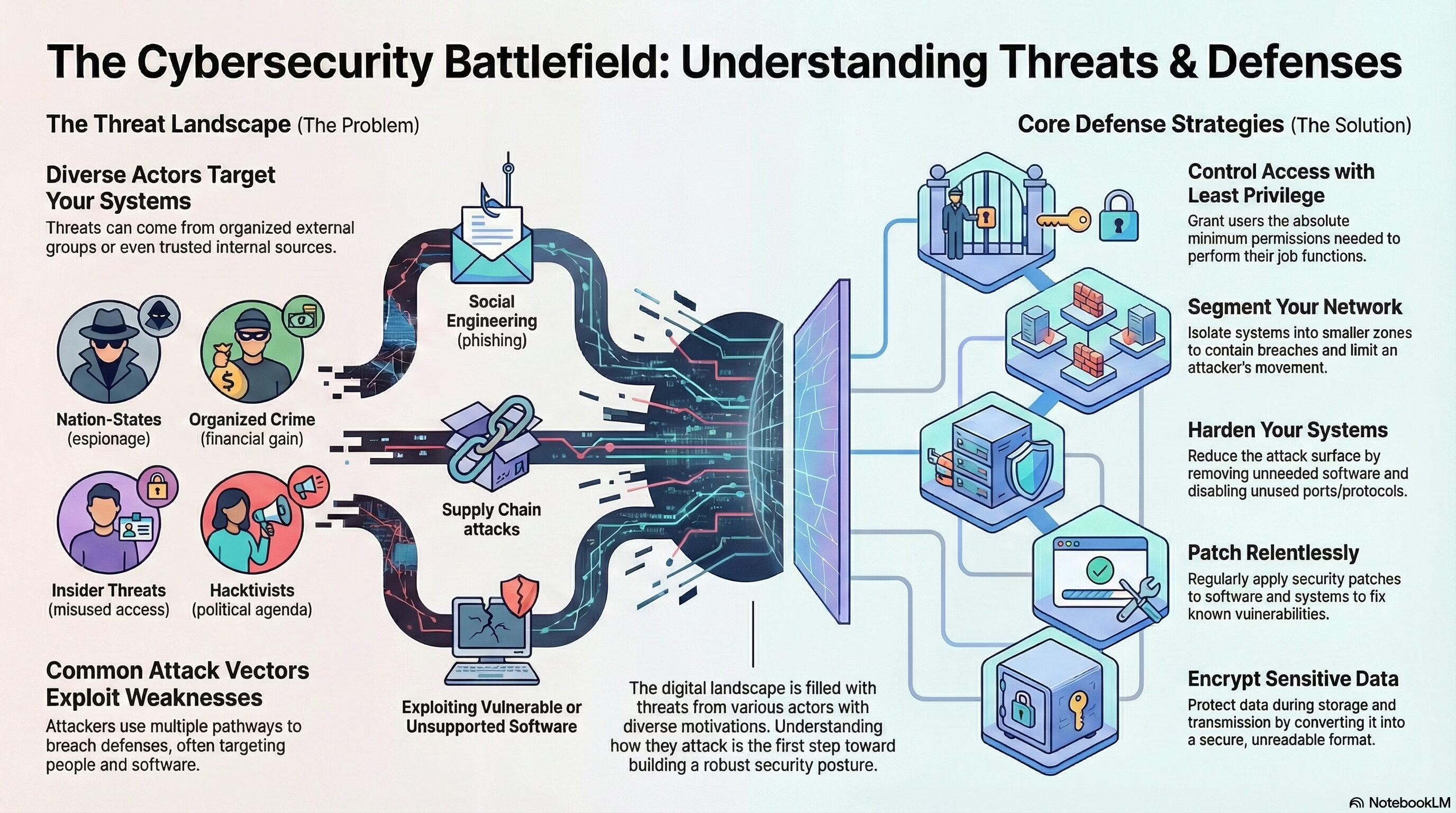
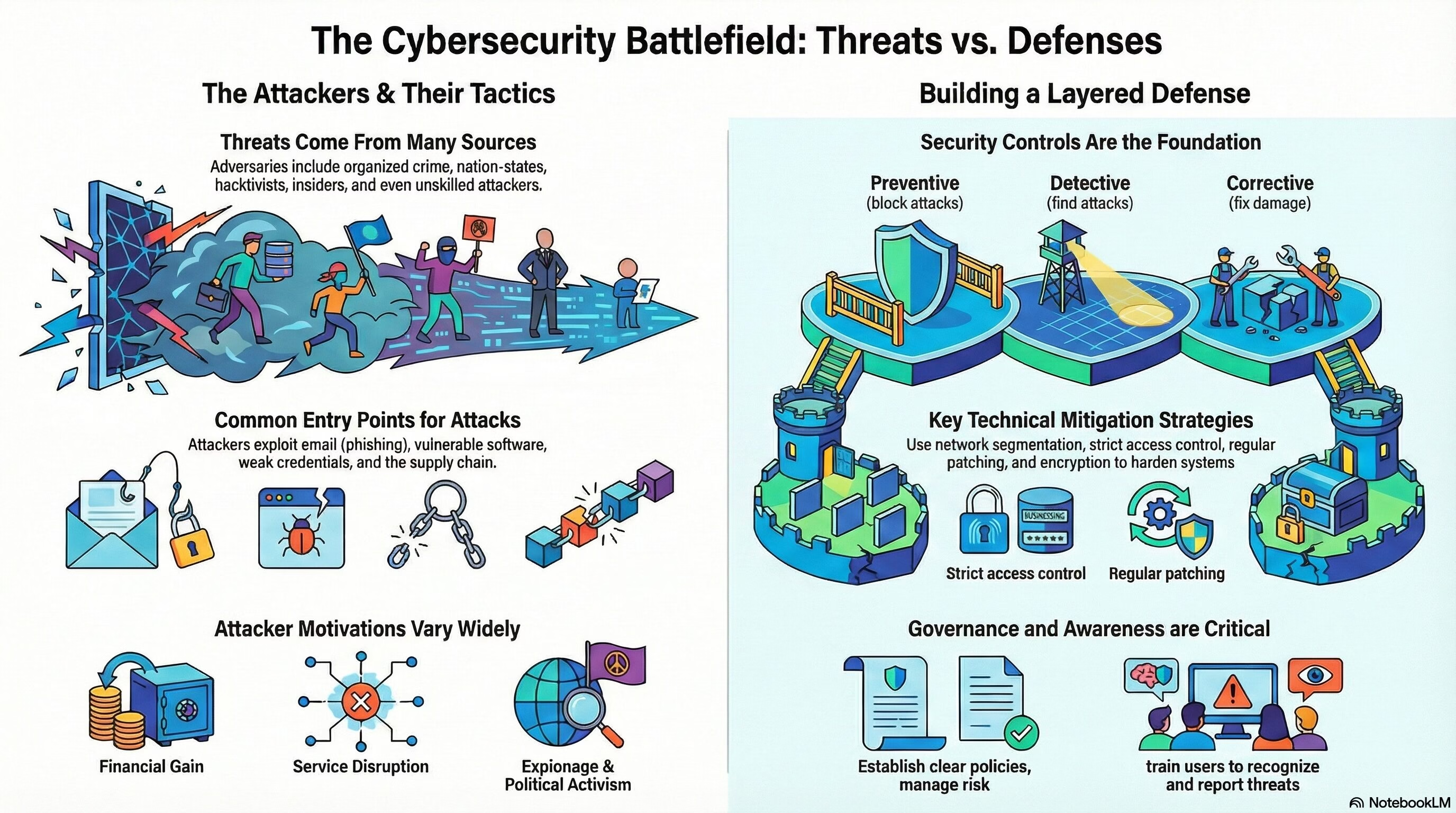
Security+ Domain 2 – Threats, Vulnerabilities, and Mitigations
Security+ Domain 2 – Threats, Vulnerabilities, and Mitigations (22% weightage) Key terms and definitions from this objective are given below: 2.1 Compare and contrast common threat actors and motivations. Threat Actors: Attributes of Actors: Motivations: 2.2 Explain common threat vectors… Read More "Security+ Domain 2 – Threats, Vulnerabilities, and Mitigations"
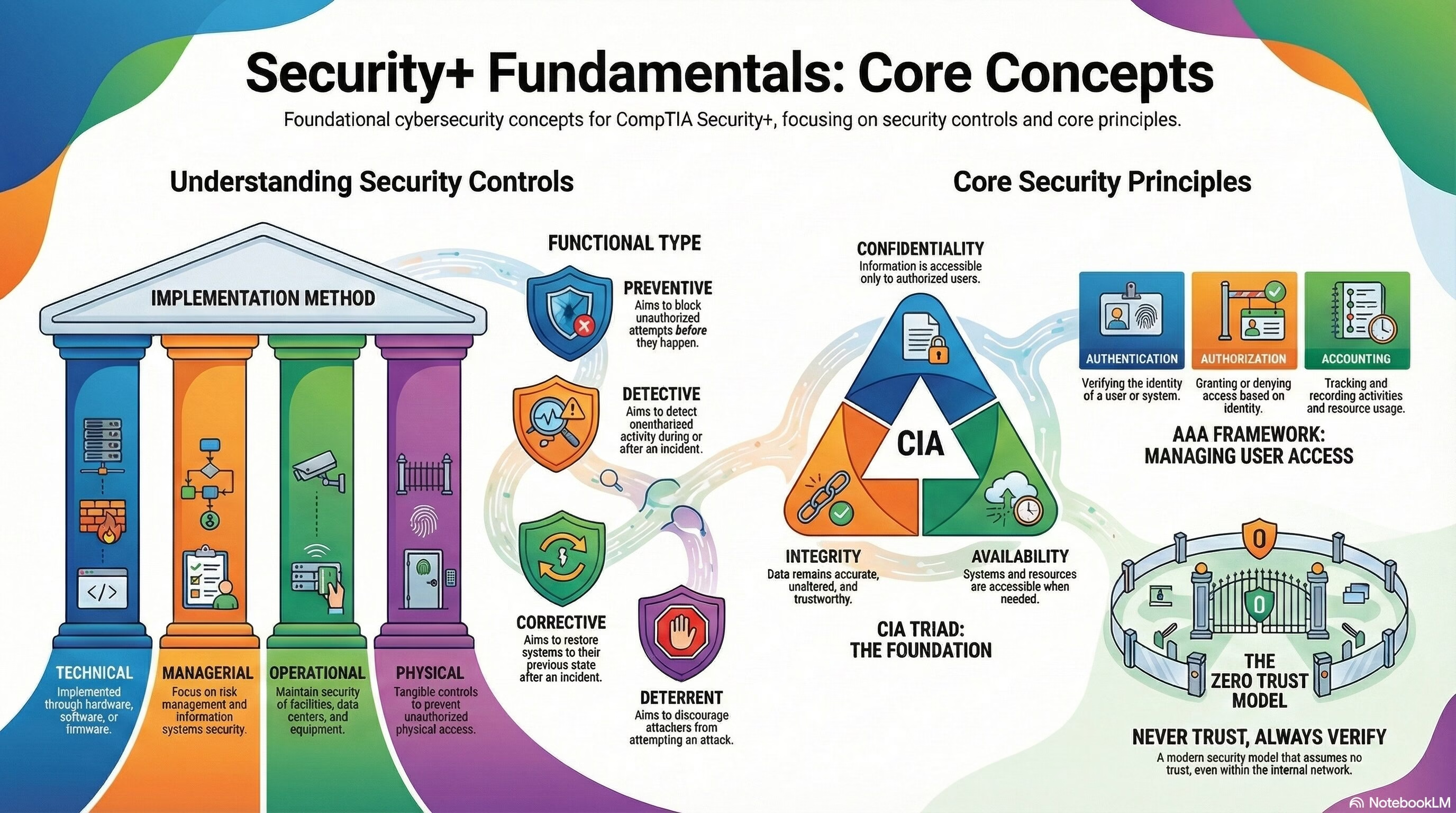
Security+ Domain 1 – General Security Concepts
Security+ Domain 1 – General Security Concepts (12% weightage) Key terms and definitions from this objective are given below: 1.1 Compare and contrast various types of security controls. Categories: Control Types: 1.2 Summarize fundamental security concepts. Confidentiality, Integrity, and Availability… Read More "Security+ Domain 1 – General Security Concepts"
CompTIA Security+ (SY0-701) Exam and Certification
Introduction The new CompTIA Security+ SY0-701 is hot off the press and represents the latest and greatest on offering cybersecurity skills in the form of current threats, automation, zero trust, IOT, risk-and much more. Once certified, you will understand the… Read More "CompTIA Security+ (SY0-701) Exam and Certification"
