Table of Contents
Security+ Domain 2 – Threats, Vulnerabilities, and Mitigations (22% weightage)
Key terms and definitions from this objective are given below:
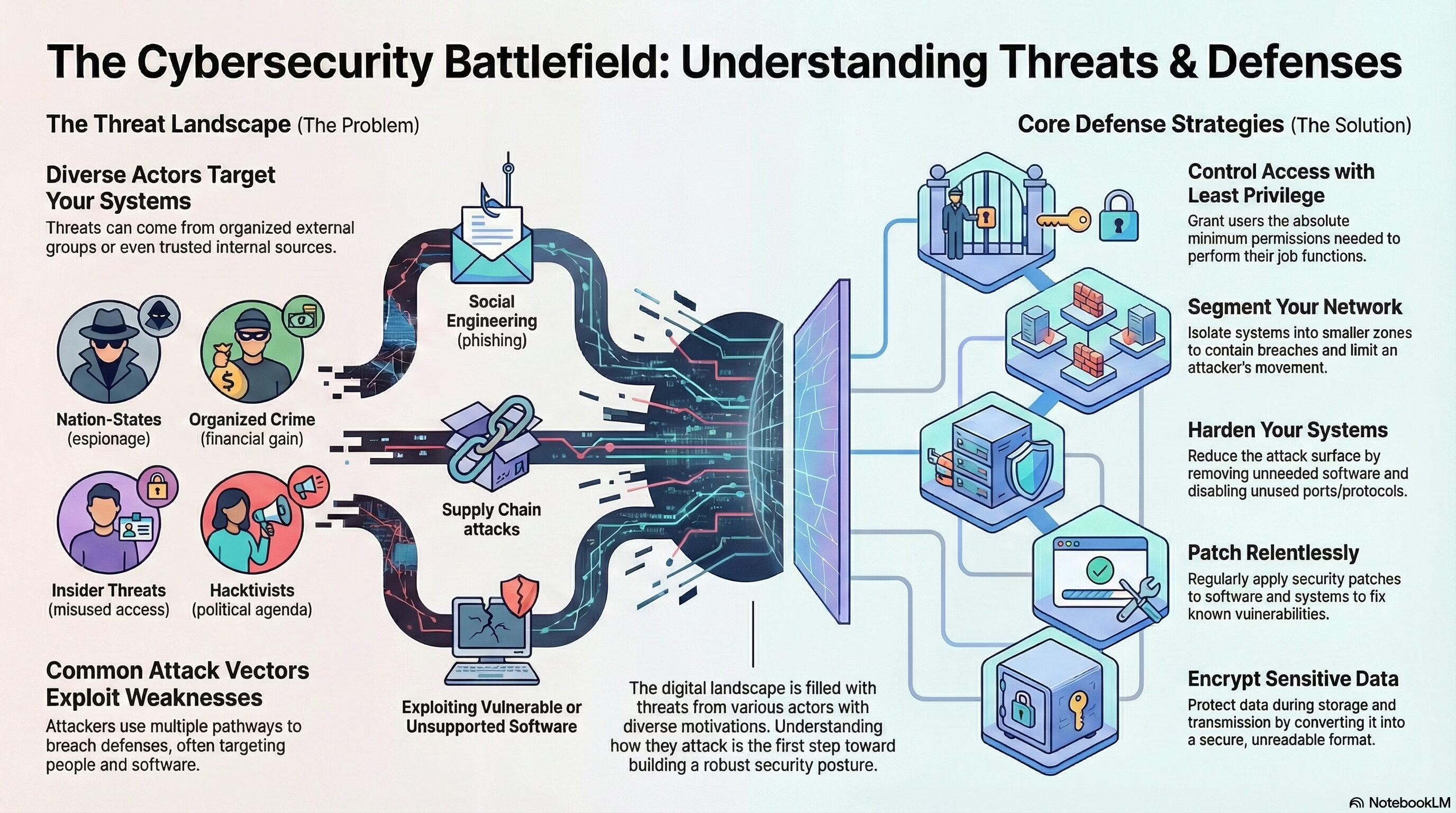
2.1 Compare and contrast common threat actors and motivations.
Threat Actors:
- Nation-state: Governments or state-sponsored entities engaged in cyber activities for political, economic, or military purposes.
- Unskilled attacker: Individuals with limited technical knowledge or skills, often using readily available tools or methods.
- Hacktivist: Individuals or groups who engage in hacking activities to promote a social or political agenda.
- Insider threat: Individuals within an organization who misuse their access and privileges to compromise security.
- Organized crime: Criminal groups engaged in cyber activities for financial gain, such as stealing sensitive information or conducting ransom attacks.
- Shadow IT: Unauthorized or unapproved use of IT systems and applications within an organization, often by employees.
Attributes of Actors:
- Internal/external:
- Internal: Threat actors originating from within the organization.
- External: Threat actors originating from outside the organization.
- Resources/funding:
- Resources: The tools, personnel, and infrastructure available to a threat actor.
- Funding: Financial support for cyber activities, often relevant to organized crime or nation-state actors.
- Level of sophistication/capability:
- Sophistication: The technical expertise and advanced methods employed by a threat actor.
- Capability: The overall ability of a threat actor to execute cyber attacks successfully.
Motivations:
- Data exfiltration: Stealing sensitive data for various purposes, such as selling it on the black market.
- Espionage: Gathering confidential information for political, economic, or military advantage.
- Service disruption: Disrupting the availability or functionality of services, often through DDoS attacks.
- Blackmail: Coercing individuals or organizations by threatening to reveal sensitive information.
- Financial gain: Engaging in cyber activities to generate profit, such as through ransomware attacks.
- Philosophical/political beliefs: Acting in alignment with personal or group beliefs, often for hacktivist purposes.
- Ethical: Conducting cyber activities with the intention of exposing or correcting perceived ethical violations.
- Revenge: Seeking retaliation against individuals or organizations for perceived wrongs.
- Disruption/chaos: Creating disorder and confusion, often for ideological reasons.
- War: Engaging in cyber warfare for geopolitical or military objectives.
2.2 Explain common threat vectors and attack surfaces.
Message-based:
- Email:
- Threat Vector: Email is a common vector for threats such as phishing attacks, malicious attachments, and links leading to malware-infected websites.
- Attack Surface: Users’ email accounts and the organization’s email infrastructure are potential attack surfaces.
- Short Message Service (SMS):
- Threat Vector: SMS can be exploited for smishing attacks, where attackers send deceptive messages to trick recipients into divulging sensitive information or clicking on malicious links.
- Attack Surface: Mobile devices and the telecommunication infrastructure are vulnerable surfaces.
- Instant Messaging (IM):
- Threat Vector: Attackers may use instant messaging platforms to distribute malware, phishing links, or engage in social engineering attacks.
- Attack Surface: Instant messaging applications and the devices running them are potential targets.
Image-based:
- Image-based:
- Threat Vector: Images can be carriers of malware or used to conceal malicious code, leading to the exploitation of vulnerabilities in image processing software.
- Attack Surface: Systems and applications handling image processing are potential targets.
File-based:
- File-based:
- Threat Vector: Files, especially attachments, are common carriers of malware. Malicious files can exploit vulnerabilities in software that processes or opens these files.
- Attack Surface: Systems and applications responsible for file handling and processing are at risk.
Voice Call:
- Voice Call:
- Threat Vector: Voice calls can be exploited for vishing attacks, where attackers impersonate legitimate entities to deceive individuals into providing sensitive information.
- Attack Surface: Telephony networks and devices used for voice calls are potential targets.
Removable Device:
- Removable Device:
- Threat Vector: Removable devices like USB drives can introduce malware when connected to systems, exploiting vulnerabilities in the way devices are managed.
- Attack Surface: Systems and applications that interact with removable devices are vulnerable surfaces.
Vulnerable Software:
- Client-based vs. Agentless:
- Threat Vector: Vulnerabilities in client-based or agentless security software can be exploited by attackers to compromise the security measures implemented by these solutions.
- Attack Surface: Security software and the systems it aims to protect are potential attack surfaces.
Unsupported Systems and Applications:
- Unsupported Systems and Applications:
- Threat Vector: Systems and applications that no longer receive updates or patches become attractive targets for attackers exploiting known vulnerabilities.
- Attack Surface: Systems running outdated or unsupported software are vulnerable surfaces.
Unsecure Networks:
- Wireless:
- Threat Vector: Unsecured wireless networks can be exploited for unauthorized access, eavesdropping, or man-in-the-middle attacks.
- Attack Surface: Wireless communication infrastructure and devices connected to these networks are potential targets.
- Wired:
- Threat Vector: Unsecured wired networks can be vulnerable to unauthorized access, network sniffing, or physical attacks on network cables.
- Attack Surface: Devices connected to wired networks and the network infrastructure are potential targets.
- Bluetooth:
- Threat Vector: Unsecured Bluetooth connections may be susceptible to unauthorized access, leading to data interception or device compromise.
- Attack Surface: Devices with Bluetooth capabilities and the Bluetooth communication channel are potential targets.
Open Service Ports:
- Open Service Ports:
- Threat Vector: Open service ports may expose services to external threats, allowing attackers to exploit vulnerabilities in those services.
- Attack Surface: Systems with open service ports are potential targets.
Default Credentials:
- Default Credentials:
- Threat Vector: Systems using default usernames and passwords are vulnerable to unauthorized access, as attackers may exploit these well-known credentials.
- Attack Surface: Systems and applications using default credentials are potential targets.
Supply Chain:
- Managed Service Providers (MSPs):
- Threat Vector: Attackers may target MSPs to compromise their systems, gaining access to the data and services of multiple clients.
- Attack Surface: MSPs and their interconnected client systems are potential targets.
- Vendors:
- Threat Vector: Security vulnerabilities in products supplied by vendors can be exploited by attackers to compromise the systems using those products.
- Attack Surface: Systems using products from vendors with security vulnerabilities are potential targets.
- Suppliers:
- Threat Vector: Suppliers may introduce vulnerabilities in the supply chain, impacting the security of the products or services they provide.
- Attack Surface: Systems relying on products or services from vulnerable suppliers are potential targets.
Human Vectors/Social Engineering:
- Phishing:
- Threat Vector: Phishing attacks involve deceiving individuals into revealing sensitive information through fraudulent emails or websites.
- Attack Surface: End-users and their susceptibility to phishing attempts are the primary targets.
- Vishing:
- Threat Vector: Vishing exploits voice communication channels to deceive individuals into providing sensitive information.
- Attack Surface: Telephony networks and individuals susceptible to vishing attacks are potential targets.
- Smishing:
- Threat Vector: Smishing attacks use SMS or text messages to trick individuals into divulging sensitive information.
- Attack Surface: Mobile devices and individuals vulnerable to smishing are potential targets.
- Misinformation/Disinformation:
- Threat Vector: Spreading false or misleading information can manipulate individuals or systems.
- Attack Surface: Individuals and organizations influenced by misinformation are potential targets.
- Impersonation:
- Threat Vector: Impersonation involves pretending to be someone else to deceive or gain unauthorized access.
- Attack Surface: Individuals and systems susceptible to impersonation are potential targets.
- Business Email Compromise:
- Threat Vector: Compromising business email accounts for fraudulent purposes, often involving financial transactions.
- Attack Surface: Business email accounts and communication channels susceptible to compromise are potential targets.
- Pretexting:
- Threat Vector: Pretexting involves creating a fabricated scenario to manipulate individuals into disclosing information.
- Attack Surface: Individuals susceptible to manipulation through pretexting are potential targets.
- Watering Hole:
- Threat Vector: Attackers compromise websites frequented by their victims to distribute malware or gather information.
- Attack Surface: Websites and individuals who visit these compromised sites are potential targets.
- Brand Impersonation:
- Threat Vector: Pretending to be a legitimate brand or organization to deceive individuals.
- Attack Surface: Individuals and systems susceptible to brand impersonation are potential targets.
- Typosquatting:
- Threat Vector: Registering domain names with slight misspellings to deceive users into visiting malicious sites.
- Attack Surface: Individuals mistyping web addresses and accessing malicious sites are potential targets.
2.3 Explain various types of vulnerabilities.
Application:
- Memory Injection: Memory injection occurs when an attacker injects malicious code into the memory space of a running process, manipulating its execution.
- Impact: Can lead to unauthorized access, data manipulation, or the execution of malicious commands.
- Buffer Overflow: Buffer overflow happens when a program writes more data to a buffer than it can hold, potentially overwriting adjacent memory.
- Impact: Can result in crashes, unauthorized access, or the execution of arbitrary code.
- Race Conditions: Race conditions occur when the behavior of software depends on the timing of events, leading to unpredictable outcomes.
- Types:
- Time-of-check (TOC): Exploiting a time gap between checking a condition and acting on it.
- Time-of-use (TOU): Exploiting a vulnerability during the brief period between a check and the subsequent action.
- Impact: Can lead to data corruption, unauthorized access, or denial of service.
- Types:
- Malicious Update: Malicious updates involve the distribution of fake or compromised software updates containing malware.
- Impact: Can result in the installation of malicious software, compromise of system integrity, or unauthorized access.
Operating System (OS)-based:
- Operating System (OS)-based: Vulnerabilities inherent in the design or implementation of an operating system.
- Impact: Can lead to privilege escalation, unauthorized access, or denial of service.
Web-based:
- Structured Query Language Injection (SQLi): SQL injection involves inserting malicious SQL code into input fields to manipulate a database.
- Impact: Can lead to unauthorized access, data manipulation, or disclosure of sensitive information.
- Cross-site Scripting (XSS): XSS occurs when an attacker injects malicious scripts into web pages viewed by other users.
- Impact: Can lead to session hijacking, defacement of websites, or the theft of user credentials.
Hardware:
- Firmware: Firmware vulnerabilities involve weaknesses in the software embedded in hardware devices.
- Impact: Can lead to unauthorized access, device manipulation, or compromise of system integrity.
- End-of-life: End-of-life vulnerabilities result from using hardware that is no longer supported or receiving security updates.
- Impact: Increases the risk of exploitation due to the absence of patches for known vulnerabilities.
- Legacy: Legacy hardware vulnerabilities arise from outdated or unsupported hardware components.
- Impact: Increases the risk of security breaches and limits the ability to adopt modern security measures.
Virtualization:
- Virtual Machine (VM) Escape: VM escape occurs when an attacker breaks out of a virtual machine to compromise the underlying hypervisor or host system.
- Impact: Can lead to unauthorized access to other virtual machines, data breaches, or denial of service.
- Resource Reuse: Resource reuse vulnerabilities involve the improper allocation or sharing of resources within a virtualized environment.
- Impact: Can result in resource exhaustion, performance degradation, or unauthorized access.
Cloud-specific:
- Cloud-specific: Vulnerabilities specific to cloud environments, often related to misconfigurations, shared resources, or insecure interfaces.
- Impact: Can lead to data breaches, unauthorized access, or service disruptions in cloud-based systems.
Supply Chain:
- Service Provider: Vulnerabilities introduced through services provided by external entities, such as cloud service providers.
- Impact: Can result in data breaches, unauthorized access, or service disruptions.
- Hardware Provider: Vulnerabilities introduced through hardware components supplied by external entities.
- Impact: Can lead to security breaches, compromised device integrity, or unauthorized access.
- Software Provider: Vulnerabilities introduced through software components supplied by external entities.
- Impact: Can result in security breaches, compromised system integrity, or unauthorized access.
Cryptographic:
- Cryptographic: Vulnerabilities related to the implementation or use of cryptographic algorithms or protocols.
- Impact: Can lead to data exposure, encryption bypass, or compromise of communication security.
Misconfiguration:
- Misconfiguration: Vulnerabilities resulting from improper or insecure configuration settings in software, systems, or networks.
- Impact: Can lead to unauthorized access, data leaks, or service disruptions.
Mobile Device:
- Side Loading: Side loading involves installing applications from unofficial sources rather than official app stores.
- Impact: Can result in the installation of malicious apps, compromise of device security, or unauthorized access.
- Jailbreaking: Jailbreaking removes restrictions on a mobile device, allowing the installation of unauthorized software.
- Impact: Can lead to security vulnerabilities, malware installation, or compromise of device integrity.
Zero-day:
- Zero-day: Zero-day vulnerabilities are flaws in software or hardware that are unknown to the vendor, making them susceptible to exploitation.
- Impact: Can lead to attacks before a patch is available, resulting in data breaches, unauthorized access, or system compromise.
2.4 Given a scenario, analyze indicators of malicious activity.
Malware Attacks:
- Ransomware: Ransomware is a type of malicious software designed to block access to a computer system or files until a sum of money, or ransom, is paid.
- Indicators:
- File Encryption: Sudden encryption of files with ransom notes.
- File Extension Changes: Altered file extensions indicating encryption.
- Ransom Messages: Display of ransom messages demanding payment.
- Indicators:
- Trojan: A Trojan, or Trojan Horse, is a type of malware that disguises itself as a legitimate file or program but is designed to cause harm or steal information once installed on a computer.
- Indicators:
- Unauthorized Access: Gaining access to systems without proper authorization.
- Payload Execution: Execution of malicious actions or payloads.
- Network Traffic: Unusual patterns in network communication.
- Indicators:
- Worm: A worm is a self-replicating type of malware that spreads across networks and computer systems, often without user interaction, by exploiting vulnerabilities.
- Indicators:
- Rapid Replication: Quick and widespread self-replication.
- Network Scanning: Frequent attempts to identify and infect vulnerable systems.
- Resource Consumption: Increased usage of system resources.
- Indicators:
- Spyware: Spyware is malicious software that secretly monitors and collects user information without their knowledge or consent, often for the purpose of data theft or unauthorized surveillance.
- Indicators:
- Unauthorized Data Access: Illegitimate access to sensitive data.
- Network Traffic: Unusual patterns in data sent to external servers.
- System Slowdown: Degraded system performance due to background activities.
- Indicators:
- Bloatware: Bloatware refers to software that comes pre-installed on a device and often includes unnecessary or unwanted applications that may consume system resources.
- Indicators:
- Unwanted Software: Presence of unnecessary and resource-consuming applications.
- Ad Pop-ups: Frequent and intrusive advertisements.
- Slow System Performance: Lagging system performance due to resource-intensive bloatware.
- Indicators:
- Virus: A computer virus is a type of malware that attaches itself to legitimate programs or files and spreads by replicating when the infected program is executed.
- Indicators:
- File Modification: Unauthorized changes to files or file properties.
- Unexpected Behavior: Unusual or unexpected system behavior.
- Rapid Spread: Spreading to other files or systems.
- Indicators:
- Keylogger: A keylogger is a type of software or hardware that records the keystrokes of a user, typically with the intent of capturing sensitive information such as passwords.
- Indicators:
- Keystroke Logging: Evidence of capturing keystrokes.
- Unauthorized Data Transmission: Suspicious data being sent over the network.
- Unusual System Activity: Keylogger-related processes running.
- Indicators:
- Logic Bomb: A logic bomb is a piece of code intentionally inserted into software or systems to execute a malicious action when certain conditions or triggers are met.
- Indicators:
- Unexpected System Events: Activation triggered by specific conditions.
- Unusual Network Traffic: Sudden increase in data transfer during activation.
- Delayed Payload: Presence of code designed to execute at a specific time or event.
- Indicators:
- Rootkit: A rootkit is a type of malicious software designed to conceal the existence of certain processes or programs on a computer, often used to gain unauthorized access or control.
- Indicators:
- System Anomalies: Unusual system behavior or inconsistencies.
- Unauthorized Access: Evidence of privileged access by an unknown entity.
- Altered System Files: Modification of critical system files.
- Indicators:
Physical Attacks:
- Brute Force: Brute force is a method of attempting to gain unauthorized access to a system or an account by systematically trying all possible passwords until the correct one is found.
- Indicators:
- Multiple Login Attempts: Numerous failed login attempts.
- Account Lockouts: Repeated lockouts due to excessive login failures.
- Unusual Access Times: Login attempts at odd hours.
- Indicators:
- Radio Frequency Identification (RFID) Cloning: RFID cloning involves copying the information stored on an RFID card or tag to create a duplicate, potentially allowing unauthorized access.
- Indicators:
- Unauthorized Access: Evidence of cloned RFID cards being used.
- Unexpected System Access: Access events from unrecognized RFID sources.
- Access Logs Discrepancies: Inconsistencies in RFID access logs.
- Indicators:
- Environmental: Environmental attacks involve physically compromising the security of a system, such as through tampering, destruction, or manipulating the surroundings.
- Indicators:
- Physical Damage: Signs of physical tampering or damage.
- Unauthorized Physical Access: Evidence of unauthorized individuals in secure areas.
- Missing or Displaced Hardware: Absence or relocation of critical hardware components.
- Indicators:
Network Attacks:
- Distributed Denial-of-Service (DDoS):
- Amplified: An amplified DDoS attack involves exploiting vulnerabilities to magnify the volume of traffic sent to a target, overwhelming its resources and causing disruption.
- Indicators:
- Network Congestion: Sudden increase in traffic leading to congestion.
- Service Disruption: Inability to access services due to overwhelming traffic.
- Alerts from DDoS Protection Tools: Notifications of DDoS attacks.
- Indicators:
- Reflected: A reflected DDoS attack involves the use of third-party systems to amplify and redirect attack traffic to the target, obscuring the origin.
- Indicators:
- Spoofed IP Addresses: Presence of spoofed source IP addresses.
- Surge in Requests: Abnormal increase in reflected requests.
- Traffic Analysis: Unusual patterns in network traffic.
- Indicators:
- Amplified: An amplified DDoS attack involves exploiting vulnerabilities to magnify the volume of traffic sent to a target, overwhelming its resources and causing disruption.
- Domain Name System (DNS) Attacks: DNS attacks target the Domain Name System, disrupting or manipulating the resolution of domain names to IP addresses.
- Indicators:
- DNS Query Abnormalities: Unexpected or excessive DNS queries.
- Domain Hijacking: Evidence of unauthorized changes to DNS records.
- Service Disruption: Inability to resolve domain names.
- Indicators:
- Wireless: Wireless attacks involve exploiting vulnerabilities in wireless networks to gain unauthorized access, intercept data, or disrupt network services.
- Indicators:
- Unauthorized Access Points: Presence of unapproved wireless access points.
- Unusual Device Connections: Devices connecting to unauthorized wireless networks.
- Signal Interference: Evidence of interference affecting network performance.
- Indicators:
- On-Path: On-path attacks involve intercepting and manipulating network traffic by positioning the attacker on the communication path between two systems.
- Indicators:
- Packet Interception: Evidence of intercepted packets.
- Unauthorized Routing: Anomalies in network routing.
- Unexpected Data Modification: Alteration of data during transmission.
- Indicators:
- Credential Replay: Credential replay attacks involve intercepting and reusing previously captured authentication credentials to gain unauthorized access.
- Indicators:
- Repeated Login Attempts: Multiple login attempts using the same credentials.
- Duplicate Authentication Requests: Replaying previously captured authentication data.
- Abnormal Access Patterns: Consistent use of specific credentials for access.
- Indicators:
- Malicious Code: Malicious code attacks involve the injection or execution of harmful code to compromise systems, steal data, or disrupt normal operations.
- Indicators:
- Unexpected Process Execution: Running of unauthorized processes.
- Antivirus Alerts: Notifications of malicious code detection.
- Unusual Outbound Traffic: Suspicious data leaving the network.
- Indicators:
Application Attacks:
- Injection: Injection attacks involve injecting malicious code or data into applications to manipulate their behavior, often exploiting vulnerabilities in input processing.
- Indicators:
- Unexpected Input Processing: Unauthorized input affecting application behavior.
- Database Query Abnormalities: Evidence of injected code in database queries.
- Error Messages: Unusual error messages indicating injection attempts.
- Indicators:
- Buffer Overflow: Buffer overflow attacks occur when a program writes more data to a buffer than it can hold, potentially leading to the execution of arbitrary code.
- Indicators:
- Memory Corruption: Evidence of buffer overflows leading to memory corruption.
- Unexpected Process Termination: Abnormal termination of processes.
- Execution of Arbitrary Code: Evidence of code execution beyond the buffer boundaries.
- Indicators:
- Replay: Replay attacks involve the unauthorized repetition or retransmission of legitimate data, often to gain unauthorized access.
- Indicators:
- Duplicate Transactions: Repeated or identical transactions.
- Unexpected System Access: Access events repeating without user interaction.
- Unusual Network Traffic Patterns: Consistent patterns in replayed network traffic.
- Indicators:
- Privilege Escalation: Privilege escalation attacks involve exploiting vulnerabilities to gain higher levels of access or privileges than originally granted.
- Indicators:
- Unauthorized Access: Evidence of accessing privileged areas.
- Inconsistent User Privileges: Users gaining unauthorized privileges.
- Security System Alerts: Notifications of attempted privilege escalation.
- Indicators:
- Forgery: Forgery attacks involve creating or altering data or transactions with the intent to deceive or gain unauthorized benefits.
- Indicators:
- Falsified Data: Presence of manipulated or forged data.
- Unexpected Transactions: Transactions not consistent with typical user behavior.
- Discrepancies in Records: Inconsistencies in logs and records.
- Indicators:
- Directory Traversal: Directory traversal attacks involve accessing files or directories outside of the intended scope by exploiting insufficient input validation.
- Indicators:
- Unauthorized File Access: Attempts to access files outside the intended directory.
- Atypical File Path Requests: Non-standard requests indicating traversal attempts.
- File Access Errors: Errors resulting from improper directory navigation.
- Indicators:
Cryptographic Attacks:
- Downgrade: Cryptographic downgrade attacks involve manipulating or forcing systems to use weaker encryption protocols than their capabilities.
- Indicators:
- Connection Anomalies: Unexpected changes in encryption protocols.
- Security Protocol Mismatch: Inconsistencies in negotiated security protocols.
- Cipher Suite Downgrade: Evidence of downgrading to weaker cryptographic algorithms.
- Indicators:
- Collision: Cryptographic collision attacks involve finding two different inputs that produce the same hash value, compromising the integrity of hash functions.
- Indicators:
- Checksum Mismatch: Conflicts in hash checksums.
- Duplicate Hash Values: Repeated instances of the same hash.
- Inconsistencies in Data Integrity: Evidence of data integrity compromise.
- Indicators:
- Birthday: Birthday attacks exploit the mathematical probability of finding two different inputs with the same hash value in a hash function.
- Indicators:
- Unusual Hash Patterns: Frequent occurrences of identical hash values.
- Inconsistent Hash Output: Hash functions producing unexpected results.
- Security System Alerts: Notifications of potential birthday attacks.
- Indicators:
Password Attacks:
- Spraying: Password spraying attacks involve attempting to gain unauthorized access by systematically trying a small set of common passwords across multiple accounts.
- Indicators:
- Multiple Login Attempts: Numerous attempts using a small set of passwords.
- Account Lockouts: Frequent lockouts due to multiple login failures.
- Unusual Access Times: Login attempts at odd hours.
- Indicators:
- Brute Force: Brute force attacks involve attempting to gain unauthorized access by systematically trying all possible password combinations.
- Indicators:
- Sequential Password Attempts: Systematic trial of passwords.
- Account Lockouts: Repeated lockouts due to excessive login failures.
- Unusual Access Times: Login attempts at odd hours.
- Indicators:
Indicators:
- Account Lockout: Account lockout occurs when a user’s account is temporarily or permanently disabled due to multiple failed login attempts.
- Indicators:
- Multiple Failed Login Attempts: Frequent login failures leading to lockout.
- Unauthorized Access Alerts: Notifications of repeated failed attempts.
- Indicators:
- Concurrent Session Usage: Concurrent session usage refers to the simultaneous use of a user account from multiple locations or devices.
- Indicators:
- Unusual Number of Active Sessions: Unexpected multiple active sessions for a single user.
- Cross-Geographical Session Activity: Simultaneous sessions from geographically distant locations.
- Indicators:
- Blocked Content: Blocked content indicates restricted or prohibited access to certain data, websites, or resources.
- Indicators:
- Error Messages: Notifications of blocked or restricted content.
- User Complaints: Reports of inability to access specific content.
- Indicators:
- Impossible Travel: Impossible travel refers to user logins from geographically distant locations within an impractical timeframe.
- Indicators:
- Login from Multiple Geographically Distant Locations: Evidence of logins from locations impossible to reach in a short timeframe.
- Unusual Login Patterns: Unexpected changes in login behavior.
- Indicators:
- Resource Consumption: Resource consumption indicates the utilization of system resources, such as CPU, memory, or bandwidth, potentially exceeding normal levels.
- Indicators:
- Unexplained Resource Spikes: Sudden and unexplained increases in resource usage.
- Performance Degradation: Sluggish system performance due to excessive resource consumption.
- Indicators:
- Resource Inaccessibility: Resource inaccessibility occurs when authorized users or systems are unable to access specific resources.
- Indicators:
- Unauthorized Access Attempts: Evidence of repeated failed attempts to access specific resources.
- System Alerts: Notifications of blocked or restricted resource access.
- Indicators:
- Out-of-Cycle Logging: Out-of-cycle logging refers to logging events that occur outside of regular or expected logging cycles.
- Indicators:
- Unexpected Log Entries: Logging events occurring outside regular cycles.
- Unusual Volume of Logs: Abnormal increase in log entries.
- Security System Alerts: Notifications of out-of-cycle logging.
- Indicators:
- Published/Documented: Published or documented vulnerabilities are security weaknesses that have been publicly disclosed, often accompanied by details on how to exploit them.
- Indicators:
- Publicized Exploits: Known exploits published in public forums.
- Documentation of Vulnerabilities: Availability of detailed guides on exploiting specific weaknesses.
- Security System Alerts: Notifications of attempted exploits based on published information.
- Indicators:
- Missing Logs: Missing logs refer to the absence of recorded events or activities within a system’s log files during specific time periods.
- Indicators:
- Gaps in Logging History: Missing log entries or periods without logs.
- Unauthorized Log Deletion: Evidence of logs being intentionally removed.
- Security System Alerts: Notifications of missing or tampered logs.
- Indicators:
2.5 Explain the purpose of mitigation techniques used to secure the enterprise.
- Segmentation: Segmentation involves dividing a network into smaller, isolated segments to contain the impact of a security breach. It limits lateral movement for attackers, making it harder for them to access sensitive areas.
- Access Control: Access control regulates who or what can view or use resources in a system. It prevents unauthorized access and protects sensitive data.
- Access Control List (ACL): A list that defines permissions attached to an object, such as a file or a network resource.
- Permissions: Specify what actions users or system processes are allowed to perform on a resource.
- Application Allow List: Defines a list of approved applications that are allowed to run on a system, reducing the risk of malicious software execution.
- Isolation: Isolation separates potentially vulnerable systems from critical systems, limiting the impact of a security incident.
- Patching: Regularly applying updates and patches to software and systems to fix vulnerabilities and protect against known threats.
- Encryption: Converts data into a secure format to prevent unauthorized access. It protects data during transmission and storage.
- Monitoring: Continuous observation of systems and networks to detect and respond to security incidents in real-time.
- Least Privilege: Users are given the minimum levels of access necessary to perform their job functions, reducing the risk of unauthorized access.
- Configuration Enforcement: Ensures that systems and networks are configured securely by enforcing predefined security configurations.
- Decommissioning: Safely retiring or taking out of service systems, devices, or software to prevent them from being exploited.
- Hardening Techniques: Strengthening security by implementing various measures.
- Encryption: Protects data by converting it into a secure format.
- Installation of Endpoint Protection: Installing security software on individual devices to prevent and detect threats.
- Host-based Firewall: A firewall that operates on individual devices, controlling incoming and outgoing network traffic.
- Host-based Intrusion Prevention System (HIPS): Eliminating unnecessary applications and services reduces the attack surface and minimizes potential vulnerabilities. Unneeded software can introduce security risks if not properly maintained and can be an easy target for attackers.
- Disabling Ports/Protocols: Closing unnecessary ports and disabling unused network protocols reduces the attack surface and potential vulnerabilities.
- Default Password Changes: Changing default passwords on systems and devices ensures that attackers cannot easily exploit known credentials.
Removal of Unnecessary Software: Eliminating unnecessary applications and services reduces potential avenues for exploitation.