Table of Contents
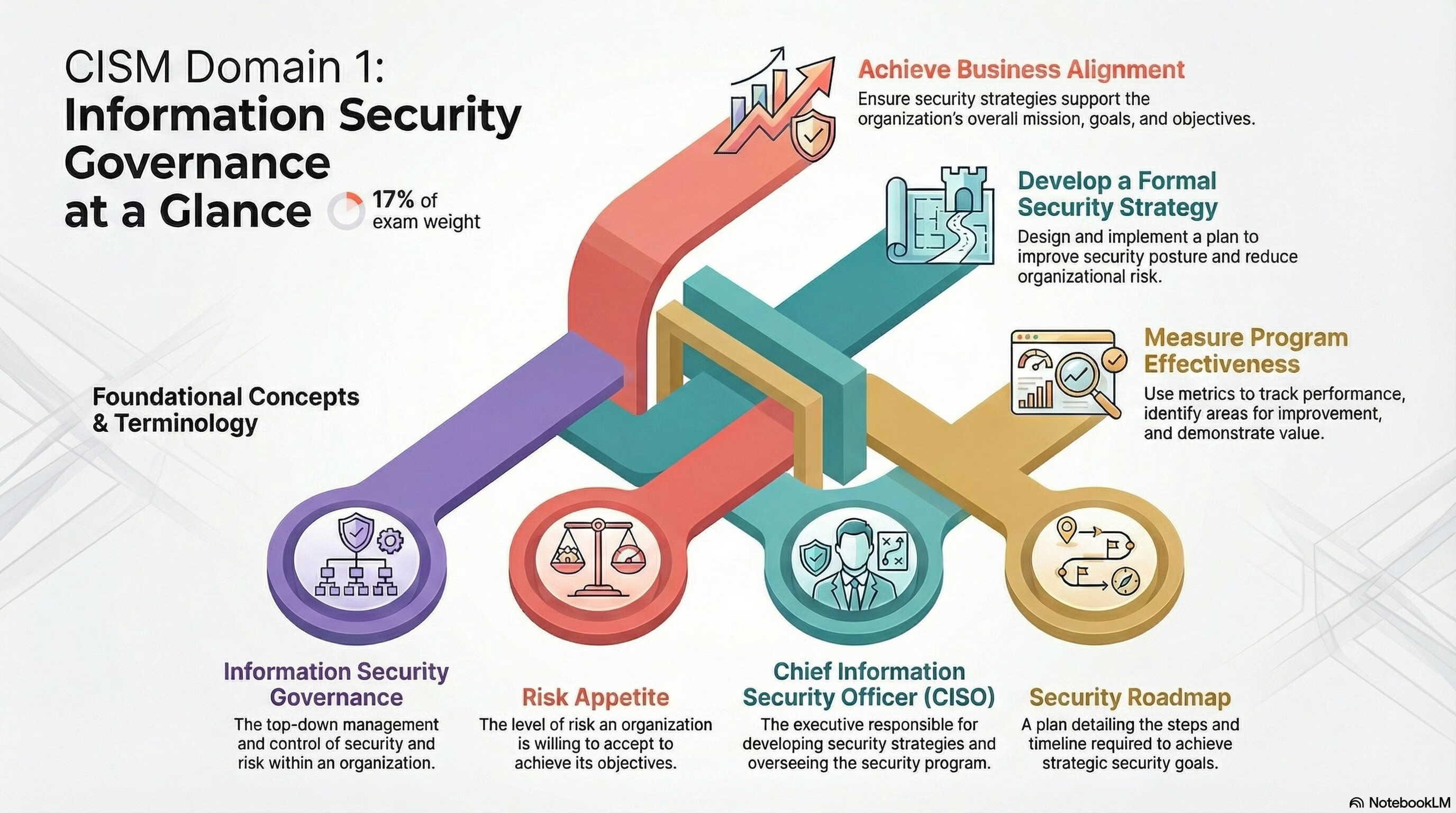
The Domain 1 – Information Security Governance of CISM exam holds a total weightage of 17% in the exam.
Below are the summaries of key objectives of Domain 1 – Information Security Governance.
The Information Security Governance domain of the CISM exam is focused on establishing and maintaining a framework to provide assurance that information security strategies are aligned with business objectives and consistent with applicable laws and regulations. This domain covers the following topics:
- Business alignment: Ensuring that information security strategies are aligned with business objectives and consistent with applicable laws and regulations.
- Security strategy development: Developing and implementing an information security strategy that supports the organization’s business objectives.
- Security governance activities: Establishing and maintaining a framework to provide assurance that information security strategies are aligned with business objectives and consistent with applicable laws and regulations.
- Information security strategy development: Designing, implementing, and maintaining an information security program that supports the information security governance framework and the organization’s business objectives.
- Resources needed to develop and execute a security strategy: Identifying the resources required to develop and execute an information security strategy.
- Obstacles to strategy development and execution: Identifying the obstacles that may hinder the development and execution of an information security strategy.
- Information security metrics: Establishing and maintaining metrics to measure the effectiveness of the information security program and to identify areas for improvement.
Unique Terms and Definitions from Domain 1 – Information Security Governance
- Information Security Governance: The top-down management and control of security and risk management in an organization, usually through a steering committee.
- Business Alignment: Ensuring that the information security program fits into and supports the overall organization’s mission, goals, objectives, and strategy.
- Risk Appetite: The level of risk that an organization is willing to accept in pursuit of its objectives.
- Roles and Responsibilities: Clear definitions of the security-related activities expected to be performed by different individuals and groups in an organization.
- Chief Information Security Officer (CISO): The highest-ranking security executive responsible for developing security strategies and overseeing the security program.
- Security Steering Committee: A group of stakeholders who provide strategic direction and oversight for information security governance activities.
- Security Governance Metrics: Measurements used to gauge the effectiveness of information security governance in achieving strategic alignment, risk optimization, value delivery, etc.
- Business Model for Information Security (BMIS): A framework with four key elements – organization, people, process, technology – and six dynamic interconnections that shows how everything is connected.
- Security Strategy: A plan to achieve defined security objectives to improve the organization’s security posture and reduce risk.
- Control Framework: A baseline set of information security controls, such as ISO 27001 or NIST 800-53.
- Gap Assessment: Analysis to identify differences between the current and desired future state of the security program.
- Capability Maturity Model: A methodology for evaluating process maturity on a scale (e.g. initial, repeatable, defined, managed, optimizing).
- Security Roadmap: A plan detailing the steps and timeline required to achieve strategic security objectives.
- Security Policy: Rules governing expected security behaviors and responsibilities throughout the organization.
- Security Standards: Detailed requirements for specific security implementation (e.g. encryption standards, access control standards).
- Security Awareness: Communications to personnel on security best practices, risks, and responsibilities.
- Third-Party Risk: The process of assessing and managing risks associated with vendors and other external service providers.
- Normalcy Bias: The tendency to believe that because something disastrous has never happened, it never will.
- Organizational Inertia: An organization’s resistance to change, limiting its capacity to implement changes within a given timeframe.
- Risk Assessment: A process to identify and analyze security risks facing the organization.
- Threat Assessment: A process to identify relevant threats to the organization.
- Vulnerability Assessment: A review to identify weaknesses in systems that could be exploited.
- Security Incident Log: A record of security events and responses used to identify trends and drive improvements.
- Security Metrics: Measurements of security performance, risk, alignment to objectives, etc. to understand program effectiveness.
- Security Culture: The attitudes, assumptions, and priorities surrounding security within an organization.
- Security Maturity: The level of formality, repeatability, and optimization of security practices.
- Risk Ledger: A record reflecting risk assessments, threat assessments, vulnerabilities, incidents, and other risk management activities.
- Security Balanced Scorecard: A tool to measure security performance against strategic objectives in categories like financial, customer, internal, innovation.
- Return on Security Investment (ROSI): The value delivered by security investments, often difficult to quantify due to unpredictable losses.
- Technical Debt: Problems in information systems stemming from poor design lacking architectural principles.
- Strengths Weaknesses Opportunities Threats (SWOT) Analysis: Introspective analysis of internal strengths/weaknesses and external opportunities/threats.
- Security Roadmap: A plan detailing the steps and timeline required to achieve strategic security objectives.
- Business Case: A document justifying a proposed initiative through cost/benefit analysis.
- Security Constraints: Practical obstacles that may impact the ability to achieve strategic security objectives as planned.
- Acceptable Risk: The degree of risk exposure an organization is willing to tolerate relative to its risk appetite.
Multiple Choice Questions quiz
|
Flashcard quiz
|