Table of Contents
The Domain 2 – Information Security Risk Management of CISM exam holds a total weightage of 20% in the exam.
Below are the summaries of key objectives of Domain 2 – Information Security Risk Management.
The Information Risk Management (IRM) domain of the CISM exam focuses on the systematic application of management practices, processes, and policies to detect, monitor, evaluate, and report information-related risks.
- Benefits and Outcomes from an Information Risk Management Perspective: This section focuses on the advantages of implementing effective information risk management practices, such as improved decision-making, increased efficiency, and reduced risk exposure.
- Risk Assessment and Risk Management Frameworks: Candidates should be familiar with various risk assessment and management frameworks, such as ISO 27001, NIST, and COBIT, and how to apply them in different contexts.
- Developing a Risk Management Strategy: This involves understanding the steps required to develop a comprehensive risk management strategy, including identifying key stakeholders, setting objectives, and allocating resources.
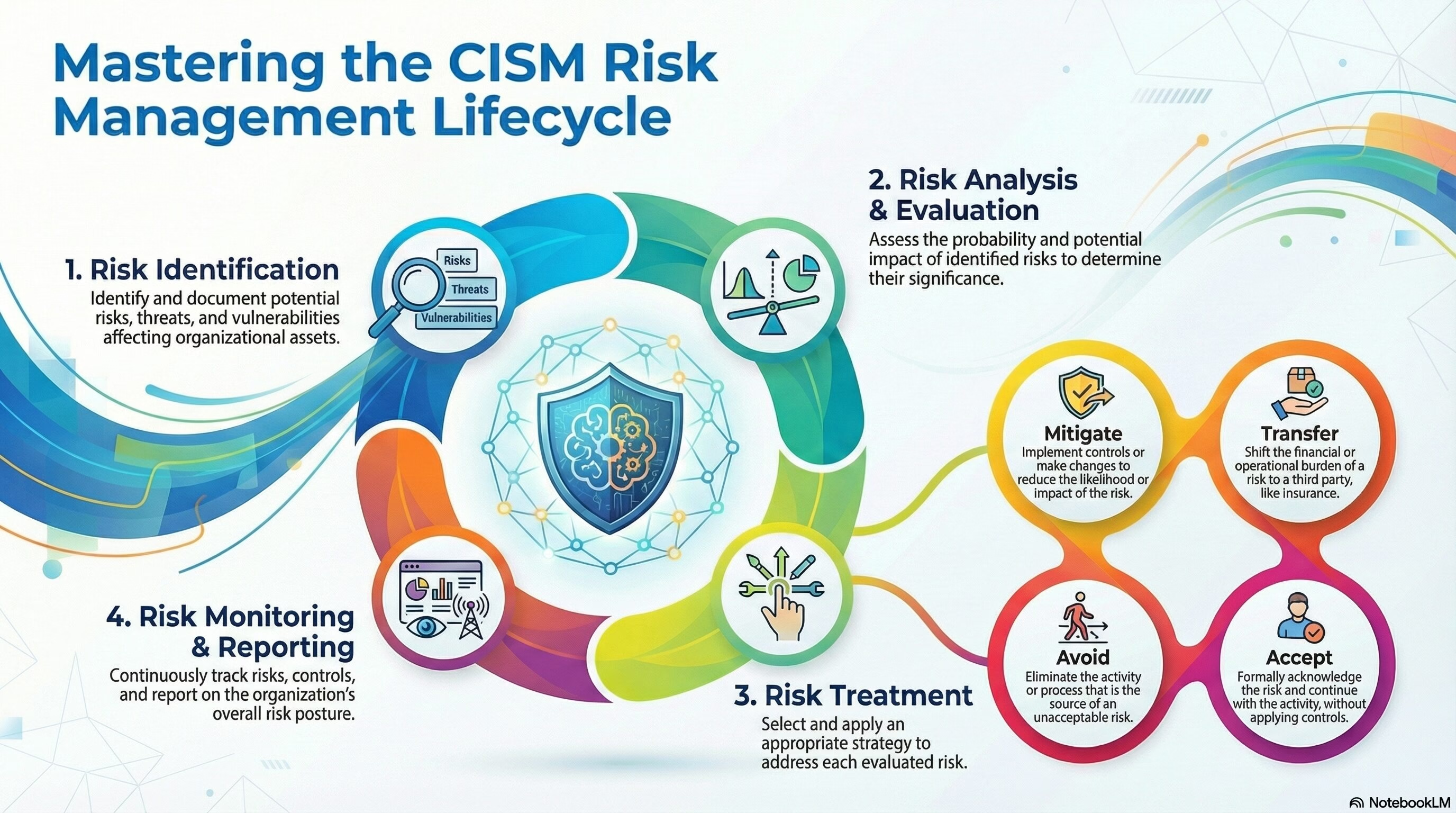
- The Risk Management Life-Cycle Process: This includes the various stages of the risk management process, such as risk identification, risk analysis, risk evaluation, risk treatment, and risk monitoring and reporting.
- Integrating Risk Management into an Organization’s Practices and Culture: Candidates should be able to explain how to embed risk management into an organization’s overall practices and culture, ensuring that it becomes an integral part of the organization’s decision-making processes.
- The Components of a Risk Assessment: This involves understanding the key elements of a risk assessment, including asset value, vulnerabilities, threats, probability, and impact of occurrence.
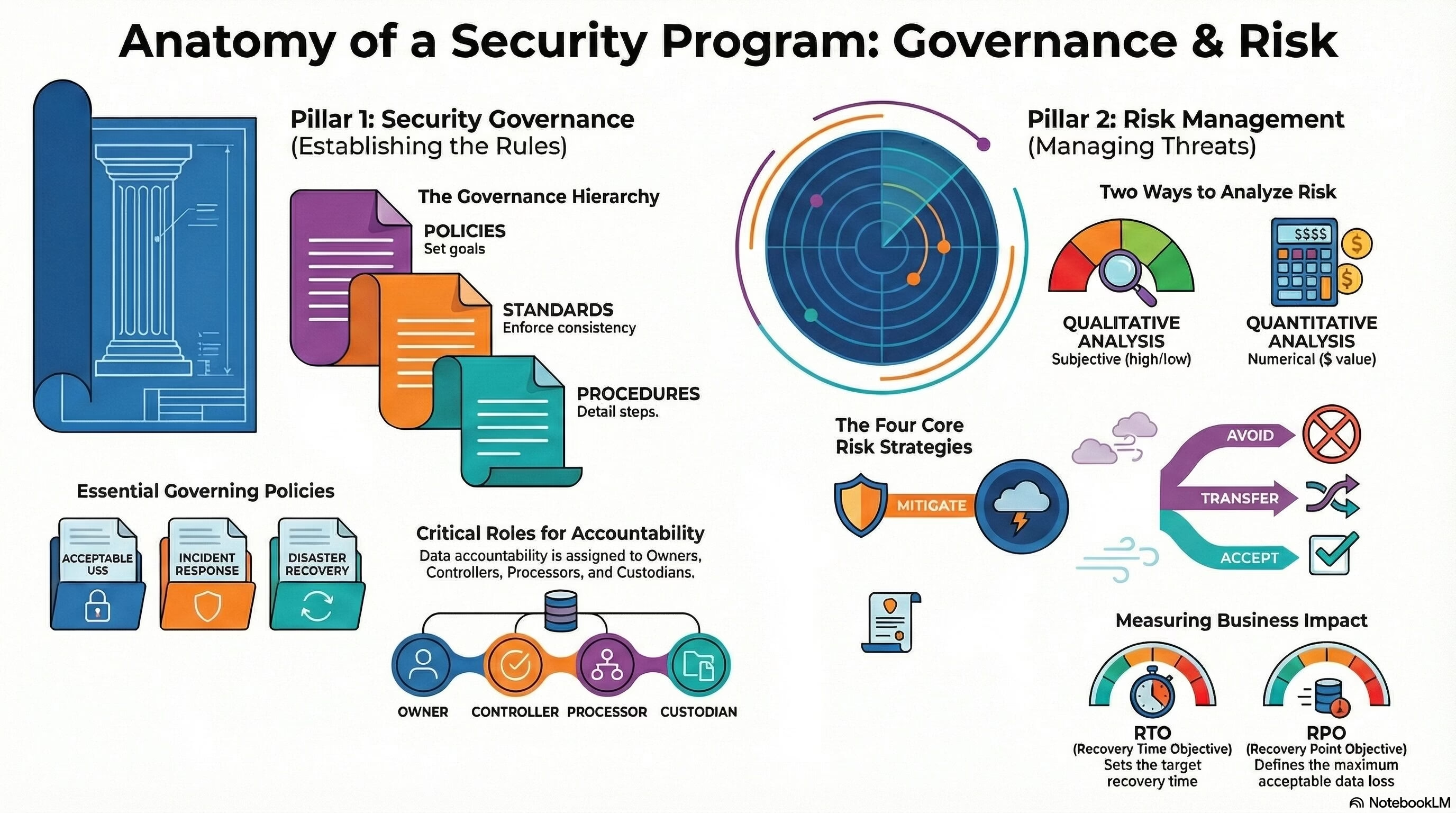
- Risk Treatment Options: Candidates should be familiar with the different risk treatment options, such as mitigate, accept, transfer, and avoid, and how to apply them effectively in different scenarios.
- The Risk Register: This includes understanding the purpose and content of a risk register, which is a central repository for recording and tracking risks and their associated controls.
- Monitoring and Reporting Risk: This involves understanding the process of monitoring risks and controls, as well as reporting on the organization’s risk posture and the effectiveness of risk management strategies.
These objectives are essential for information security professionals to effectively manage information risks within an organization, ensuring that the organization’s information assets are protected and its risk exposure is minimized.
Unique Terms and Definitions from Domain 2 – Information Security Risk Management
- Information Risk Management – The practice of balancing business opportunity with potential information security-related losses.
- Risk Assessment – The process of identifying, analyzing and evaluating risk.
- Risk Management – The process of identifying, assessing, and controlling risks arising from operational factors and making decisions that balance risk costs with mission benefits.
- Risk Appetite – The level of risk that an organization is willing to accept while in pursuit of its objectives.
- Risk Tolerance – The acceptable level of variation relative to the achievement of objectives.
- FAIR (Factor Analysis of Information Risk) – An analysis method that helps understand the factors that contribute to risk and estimate the probability and impact of losses.
- OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) – A risk analysis approach to identify and manage information security risks.
- Asset – Anything that has value to the organization including people, information, technology, facilities and reputation.
- Threat – An event that could negatively impact an asset.
- Vulnerability – A weakness that could be exploited by a threat to harm an asset.
- Risk Register – A log of risks that contains information about the risk, affected assets, probability, impact and treatment.
- Residual Risk – The risk that remains after risk treatment activities have been applied.
- Risk Avoidance – Eliminating aspects of operations that pose unacceptable risks.
- Risk Acceptance – Accepting the potential risk and continuing with the activity.
- Risk Mitigation – Implementing controls or making changes to reduce the impact or likelihood of the risk.
- Risk Transfer – Shifting the risk to another party, often through insurance or outsourcing.
- Risk Communication – Sharing information about risk management policies, processes and decisions with stakeholders.
- RTO (Recovery Time Objective) – The maximum tolerable time period from an outage to service resumption.
- RPO (Recovery Point Objective) – The maximum data loss that is acceptable during a disaster recovery.
- KRI (Key Risk Indicator) – A metric that provides insight into the organization’s risk position.
- SIEM (Security Information and Event Management) – Software that aggregates and analyzes log data from across an organization’s infrastructure.
- DLP (Data Loss Prevention) – Solutions designed to detect potential data breaches and prevent data exfiltration.
- IDS (Intrusion Detection System) – Monitors network traffic and system activity for malicious activity and generates alerts.
- IPS (Intrusion Prevention System) – Monitors network traffic like an IDS but can also block potentially malicious traffic.
- CASB (Cloud Access Security Broker) – Solutions that secure the use of cloud services by enforcing security policies.
- SAST (Static Application Security Testing) – Analyzing application source code, binaries or bytecode for coding and design conditions that are indicative of security vulnerabilities.
- DAST (Dynamic Application Security Testing) – Testing applications while they are running to identify vulnerabilities and security flaws.
- PAM (Privileged Access Management) – Systems that secure, control and monitor privileged access to critical assets.
- PKI (Public Key Infrastructure) – A system for the creation, storage, distribution and revocation of digital certificates based on public-key cryptography.
- UBA (User Behavior Analytics) – Solutions that apply analytics and machine learning to detect insider threats, account compromise, and risky user activity.
- UTM (Unified Threat Management) – An integrated security solution that includes functions like firewall, anti-malware, IDS/IPS and more in one appliance.
- SOC (Security Operations Center) – A centralized unit that deals with security issues on an organizational and technical level.
- CTI (Cyber Threat Intelligence) – Analyzed information about threats that helps organizations detect and respond to security incidents.
- BYOD (Bring Your Own Device) – The policy of permitting employees to use personal mobile devices to access company data and systems.
- Shadow IT – Hardware, software or services within an enterprise that are not formally approved, provisioned or controlled by the organization’s IT department.
Multiple Choice Questions quiz
|
Flashcard quiz
|