Table of Contents


Short-Answer Quiz
- Describe the CIA triad and its opposite, the DAD triad. What are the core objectives of each concept in the context of information security?
- Explain the difference between the legal systems of civil law and common law. How does each system rely on different sources for its legal authority?
- What is the purpose of data classification, and what roles do a data controller and data processor play in managing sensitive data?
- Define the security model of Zero Trust. What fundamental assumption does this model make about network users and devices?
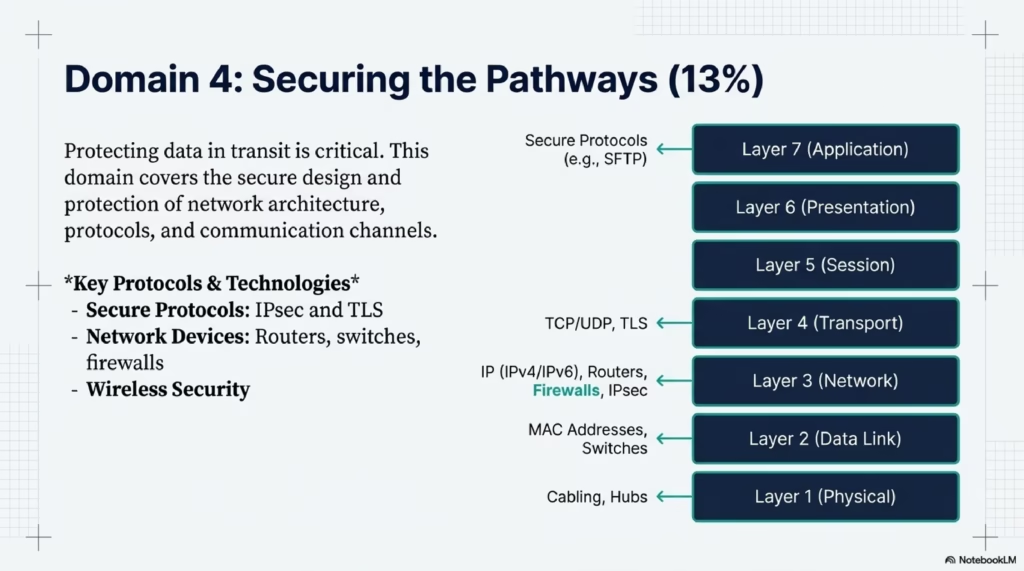
- Compare and contrast the TCP/IP and OSI network models. What are the layers of each model?
- What is Federated Identity Management (FIM)? Describe its primary benefits for users and organizations across multiple systems.
- Differentiate between a vulnerability assessment and a penetration test. What is the primary goal of each testing method?
- Define Maximum Tolerable Downtime (MTD) and Recovery Time Objective (RTO). How do these two metrics relate to business continuity planning?
- Explain the difference between a compiler and an interpreter in software development. How does each program process source code?
- Describe the concept of defense-in-depth. Why is this considered a fundamental strategy for protecting information assets?
Answer Key
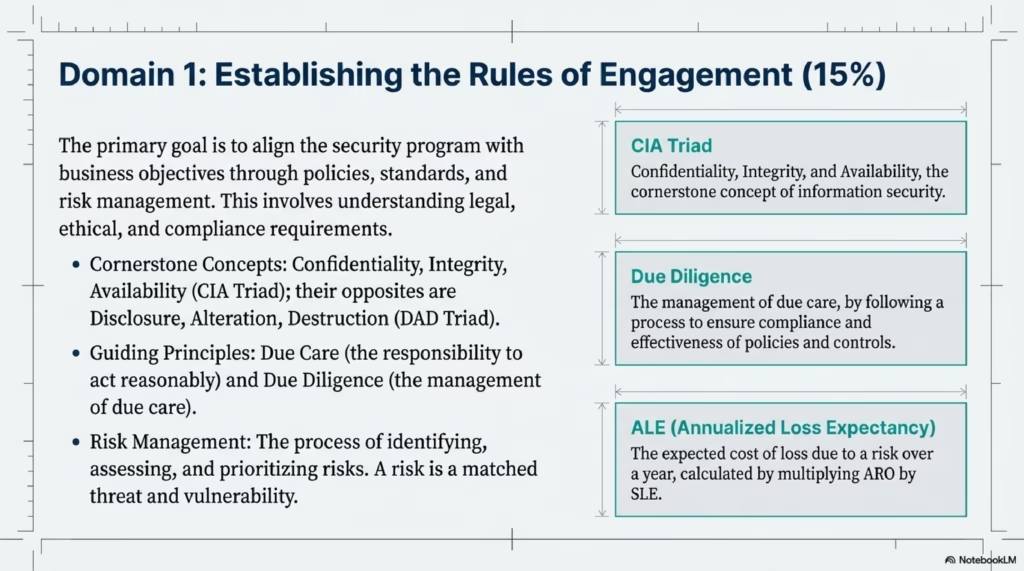
- The CIA triad is the cornerstone concept of information security, describing the three objectives of protecting data: Confidentiality (preventing unauthorized disclosure), Integrity (preventing unauthorized modification), and Availability (ensuring information is available when needed). Its opposite, the DAD triad, describes threats to data: Disclosure, Alteration, and Destruction.
- Civil law is a legal system that relies on codified laws or statutes, with a judicial branch that interprets them. In contrast, common law is a legal system that relies on judicial precedents and case rulings, with a legislative branch that creates new laws.
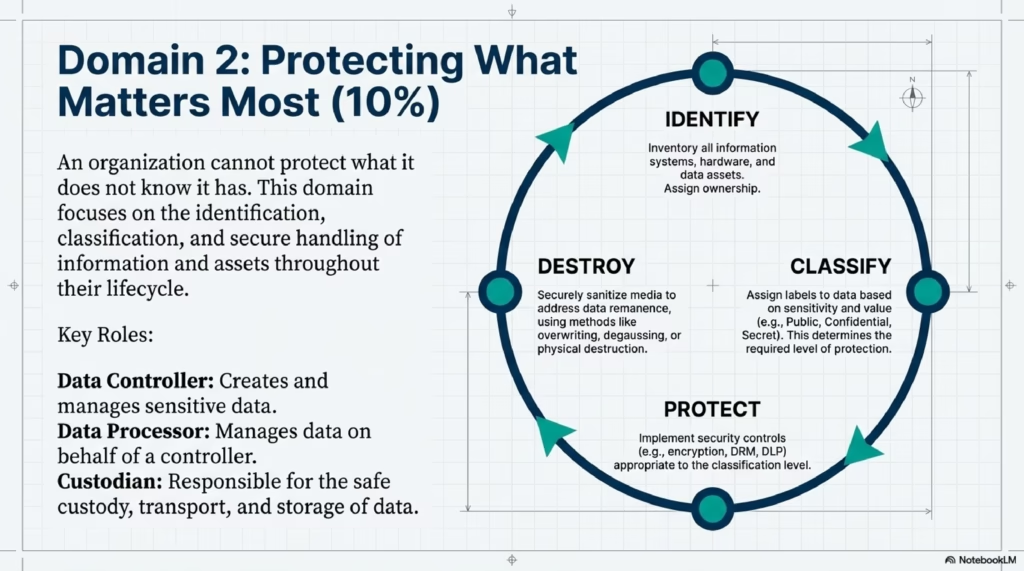
- Data classification is the process of assigning labels to data based on its sensitivity and value, which helps determine the appropriate level of protection. A data controller is a person or entity that creates and manages sensitive data, while a data processor is a person or entity that manages data on behalf of a data controller.
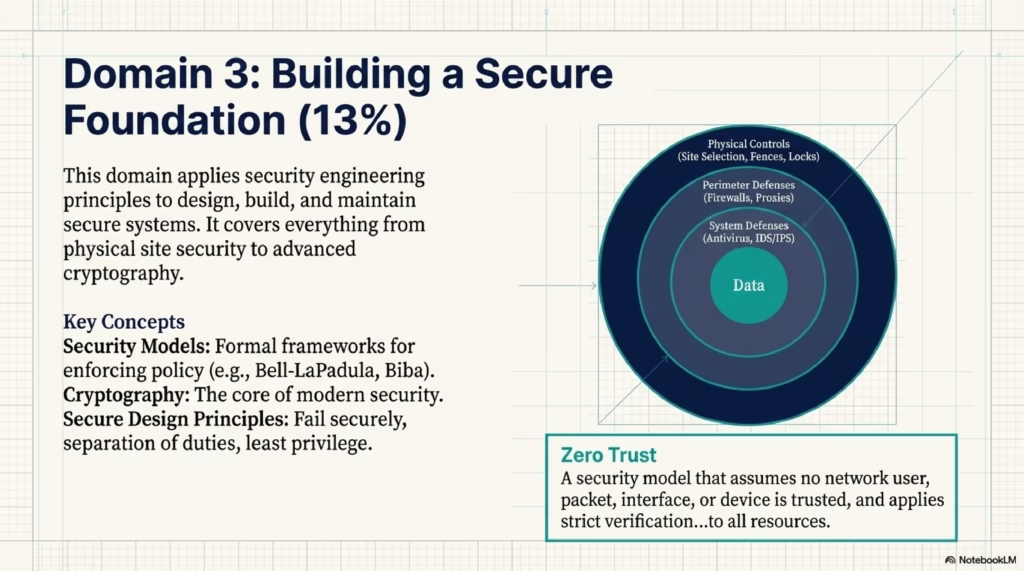
- Zero Trust is a security model that assumes no network user, packet, interface, or device is trusted. It operates on the principle of “never trust, always verify,” applying strict verification and enforcement mechanisms to all resources and transactions, regardless of their location.
- The OSI model is a network model with seven layers: physical, data link, network, transport, session, presentation, and application. The TCP/IP model is a simpler network model with four layers: network access, Internet, transport, and application.
- Federated Identity Management (FIM) is a type of identity management that enables single sign-on (SSO) across multiple systems and domains. It works by delegating the responsibility of authenticating a user to a trusted external party, which enhances user experience and reduces administrative overhead.
- A vulnerability assessment is a scan of a network or system for a list of predefined vulnerabilities, such as misconfigurations or outdated software. A penetration test is an authorized attempt to actively break into an organization’s perimeter to demonstrate real-world risk and exploit vulnerabilities.
- Maximum Tolerable Downtime (MTD) is the longest period that an organization can tolerate a system being unavailable without suffering unacceptable consequences. Recovery Time Objective (RTO) is the target time for restoring that system after a disruption. The RTO must be less than the MTD for a business continuity plan to be effective.
- A compiler is a program that takes source code and translates it all at once into machine code, producing a separate executable file. An interpreter is a program that translates and executes source code line-by-line on the fly, without creating a separate executable file.
- Defense-in-depth is the strategy of applying multiple layers of safeguards or controls to protect an asset. This layered approach ensures that if one control fails, other controls are still in place to protect the asset, thereby increasing the overall security posture.
Essay Questions
- Discuss the relationship between the principles of “least privilege” and “need to know” from Domain 1 and the access control models (e.g., RBAC, ABAC) from Domain 5. How do these concepts work together to enforce security policies within an organization?
- Explain how an organization would use the processes and techniques from Domain 6 (Security Assessment and Testing) to validate the effectiveness of the perimeter and system defenses described in Domain 3 (Security Architecture and Engineering).
- Trace the lifecycle of a security incident, integrating concepts from multiple domains. Describe how preventative controls (Domain 7), network monitoring (Domain 4), and forensic investigation (Domain 7) are applied from initial detection through to lessons learned.
- Analyze the security challenges an organization faces when dealing with third parties as outlined in Domain 1. How can controls and frameworks like Data Loss Prevention (DLP) and Cloud Access Security Brokers (CASB) from Domain 2 help mitigate these risks?
- Compare the Waterfall and Agile software development methodologies described in Domain 8. Discuss how security can be integrated into each model, referencing the concept of DevSecOps.
——————————————————————————–
Comprehensive Glossary
A
- AAA – Authentication, Authorization, and Accountability, the three processes that ensure the identity, access, and responsibility of users and systems.
- Access Control Models – The frameworks that define how access decisions are made, such as discretionary access control, mandatory access control, non-discretionary access control, etc.
- Access Control Technologies – The tools and mechanisms that implement access control policies, such as access control lists, role-based access control, single sign-on, etc.
- Access Management – The process of granting, restricting, and revoking access to resources based on the identity, role, or context of the users and devices.
- Access Matrix – A model of access control that uses rows to represent subjects and columns to represent objects, with privileges listed in each cell.
- Accountability – The ability to audit and monitor the actions of users or devices on a system and ensure compliance with security policies and regulations.
- Account Harvesting – The process of collecting all the legitimate account names on a system, often used for password guessing attacks.
- Active Content – Program code embedded in the contents of a web page that is automatically downloaded and executed on the user’s workstation, such as Java or ActiveX.
- Active-Active Cluster – A cluster configuration that involves multiple systems that are all online and actively processing traffic or data.
- Active-Passive Cluster – A cluster configuration that involves devices or systems that are already in place, configured, powered on, and ready to begin processing network traffic should a failure occur on the primary system.
- Annualized Loss Expectancy (ALE) – The expected cost of loss due to a risk over a year, calculated by multiplying the annual rate of occurrence (ARO) of an event by the single loss expectancy (SLE) of that event.
- Antiforensics – Techniques that make forensic investigation difficult or impossible, such as memory-resident malware, encryption, or data wiping.
- Antivirus – Software that detects and removes malware from a system, by using signatures, heuristics, or behavior analysis.
- Application Development Model – A framework that defines the phases, activities, deliverables, and milestones of a software development project, such as the Waterfall Model, Spiral Model, Extreme Programming (XP), and DevOps.
- Artificial Intelligence – The science of programming electronic computers to “think” more intelligently, sometimes mimicking the ability of mammal brains, such as playing chess, recognizing faces, or driving cars.
- Assembly language – A low-level computer programming language that uses short mnemonics, such as “ADD”, “SUB”, and “JMP”, that match to machine language instructions.
- Asymmetric cryptography – A branch of cryptography that uses a pair of keys (a public key and a private key) for encryption and decryption, and provides confidentiality, integrity, and authentication.
- ATA Secure Erase – A command that securely erases all data on an SSD by resetting all blocks to the factory default state and generating a new encryption key.
- Attribute-Based Access Control (ABAC) – A model that assigns access permissions to users based on their attributes, such as location, department, or clearance level. ABAC allows for more fine-grained and dynamic access control by considering various factors at the time of the access request.
- Authentication – The process of verifying an identity claim, such as a username and password, a token, or a biometric feature.
- Authentication Methods – The ways of verifying the identity of a subject, such as passwords, tokens, biometrics, etc.
- Authorization – The process of granting or denying access to resources based on the authenticated identity and the access policies.
- Availability – Ensures that information is available when needed.
B
- BCP/DRP – Business Continuity Plan/Disaster Recovery Plan. A set of policies and procedures that aim to ensure the continuity of critical business functions and minimize the impact of disruptive events.
- Bottom-Up programming – A programming approach that starts with the low-level technical implementation details and works up to the concept of the complete program.
- Business continuity – The ability of an organization to maintain its essential functions and operations during and after a disruption, such as a natural disaster or a cyberattack.
- Bytecode – An intermediary form of code, such as Java bytecode, that is platform-independent and must be converted into machine code by a virtual machine, such as the Java Virtual Machine (JVM).
C
- CIA triad – Confidentiality, Integrity, and Availability, the cornerstone concept of information security that describes the three objectives of protecting data and systems.
- CIDR – Classless Inter-Domain Routing, a method of dividing the IP address space into variable-sized networks, using a slash notation to indicate the network prefix length.
- Civil law – A legal system that relies on codified laws or statutes, and a judicial branch that interprets them.
- Class – A template or blueprint that defines the attributes and methods of an object, such as mathematical operators, the parent class of Addy.
- Closed source software – Software that is typically released in executable form, keeping the source code confidential, such as Oracle and Microsoft Windows 11.
- Cloud Access Security Broker (CASB) – A software tool or service that acts as an intermediary between cloud service consumers and cloud service providers. CASBs provide security policy enforcement, visibility, data security, threat protection, and compliance for cloud-based resources.
- Cohesion – A measure of how independent an object is in performing its functions.
- Combinatorial Software Testing – A black box testing method that seeks to identify and test all unique combinations of software inputs, such as pairwise testing.
- Common law – A legal system that relies on judicial precedents and case rulings, and a legislative branch that creates new laws.
- Compiler – A program that takes source code, such as C or Basic, and compiles it into machine code, producing an executable file.
- Computer-Aided Software Engineering (CASE) – The use of software programs to assist in the creation and maintenance of other computer programs, such as 4GL, object-oriented languages, and GUIs.
- Confidentiality – Seeks to prevent the unauthorized disclosure of information: it keeps data secret.
- Configuration Management – A process that controls and documents the changes made to the software and hardware components of a system throughout its lifecycle.
- COOP – Continuity of Operations Plan. A plan that describes the procedures required to maintain operations during a disaster.
- Copyright – A legal right that grants the author of an original work the exclusive right to reproduce, distribute, perform, display, or license the work, for a limited period of time.
- Cornerstone Cryptographic Concepts – The fundamental concepts and techniques of cryptography, such as encryption, decryption, hashing, digital signatures, etc.
- Coupling – A measure of how much an object depends on other objects to perform its functions.
- Credential Management Systems – Systems that help harden user credentials by providing secure password generation, storage, rotation, and audit.
- Cryptographic Attacks – The methods and techniques for breaking or compromising cryptographic systems, such as brute force, birthday, chosen plaintext, etc.
D
- DAD triad – Disclosure, Alteration, and Destruction, the opposite of the CIA triad that describes the three types of threats to data and systems.
- Data classification – The process of assigning labels to data based on its sensitivity and value to an organization.
- Data controller – A person or entity that creates and manages sensitive data within an organization.
- Data Loss Prevention (DLP) – A class of solutions that aim to detect or prevent data from leaving an organization in an unauthorized manner.
- Data mining – The search for patterns in a data warehouse, using statistical or machine learning techniques.
- Data processor – A person or entity that manages data on behalf of a data controller.
- Data remanence – The persistence of data on a storage device after non-invasive attempts to delete it.
- Data warehousing – The collection and storage of large amounts of data in a database, requiring large scalable storage solutions and high performance.
- Database – A structured collection of related data that allows queries, insertions, deletions, and other functions, managed by a Database Management System (DBMS).
- Database normalization – A process that seeks to make the data in a database table logically concise, organized, and consistent, removing redundant data.
- Database replication – A database high availability option that mirrors a live database, allowing simultaneous reads and writes to multiple replicated databases by clients.
- Database shadowing – A database high availability option that mirrors all changes made to a primary database, but clients do not access the shadow.
- Database view – The result of a query on a database table, which may be used to provide a constrained user interface.
- DDoS – Distributed Denial-of-Service, a type of attack that floods a target system or network with a large amount of traffic or requests.
- Decryption – The process of reversing encryption, using the same or a different key or algorithm, to restore the original data.
- Defense-in-depth – The strategy of applying multiple layers of safeguards (controls) to protect an asset, in case one or more of them fail.
- Delegation – A mechanism that allows an object to pass a message to another object if it does not know how to perform a requested function.
- Digital certificate – A digital document that contains information about an entity and its public key, and is signed by a trusted authority.
- Digital forensics – A formal approach to dealing with investigations and evidence with special consideration of the legal aspects of this process.
- Digital Rights Management (DRM) – A set of technologies and techniques that restrict the use of copyrighted materials and other forms of intellectual property.
- Digital Signature – A cryptographic technique that uses asymmetric encryption and hashing to provide non-repudiation, authentication, and integrity for a document or message.
- Disaster recovery – The process of restoring the normal operations and functions of an organization after a disruption.
- Due care – The act of doing what a reasonable person would do in a given situation, to avoid negligence and harm.
- Due diligence – The management of due care, by following a process to ensure compliance and effectiveness of policies and controls.
- Dynamic Application Security Testing (DAST) – An active method of testing code while executing it, such as fuzzing and black box testing.
- Dynamic Testing – An active method of testing code while executing it. It includes fuzzing, black box testing, combinatorial testing, and misuse case testing.
E
- eDiscovery – Electronic discovery. The process of identifying, preserving, collecting, processing, reviewing, and producing electronically stored information for legal purposes.
- Electronic Vaulting – The batch process of electronically transmitting data that is to be backed up on a routine, regularly scheduled time interval.
- Encryption – The process of transforming data into an unreadable form, using a secret key or algorithm, to protect its confidentiality.
- Entity integrity – A database property that ensures that each tuple has a unique primary key that is not null.
- Environmental Controls – The physical and technical controls that maintain the optimal environmental conditions for a system or facility.
- Evaluation Methods, Certification and Accreditation – Processes and standards for assessing the security level and compliance of a system or product.
- Expert system – A type of artificial intelligence that uses a knowledge base of “if/then” statements and an inference engine to make decisions based on rules.
F
- Federated Identity Management (FIdM) – A type of identity management that enables single sign-on across multiple systems and domains, using standards such as SAML or OpenID.
- Firewall – A device or software that filters traffic based on rules and policies.
- Foreign key – A key in a related database table that matches a primary key in a parent database table.
- Forensics – A formal approach to dealing with investigations and evidence with special consideration of the legal aspects of this process.
- Fourth-generation programming language (4GL) – A computer programming language that is designed to increase a programmer’s efficiency by automating the creation of computer programming code.
- Free software – Software that is free of charge to use (gratis) or free to use in any way (libre), or both.
- Fuzzing – A type of black box testing that submits random, malformed data as inputs into software programs to determine if they will crash.
G
- Genetic algorithm and programming – A type of artificial intelligence that uses evolutionary principles to generate code that solves a problem.
H
- Hashing – The process of applying a mathematical function to data, to produce a fixed-length output called a hash or digest.
- History of Cryptography – The origin and evolution of cryptography, from ancient ciphers to modern algorithms and standards.
- HMAC – Hash-based Message Authentication Code, a technique that uses hashing and a secret key to verify the integrity and authenticity of a message.
- Honeypot – A decoy system or network that is designed to attract and trap attackers.
I
- Identity and Access Management (IAM) – A set of processes, policies, and tools that regulate who or what has access to applications in the cloud or on-premises.
- Identity Federation – The process of delegating the responsibility of authenticating a user to a trusted external party.
- Identity Management – The process of creating, maintaining, and terminating digital identities for users and devices.
- Identity-as-a-Service (IDaaS) – A cloud-based delivery model for identity and access management solutions.
- IDS and IPS – Intrusion Detection System and Intrusion Prevention System, devices or software that monitor network or system activity for malicious or anomalous behavior.
- Implementing Cryptography – The practical aspects and challenges of applying cryptography in real-world scenarios.
- Incident response – A process of preparing for, detecting, containing, analyzing, and recovering from security incidents.
- Inference and Aggregation – Two types of attacks that exploit the logical connections or mathematical calculations between lower-level data to derive higher-level information.
- Inheritance – A mechanism that allows an object to acquire the attributes and methods of another object or class.
- Integrated Development Environment (IDE) – A software application that provides a programmer with a single interface that can perform editing, debugging, syntax checking and highlighting, compiling, interpreting, and version control functions.
- Integrity – Seeks to prevent unauthorized modification of information.
- Intellectual property – The intangible creations of the human mind, such as inventions, artistic works, designs, and symbols.
- Interface Testing – A method of testing the different ways users can interact with the application.
- Interpreter – A program that translates and executes source code on the fly, without producing an executable file.
- IP – Internet Protocol, a network layer protocol that provides logical addressing and routing for packets across the Internet.
- IPv4 – Internet Protocol version 4, which uses 32-bit addresses to identify hosts and networks.
- IPv6 – Internet Protocol version 6, which uses 128-bit addresses to identify hosts and networks.
K
- Kerberos – A third-party authentication service that uses tickets and encryption to provide single sign-on and mutual authentication.
- Key Clustering – A phenomenon that occurs when two different symmetric keys produce the same ciphertext for the same plaintext.
L
- Least privilege – The principle of granting users the minimum amount of access (authorization) required to do their jobs, but no more.
- Lightweight Directory Access Protocol (LDAP) – A common open protocol for interfacing and querying directory service information provided by network operating systems.
M
- MAC address – A unique hardware address of an Ethernet network interface card (NIC).
- Machine code – Software that is executed directly by the CPU.
- Malware – Malicious software that performs harmful or unwanted actions on a system.
- Message – An input or output that is sent or received by an object.
- Method – A function or procedure that is performed by an object.
- MTD – Maximum Tolerable Downtime. The maximum amount of time that a system or service can be unavailable.
- Multi-factor Authentication (MFA) – A technique that requires users to provide more than one piece of evidence to prove their identity.
N
- NAT – Network Address Translation, a technique that allows private IP addresses to be translated into public IP addresses.
- Need to know – The principle of granting users access to a specific piece of information only if they have a business need to do so.
- Non-repudiation – The ability to prove the origin and integrity of a transaction or message.
O
- Object – A passive entity on an information system (e.g., file) or a “black box” that combines code and data and sends and receives messages (in programming).
- Object-oriented language – A computer programming language that models the real world through the use of objects that combine methods and data.
- Open source software – Software that publishes source code publicly, allowing users to modify and share it.
P
- Packet – A unit of data that is transmitted over a packet-switched network.
- Packet-switched network – A form of networking where bandwidth is shared and data is carried in units called packets.
- Patent – A legal right that grants a monopoly to the inventor of a novel and useful invention.
- Penetration Test – An authorized attempt to break into an organization’s physical or electronic perimeter to demonstrate real-world risk.
- Penetration testing – A method of evaluating the security of a system or network by simulating an attack.
- Perimeter Defenses – The security measures and devices that protect the boundary of a system or network from unauthorized access.
- Phishing – A type of social engineering attack that uses fraudulent emails or websites to trick users into revealing sensitive information.
- PKI – Public Key Infrastructure, a system that manages the creation, distribution, and verification of digital certificates and public keys.
- Polyinstantiation – A technique that allows multiple records with the same primary key to exist in a multilevel secure database, or a mechanism that allows two objects with the same name to contain different data.
- Polymorphism – A mechanism that allows an object to change its behavior based on the context of the message.
- Privileged Access Management (PAM) – A technique that controls and monitors the access of users or devices that have elevated privileges.
- Procedural language – A computer programming language that uses subroutines, procedures, and functions.
- Proprietary software – Software that is subject to intellectual property protections such as patents or copyrights.
- Proxy – A device or software that acts as an intermediary between a client and a server.
R
- RAID – Redundant Array of Inexpensive Disks. A method of using multiple disk drives to achieve greater data reliability, greater speed, or both.
- Referential integrity – A database property that ensures that every foreign key in a secondary table matches a primary key in the parent table.
- Relational database – A database that contains two-dimensional tables of related data.
- Religious law – A legal system that derives from religious doctrine or interpretation.
- Return on Investment – Money saved by deploying a safeguard.
- Ring Model – A hardware-based security model that uses different privilege levels to isolate and protect domains.
- Risk – A matched threat and vulnerability.
- Risk assessment – A process of identifying, analyzing, and evaluating the risks that an organization faces.
- Role-Based Access Control (RBAC) – A model that assigns access permissions to users based on their roles in an organization.
- Router – A network device that routes packets from one network to another.
- RTO – Recovery Time Objective. The target time for restoring a system or service after a disruption.
S
- Safeguard – A measure taken to reduce risk.
- Scoping – The process of determining which portions of a standard will be employed by an organization.
- Secure Hardware Architecture – The design and implementation of hardware components and devices that support security functions and features.
- Secure Operating System and Software Architecture – The design and implementation of software components and applications that support security functions and features.
- Secure System Design Concepts – Principles and best practices for creating secure systems.
- Security Assessment – A holistic approach to determining the effectiveness of access control, with a broad scope that may include other tests.
- Security Association Markup Language (SAML) – An XML-based framework for exchanging security information between different systems and domains.
- Security Audit – A test against a published standard to verify an organization’s compliance with the specified requirements.
- Security Engineering – The discipline of designing, building, and maintaining secure systems.
- Security Models – Formal frameworks that define the rules and principles for implementing and enforcing security policies in a system.
- Semantic integrity – A database property that ensures that each attribute value is consistent with the attribute data type.
- Single Sign-On (SSO) – A technique that allows users to authenticate once and then access multiple, different systems without re-authenticating.
- Site Marking – A design decision that determines whether a facility or data center is externally labeled or identified.
- Site Selection, Design, and Configuration – The process and criteria for choosing, building, and setting up a secure facility or data center.
- Smart Card – A physical access control device that contains an integrated circuit chip that can store and process data.
- Software escrow – A contractual arrangement where a neutral third party holds the source code of a software product.
- Software licensing – A legal agreement that defines the rights and obligations of the software provider and the software user.
- Solid State Drive (SSD) – A type of storage device that uses flash memory and DRAM to store data.
- Source code – Computer programming language instructions that are written in text.
- State Machine Model – A mathematical model that represents all the possible states and transitions of a system.
- Static Application Security Testing (SAST) – A passive method of testing code without executing it.
- Static Testing – A passive method of testing code without executing it, including walkthroughs, syntax checking, and code reviews.
- Subject – An active entity on an information system, such as a user or a program, that can manipulate objects.
- Symmetric cryptography – A type of encryption that uses the same key for encryption and decryption.
- Synthetic Transactions – Scripts or tools that simulate activities normally performed in an application to establish expected performance norms.
- System Defenses – The security measures and devices that protect the internal components and data of a system or network.
- System Vulnerabilities, Threats and Countermeasures – The identification and analysis of weaknesses, risks, and attacks that affect a system.
T
- Tailoring – The process of customizing a standard for an organization.
- TCP – Transmission Control Protocol, a reliable, connection-oriented transport layer protocol.
- Test Coverage Analysis – A method of measuring the degree to which code testing applies to the entire application.
- The OSI model – A network model with seven layers: physical, data link, network, transport, session, presentation, and application.
- The TCP/IP model – A simpler network model with four layers: network access, Internet, transport, and application.
- Threat – A potentially negative occurrence.
- Threat hunting – The proactive search for indicators of intrusions or adversary activities within an organization’s network or systems.
- Threat Modeling – A process of identifying, analyzing, and mitigating the threats to a system or application.
- TLS and IPsec – Two protocols that provide security for data in transit.
- Top-Down programming – A programming approach that starts with the broadest and highest level requirements and works down towards low-level details.
- Total Cost of Ownership – The cost of a safeguard.
- Traceability Matrix – A tool that maps customer requirements or use cases to the software testing plan or test cases.
- Trade secret – A legal right that protects any confidential and valuable information that gives a competitive advantage to its owner.
- Trademark – A legal right that grants the owner of a distinctive sign, symbol, or slogan the exclusive right to use it.
- Transitive Trust – A trust relationship that extends to other trust partners.
- Types of Cryptography – The classification and comparison of different cryptographic methods and systems.
U
- UDP – User Datagram Protocol, an unreliable, connectionless transport layer protocol.
V
- Virtualization and Distributed Computing – Technologies and methods for creating and managing multiple virtual machines or systems.
- VPN – Virtual Private Network, a secure tunnel that encrypts and protects data in transit over a public network.
- Vulnerability – A weakness in a system.
- Vulnerability Assessment – A scan of a network or system for a list of predefined vulnerabilities.
- Vulnerability scanning – A method of assessing the security of a system or network by using automated tools to detect and report known vulnerabilities.
W
- WRT – Work Recovery Time. The time required to resume normal business operations after recovering from a disruption.
Z
- Zero-day – A vulnerability that is unknown to the vendor or the public.
- Zero Trust – A security model that assumes no network user, packet, interface, or device is trusted.