Table of Contents
Security+ Domain 3 – Security Architecture (18% weightage)
Key terms and definitions from this objective are given below:
3.1 Compare and contrast security implications of different architecture models.
Architecture and Infrastructure Concepts:
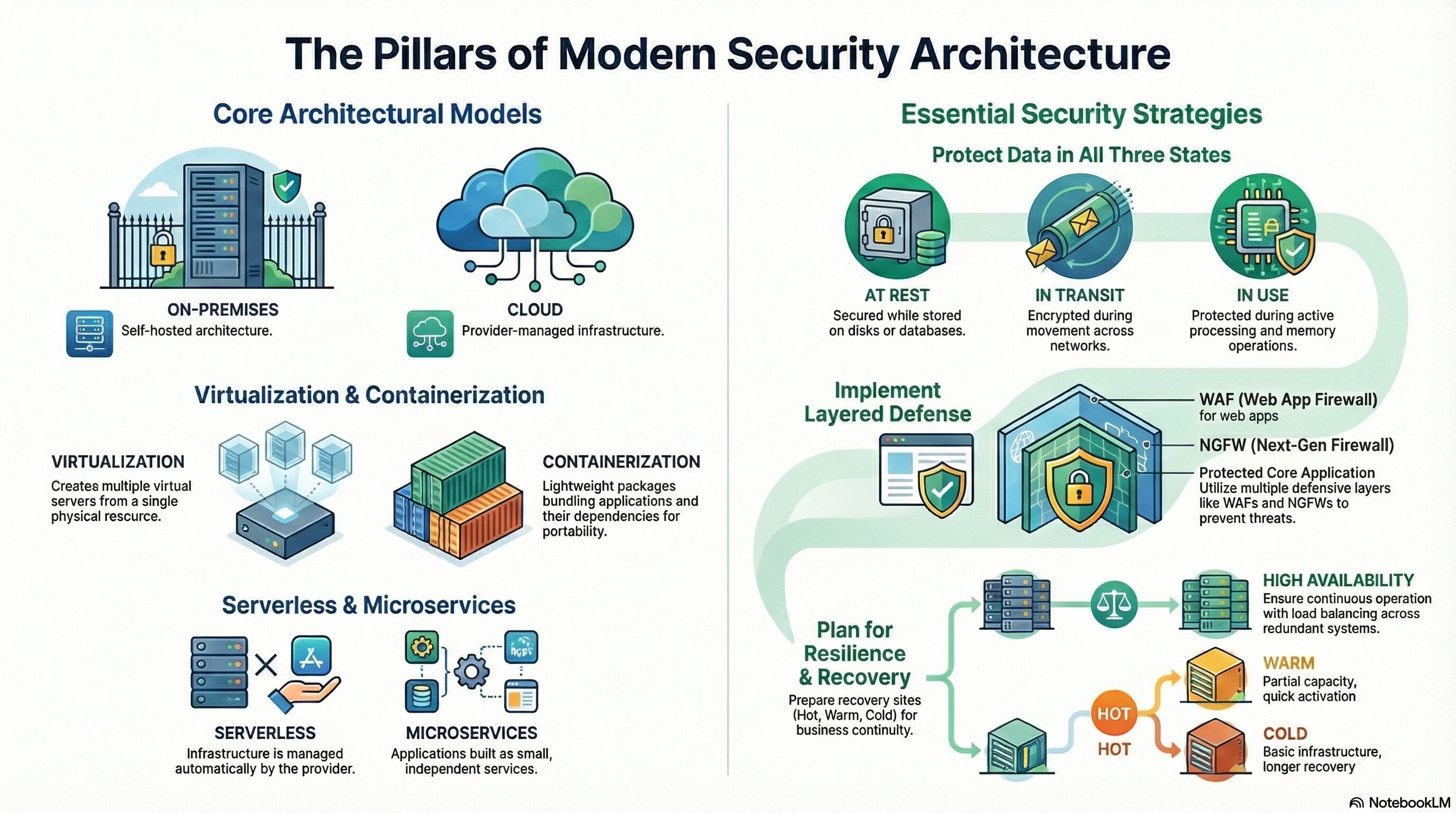
Cloud:
- Responsibility Matrix: A document outlining the division of responsibilities between a cloud service provider (CSP) and its customers. It defines which security and management tasks are handled by each party.
- Hybrid Considerations: Hybrid cloud refers to an IT architecture that incorporates some degree of workload portability, orchestration, and management across 2 or more environments, which can include on-premises data centers, private clouds, and public clouds.
- Third-Party Vendors: External organizations or service providers that offer products or services to complement or enhance the capabilities of a primary service or system.
Infrastructure as Code (IaC): IaC is a practice in which infrastructure is provisioned and managed using code and software development techniques. It enables the automation of infrastructure deployment and configuration.
Serverless: Serverless computing is a cloud computing execution model where the cloud provider manages the infrastructure, and users only need to worry about writing and deploying code. The term “serverless” does not mean there are no servers; it means the user doesn’t need to provision or manage them.
Microservices: Microservices is an architectural style that structures an application as a collection of small, independently deployable services. Each service is designed to perform a specific business function and can communicate with other services through well-defined APIs.
Network Infrastructure:
- Physical Isolation: Physically separating networks or components to enhance security by reducing the risk of unauthorized access.
- Air-Gapped: An air-gapped network is physically isolated from unsecured networks, ensuring there is no direct or indirect connection to the internet or other networks.
- Logical Segmentation: Dividing a network into segments based on logical criteria, such as departments or functions, to control and secure the flow of traffic.
- Software-Defined Networking (SDN): SDN is an approach to networking that uses software-based controllers or application programming interfaces (APIs) to direct traffic on the network and communicate with the underlying hardware infrastructure.
On-Premises: On-premises refers to the deployment of software, infrastructure, or services within an organization’s physical location or data center, rather than in a cloud environment.
Centralized vs. Decentralized: Describes the distribution of authority and control within an organization. Centralized structures have decision-making concentrated at a single point, while decentralized structures distribute decision-making across various levels or units.
Containerization: Containerization is a lightweight form of virtualization that encapsulates an application and its dependencies into a standardized unit called a container. Containers provide consistency across various development, testing, and deployment environments.
Virtualization: Virtualization involves creating a virtual version of a computing resource, such as a server, operating system, or network, to optimize resource utilization and increase flexibility.
IoT (Internet of Things):IoT refers to the network of interconnected devices embedded with sensors, software, and other technologies to exchange data and enable communication between devices.
Industrial Control Systems (ICS) / Supervisory Control and Data Acquisition (SCADA): ICS and SCADA are control systems used in industrial settings to monitor and control processes. ICS focuses on automation, while SCADA involves the collection and analysis of real-time data.
Real-Time Operating System (RTOS): An operating system designed to meet the requirements of real-time systems, ensuring that tasks are performed within specified time constraints.
Embedded Systems:Embedded systems are specialized computing systems integrated into other devices or systems to perform specific functions.
High Availability: High availability refers to the design and implementation of systems that ensure a high level of operational performance, often achieved through redundancy and failover mechanisms.
Considerations:
Availability: Availability is a measure of the uptime and accessibility of a system or service, indicating how reliably it can be accessed by users.
Resilience: Resilience is the ability of a system to recover quickly from disruptions, such as hardware failures, network outages, or security incidents.
Cost: Cost considerations involve evaluating the financial implications of implementing and maintaining an IT infrastructure or solution.
Responsiveness: Responsiveness refers to how quickly a system or application can respond to user inputs or external events.
Scalability: Scalability is the ability of a system to handle an increasing amount of load or demand by adding resources or capacity.
Ease of Deployment: Ease of deployment assesses how easily a system, application, or update can be rolled out and integrated into an existing environment.
Risk Transference: Risk transference involves shifting the burden of potential risks and liabilities to a third party, often through insurance or outsourcing.
Ease of Recovery: Ease of recovery refers to how quickly and effectively a system or service can be restored after a disruption or failure.
Patch Availability: Patch availability is the timely availability of software updates and security patches to address vulnerabilities and enhance system security.
Inability to Patch: Describes situations where systems or software cannot be easily updated or patched, potentially leaving them vulnerable to security threats.
Power:Power considerations involve assessing the electrical requirements and availability necessary for the proper functioning of IT infrastructure.
Compute: Compute refers to the processing power and resources required to perform computational tasks in an IT environment.
3.2 Given a scenario, apply security principles to secure enterprise infrastructure.
Infrastructure Considerations:
Device Placement: Determining the physical or logical location of devices within a network to optimize performance, security, and resource utilization. Security Zones: Security zones involve segregating network resources and assets based on security requirements. Each zone may have different access controls, policies, and security measures. Attack Surface: The attack surface refers to the sum of all possible points where an unauthorized user or malicious software could try to enter or extract data from an environment. Connectivity: Connectivity refers to the extent and reliability of network connections between devices, systems, or networks. Failure Modes:
- Fail-Open: In the event of a failure, the device allows traffic to pass through, potentially exposing the network.
- Fail-Closed: In the event of a failure, the device blocks traffic, preventing unauthorized access but potentially causing service disruption.
Device Attribute:
- Active vs. Passive: Active devices actively modify or manipulate network traffic, while passive devices monitor and analyze traffic without making changes.
- Inline vs. Tap/Monitor: Inline devices are directly in the data path and can actively intercept and modify traffic, while tap/monitor devices passively monitor traffic without being in the direct data path.
Network Appliances:
- Jump Server: A jump server, or jump host, is an intermediary server used to access and manage devices within a secure network.
- Proxy Server: A proxy server acts as an intermediary between clients and servers, forwarding requests and responses to enhance security, privacy, and performance.
- Intrusion Prevention System (IPS)/Intrusion Detection System (IDS):
- IPS A security appliance that actively monitors and analyzes network or system activities to detect and prevent malicious activities.
- IDS A security appliance that passively monitors network or system activities and alerts on potential security threats.
- Load Balancer: A load balancer distributes incoming network traffic across multiple servers to ensure optimal resource utilization and prevent overload on individual servers.
- Sensors: Sensors are devices that collect data from the environment, such as network traffic, to detect and respond to security incidents.
Port Security:
- 802.1X: A port-based authentication protocol that provides an additional layer of security for network access, requiring authentication before granting access.
- Extensible Authentication Protocol (EAP): EAP is a framework that various other authentication protocols use to facilitate secure communication.
Firewall Types:
- Web Application Firewall (WAF): A firewall specifically designed to protect web applications from common security threats and vulnerabilities.
- Unified Threat Management (UTM): A comprehensive security solution that integrates multiple security features, such as firewall, antivirus, intrusion detection, and content filtering, into a single platform.
- Next-Generation Firewall (NGFW): A firewall that combines traditional firewall capabilities with advanced features such as application-layer filtering and intrusion prevention.
- Layer 4/Layer 7: Layer 4 firewalls operate at the transport layer, filtering traffic based on source and destination IP addresses and ports. Layer 7 firewalls operate at the application layer, allowing for more granular control based on application-specific characteristics.
Secure Communication/Access:
- Virtual Private Network (VPN): A VPN creates a secure, encrypted connection over a less secure network, such as the internet, allowing remote users to access a private network securely.
- Remote Access: The ability for users to connect to a network or system from a remote location, typically through secure authentication methods.
- Tunneling:
- Transport Layer Security (TLS): A protocol that ensures privacy between communicating applications and users on the internet by encrypting data during transmission.
- Internet Protocol Security (IPSec): A suite of protocols that secure internet protocol communications by authenticating and encrypting each packet of data during transmission.
- Software-Defined Wide Area Network (SD-WAN): SD-WAN is an approach to designing and deploying wide area networks that uses software-defined networking to determine the most effective way to route traffic to remote locations.
- Secure Access Service Edge (SASE): SASE is an integrated security framework that combines network security functions with WAN capabilities to support the dynamic, secure access needs of organizations.
Selection of Effective Controls:
- The process of choosing and implementing security controls based on an organization’s risk assessment, security policies, and specific requirements to protect against potential threats and vulnerabilities. Effective controls contribute to a robust security posture and resilience against cyber threats.
3.3 Compare and contrast concepts and strategies to protect data.
Data Types:
- Regulated: Regulated data refers to information that is subject to specific legal regulations and compliance requirements. Examples include personally identifiable information (PII), healthcare data (HIPAA), and financial data (PCI DSS).
- Trade Secret: Trade secrets are confidential business information that provides a competitive advantage. They are protected by law, and unauthorized disclosure or use is considered an infringement.
- Intellectual Property: Intellectual property includes creations of the mind, such as inventions, literary and artistic works, designs, symbols, names, and images used in commerce.
- Legal Information: Legal information refers to data related to legal matters, such as contracts, court records, and other documents containing legally binding information.
- Financial Information: Financial information encompasses data related to financial transactions, accounts, budgets, and other monetary aspects of an individual or organization.
Human- and Non-Human-Readable:
- Human-Readable: Information that can be easily interpreted by humans without the need for additional processing or translation.
- Non-Human-Readable: Information formatted or encoded in a way that is not easily understood by humans, often requiring specialized tools or algorithms for interpretation.
Data Classifications:
- Sensitive: Sensitive data includes information that, if disclosed, could result in harm to individuals or the organization. It requires heightened protection to prevent unauthorized access.
- Confidential: Confidential data is information that requires protection to prevent unauthorized disclosure, but its impact may be less severe than that of sensitive data.
- Public: Public data is information that is meant for unrestricted access and can be freely shared with the public.
- Restricted: Restricted data is subject to limitations on access, sharing, or distribution due to legal, contractual, or organizational policies.
- Private: Private data refers to information intended for a limited audience and is not publicly disclosed. It is shared within a defined group or organization.
- Critical: Critical data is information deemed crucial to the functioning and survival of an organization. Its compromise could have severe consequences.
General Data Considerations:
Data States:
- Data at Rest: Data at rest is information that is stored on a physical or digital medium and is not currently in use.
- Data in Transit: Data in transit is information being transmitted over a network or communication channel.
- Data in Use: Data in use is information actively being processed or accessed by a system or user.
Data Sovereignty: Data sovereignty refers to the concept that data is subject to the laws and regulations of the country or region in which it is located.
Geolocation: Geolocation involves identifying and tracking the physical location of devices or individuals using data from various sources, such as GPS or IP addresses.
Methods to Secure Data:
- Geographic Restrictions: Geographic restrictions involve limiting access to data based on the physical location of users or systems to enhance security and compliance.
- Encryption: Encryption is the process of converting plaintext into ciphertext using algorithms and cryptographic keys to protect data confidentiality.
- Hashing: Hashing is a one-way function that generates a fixed-size string of characters (hash) from input data. It is commonly used for data integrity verification.
- Masking: Data masking involves replacing sensitive information with fictional or pseudonymous data to protect privacy during testing or non-production use.
- Tokenization: Tokenization replaces sensitive data with a unique identifier (token) that has no intrinsic value and is used to reference the original data in a secure manner.
- Obfuscation: Obfuscation involves deliberately making data unclear or difficult to interpret, often to protect sensitive information.
- Segmentation: Segmentation involves dividing a network into isolated segments to restrict the lateral movement of attackers and contain potential security breaches.
- Permission Restrictions: Permission restrictions involve assigning specific access rights or privileges to users or systems based on their roles or responsibilities to control data access and manipulation.
3.4 Explain the importance of resilience and recovery in security architecture.
High Availability:
Load Balancing vs. Clustering:
- Load Balancing: Load balancing is the distribution of network traffic across multiple servers to ensure no single server becomes overwhelmed, optimizing resource utilization and preventing service degradation.
- Clustering: Clustering involves connecting multiple servers to work together as a single system, providing redundancy and fault tolerance. If one server fails, another in the cluster can take over.
Site Considerations:
- Hot: A hot site is a fully operational data center with up-to-date equipment, data, and applications. It is ready to take over operations immediately after a primary site failure.
- Cold: A cold site is a location equipped with necessary infrastructure, but lacks up-to-date equipment, data, and applications. It requires manual intervention and setup in the event of a primary site failure.
- Warm: A warm site is a compromise between hot and cold sites. It has some infrastructure in place and may have partial data and applications, requiring a quicker setup compared to a cold site.
- Geographic Dispersion: Geographic dispersion involves spreading critical infrastructure, such as data centers or servers, across multiple locations to mitigate the impact of localized disasters or disruptions.
- Platform Diversity: Platform diversity refers to the use of different hardware, software, or operating systems to reduce the risk of a single point of failure and enhance overall system resilience.
- Multi-Cloud Systems: Multi-cloud systems involve utilizing services or resources from multiple cloud service providers. This approach enhances flexibility, redundancy, and reduces dependence on a single provider.
- Continuity of Operations: Continuity of operations (COOP) ensures that essential functions and services can continue in the face of disruptive events, such as natural disasters, cyber attacks, or equipment failures.
Capacity Planning:
- People: Capacity planning for people involves ensuring that the necessary skilled personnel are available to manage and support IT systems during normal operations and in emergencies.
- Technology: Capacity planning for technology involves ensuring that hardware, software, and network resources are sufficient to handle current and future workloads.
- Infrastructure: Capacity planning for infrastructure involves assessing and provisioning the necessary physical and virtual resources to support business operations and prevent performance bottlenecks.
Testing:
- Tabletop Exercises: Tabletop exercises are discussion-based simulations where key personnel meet to discuss their roles and responses to various simulated scenarios.
- Failover: Failover testing involves intentionally triggering a failure to assess the system’s ability to switch to a backup or secondary system seamlessly.
- Simulation: Simulation testing recreates real-world scenarios to evaluate the performance and effectiveness of a system’s response under controlled conditions.
- Parallel Processing: Parallel processing testing involves running simultaneous tasks or processes to assess the system’s ability to handle multiple operations concurrently.
Backups:
Onsite/Offsite:
- Onsite: Onsite backups are copies of data stored in the same location as the primary data source, providing quick access but vulnerable to local disasters.
- Offsite: Offsite backups are copies of data stored in a separate location from the primary data source, reducing the risk of data loss in case of local disasters.
Frequency: Backup frequency determines how often data is copied or archived to ensure that changes and updates are captured regularly.
Encryption: Backup encryption involves securing backup data using encryption algorithms to protect it from unauthorized access or tampering.
Snapshots: Snapshots are point-in-time copies of data that capture the state of a system or dataset at a specific moment.
Recovery: Recovery refers to the process of restoring data and systems to their operational state after a failure or data loss event.
Replication: Replication involves creating and maintaining duplicate copies of data or systems in real-time to ensure data availability and resilience.
Journaling: Journaling records changes or modifications made to data, providing a log that can be used to recover data to a specific point in time.
Power:
Generators: Generators are devices that convert mechanical energy into electrical energy, providing backup power during electrical outages.
Uninterruptible Power Supply (UPS): A UPS is a device that provides short-term battery power backup during electrical outages, preventing data loss or system downtime.