Table of Contents
Security+ Domain 1 – General Security Concepts (12% weightage)
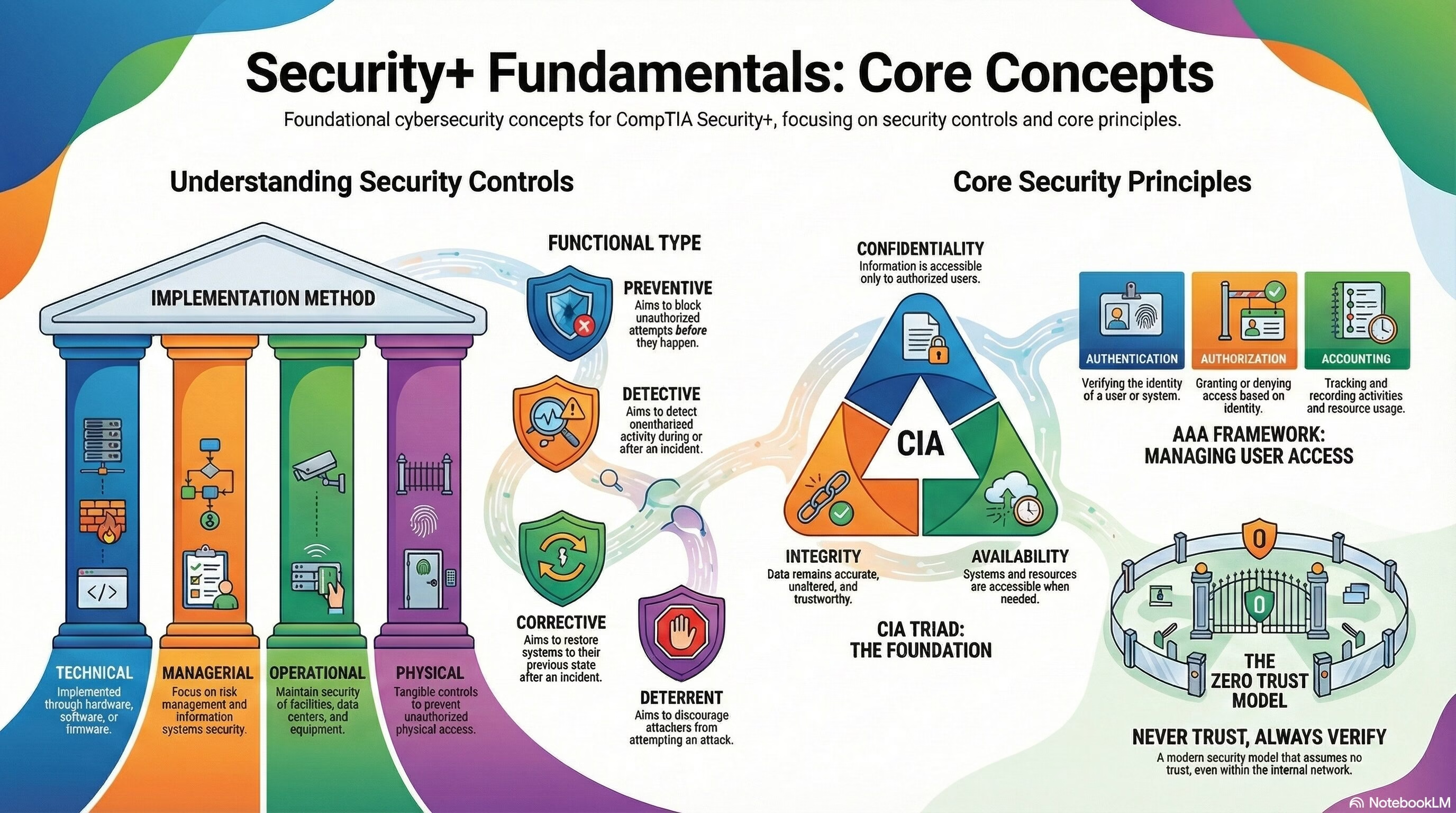
Key terms and definitions from this objective are given below:
1.1 Compare and contrast various types of security controls.
Categories:
- Technical: These are security controls that are primarily implemented and executed by the information system through mechanisms contained in the hardware, software, or firmware components of the system.
- Managerial: These are security controls that focus on the management of risk and the management of information systems security.
- Operational: These are security controls that maintain the security and integrity of system facilities, data centers, and equipment.
- Physical: These are tangible security controls used to prevent or detect unauthorized access to physical areas, systems, or assets.
Control Types:
- Preventive: These controls aim to block any unauthorized attempts to change a system before it happens.
- Deterrent: These controls aim to discourage attackers from attacking their systems or premises.
- Detective: These controls include security measures implemented by an organization to detect unauthorized activity or a security incident.
- Corrective: These controls include measures that are implemented to restore the systems or resources to their previous state after a security incident or an unauthorized activity.
- Compensating: These are controls employed by an organization in lieu of a recommended security control that provides equivalent or comparable protection for an information system.
- Directive: These controls aim to ensure that identified risks are managed through formal directions provided to the management and employees of the organization.
1.2 Summarize fundamental security concepts.
Confidentiality, Integrity, and Availability (CIA):
- Confidentiality: Ensuring that information is only accessible to those who have the proper authorization.
- Integrity: Ensuring that data remains accurate, unaltered, and trustworthy throughout its lifecycle.
- Availability: Ensuring that systems and resources are accessible and available when needed by authorized users.
Non-repudiation:
- Non-repudiation: A concept that prevents an individual or entity from denying the validity of their previous actions or commitments.
Authentication, Authorization, and Accounting (AAA):
- Authentication: Verifying the identity of a person, system, or entity.
- Authorization: Granting or denying access to resources or actions based on authenticated identity.
- Accounting: Tracking and recording activities and resource usage, often for audit purposes.
Gap analysis:
- Gap analysis: The process of assessing the difference between current and desired cybersecurity postures to identify areas for improvement.
Zero Trust:
- Zero Trust: A security model that assumes no trust, even within the internal network. It requires authentication and verification for all users and devices.
- Control Plane:
- Adaptive identity: Adjusting access privileges based on the changing identity of users or systems.
- Threat scope reduction: Minimizing the potential impact of security breaches by reducing the attack surface.
- Policy-driven access control: Enforcing access policies based on defined rules.
- Policy Administrator: Manages and configures security policies.
- Policy Engine: Enforces security policies.
- Data Plane:
- Implicit trust zones: Designating areas where trust is automatically assumed.
- Subject/System: Refers to entities (users, systems) involved in security decisions.
- Policy Enforcement Point: The location where security policies are enforced.
- Control Plane:
Physical security:
- Bollards: Short vertical posts used to control or direct traffic.
- Access control vestibule: An enclosed area with two sets of doors to control access.
- Fencing: Physical barriers used for security.
- Video surveillance: Using cameras to monitor and record activities.
- Security guard: Human personnel providing security.
- Access badge: A physical or electronic card granting access.
- Lighting: Illumination for security purposes.
- Sensors:
- Infrared: Detects heat signatures.
- Pressure: Responds to physical force or pressure.
- Microwave: Uses microwaves for detection.
- Ultrasonic: Uses ultrasonic waves for detection.
Deception and disruption technology:
- Honeypot: A decoy system designed to attract and analyze attackers.
- Honeynet: A network of honeypots.
- Honeyfile: A file used to detect unauthorized access.
- Honeytoken: A type of bait used to detect unauthorized access.
1.3 Explain the importance of change management processes and the impact to security.
Business processes impacting security operation:
- Approval process: A formal process where changes or implementations are reviewed and authorized before being executed. In IT, this ensures that security-related changes are validated and approved to avoid unauthorized or insecure modifications.
- Ownership: Designates individuals or groups responsible for specific processes, systems, or assets. In IT, it clarifies accountability for the security of each component.
- Stakeholders: Individuals or groups with an interest or concern in the security and functioning of a system or process. In IT, identifying and involving stakeholders ensures that their needs and concerns are considered in security decisions.
- Impact analysis: Assessing the potential effects or consequences of a change or event on systems, processes, or the organization. In IT, it helps predict and mitigate negative impacts on security caused by changes or incidents.
- Test results: Outcomes and findings from testing activities, such as security assessments or penetration testing. In IT, analyzing test results helps identify vulnerabilities and weaknesses in the security infrastructure.
- Backout plan: A predefined set of steps to revert changes or implementations in case of issues or failures. In IT, it ensures a secure fallback mechanism if security changes lead to unexpected problems.
- Maintenance window: A scheduled timeframe during which system maintenance or changes can be performed without affecting normal operations. In IT, it ensures that security updates and changes can be implemented without disrupting critical business operations.
- Standard operating procedure: A documented set of step-by-step instructions to perform routine tasks or processes. In IT, it provides a consistent and secure approach to handling security-related operations and incidents.
Technical implications:
- Allow lists/deny lists: Lists specifying entities (such as IP addresses, applications, users) that are allowed or denied access. In IT, it controls access to systems, networks, or resources based on predefined lists.
- Restricted activities: Actions that are limited or prohibited to prevent security risks. In IT, it ensures that users and systems adhere to security policies and guidelines.
- Downtime: Period during which a system or service is unavailable. In IT, security changes or incidents may require planned downtime to implement measures or investigate issues.
- Service restart: Restarting a service to apply changes or address issues. In IT, it can be necessary after security updates or to recover from security incidents.
- Application restart: Restarting an application to apply changes or address issues. In IT, it ensures that security changes affecting applications are applied.
- Legacy applications: Older software or applications that may no longer be actively supported or updated. In IT, they may present security challenges; special measures may be needed to secure legacy applications.
- Dependencies: Relationships between different components or systems where one relies on the other. In IT, understanding dependencies is crucial to prevent security issues when making changes.
Documentation:
- Updating diagrams: Keeping visual representations of systems, processes, or networks current. In IT, it ensures that security professionals and stakeholders have accurate visual references for the security architecture.
- Updating policies/procedures: Modifying documented guidelines or instructions related to security practices. In IT, it ensures that security policies and procedures align with current security requirements and practices.
Version control:
- Version control: Managing and tracking changes to documents, code, or configurations to maintain a history of revisions. In IT, version control is crucial for tracking changes to security-related documents, policies, or configurations over time, facilitating auditing and rollback if necessary.
1.4 Explain the importance of using appropriate cryptographic solutions.
Public Key Infrastructure (PKI):
- Public key: A cryptographic key that is shared openly and used for encryption and verification of digital signatures.
- Private key: A secret key known only to the owner and used for decrypting messages and creating digital signatures.
- Key escrow: A process where a trusted third party holds a copy of an encryption key to be used in case the original key is lost or compromised.
Encryption:
- Level:
- Full-disk: Encrypting an entire storage device, protecting all data on it.
- Partition: Encrypting specific partitions on a storage device.
- File: Encrypting individual files.
- Volume: Encrypting a logical volume on a storage device.
- Database: Encrypting a database to protect its contents.
- Record: Encrypting individual records within a database.
- Transport/communication: Encrypting data during transmission to ensure its confidentiality.
- Asymmetric: Encryption using a pair of keys (public and private) for encryption and decryption.
- Symmetric: Encryption using a single key for both encryption and decryption.
- Key exchange: Secure exchange of cryptographic keys between parties.
- Algorithms: Mathematical functions used for encryption and decryption.
- Key length: The size of the encryption key, usually measured in bits.
Tools:
- Trusted Platform Module (TPM): A hardware module that provides secure storage of cryptographic keys and performs cryptographic operations.
- Hardware security module (HSM): A physical device designed to manage and safeguard cryptographic keys.
- Key management system: A system for managing cryptographic keys throughout their lifecycle.
- Secure enclave: A secure and isolated area in a system’s hardware or software for protecting sensitive data and operations.
Obfuscation:
- Steganography: Concealing information within other non-secret data.
- Tokenization: Replacing sensitive data with a non-sensitive equivalent (token).
- Data masking: Concealing specific data elements within a database.
Hashing:
- Hashing: A one-way function that converts input data into a fixed-size string of characters, often used for data integrity verification.
- Salting: Adding a random value (salt) to data before hashing to enhance security.
Digital Signatures:
- Digital signatures: A cryptographic technique for validating the authenticity and integrity of digital messages or documents.
- Key stretching: Techniques to increase the security of passwords by making them more resistant to brute-force attacks.
Blockchain:
- Blockchain: A decentralized and distributed ledger technology that records transactions across multiple computers in a secure and tamper-resistant manner.
- Open public ledger: A publicly accessible and transparent record of all transactions on a blockchain.
Certificates:
- Certificate authorities: Trusted entities that issue digital certificates.
- Certificate revocation lists (CRLs): Lists of digital certificates that have been revoked before their expiration date.
- Online Certificate Status Protocol (OCSP): A protocol for checking the validity of a digital certificate.
- Self-signed: A certificate that is signed by its own creator.
- Third-party: Certificates issued by a trusted third-party certificate authority.
- Root of trust: A foundational element in a security system that is inherently trusted.
- Certificate signing request (CSR) generation: The process of generating a request for a digital certificate.
Wildcard: A type of certificate that can be used for multiple subdomains of a domain.