Creating an effective security strategy is a critical part of organizations wanting to defend their digital assets and reduce risks. As I go through this while revising for my cybersecurity concepts, I find that the concept of understanding what’s included… Read More "Crafting an Effective Security Strategy"
Introduction to Information Security Governance
Today, Information Security Governance is not just a need but a foundational framework the organizations must embrace to protect the data and, in turn, establish trust with the customers. While preparing for my future cybersecurity exam, I realize that there… Read More "Introduction to Information Security Governance"
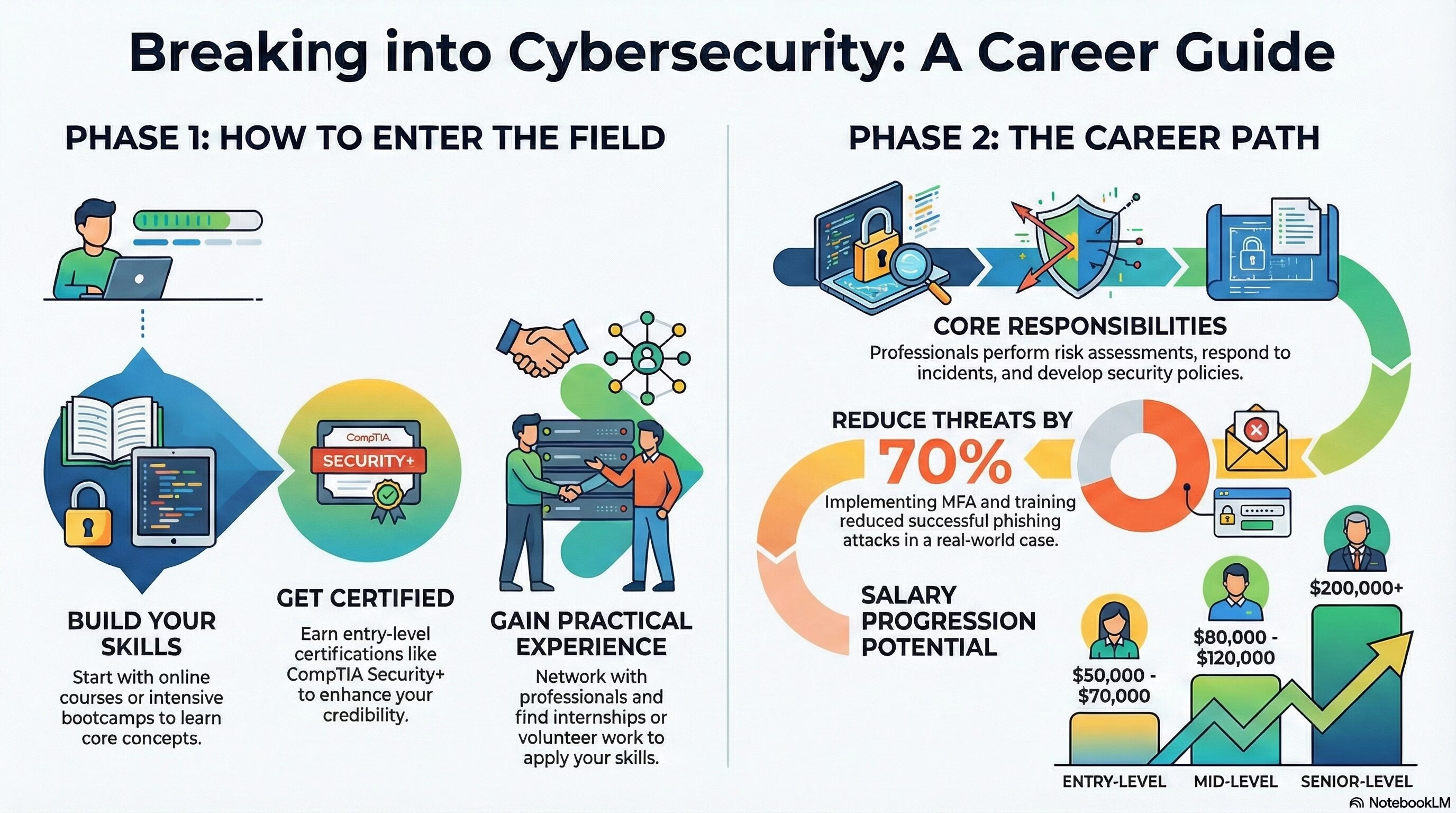
What is Cybersecurity? Getting started, salary & responsibilities
As a professional having more than 11 year in Cybersecurity domain, I have witnessed firsthand the growing importance of cybersecurity in today’s technology-driven world. In this article, I will explore the essentials of cybersecurity, how to break into the field,… Read More "What is Cybersecurity? Getting started, salary & responsibilities"
The Impact of Artificial Intelligence in Cybersecurity
Artificial Intelligence has transformed the way cybersecurity is approached, furthering threat detection and response times, including big data analysis. Some of the main AI concepts reviewed in the paper include Expert Systems, Artificial Neural Networks, Bayesian Filtering, and Genetic Algorithms;… Read More "The Impact of Artificial Intelligence in Cybersecurity"
The Role of Object-Oriented Design and Programming in Cybersecurity
Object-oriented design and programming are some of the major paradigms in software development, including cybersecurity. This is because object-oriented design and programming allow the developer to build modular, reusable, and maintainable code structures that improve the security of the software.… Read More "The Role of Object-Oriented Design and Programming in Cybersecurity"
Understanding Databases in Cybersecurity
Databases form the basis on which modern applications stand, especially in matters of security that call for utmost care and vigilance to ensure the integrity and security of data. This article takes a look at some aspects related to databases… Read More "Understanding Databases in Cybersecurity"
Comprehensive Guide to Application Development Methods in Cybersecurity
This article describes some key methodologies using practical examples and scenarios that set their importance in the context of cybersecurity. The Waterfall Model The waterfall model is a linear successive software development methodology. It means each phase needs to be… Read More "Comprehensive Guide to Application Development Methods in Cybersecurity"
Comprehensive Guide to Programming Concepts in Cybersecurity
This article considers some of the fundamental concepts of programming a person studying for cybersecurity certifications should understand. It will provide practical examples in an attempt to explain why this matters. Machine Code, Source Code, and Assemblers Machines consist of… Read More "Comprehensive Guide to Programming Concepts in Cybersecurity"
DRP Testing, Training, and Awareness
DRP involves preparing an organization for recovery from a disruptive incident, which encompasses way more than having a documented plan. It needs to include employee knowledge in terms of training and job roles in case a disaster strikes. This article… Read More "DRP Testing, Training, and Awareness"
Backups and Availability: Ensuring Data Resilience
In fact, effective backup strategies ensure the ability to recover in case of hardware failures, cyber attacks, and natural calamities. This article shall explain the concepts of backups and availability with an emphasis on hardcopy data, electronic backups, and software… Read More "Backups and Availability: Ensuring Data Resilience"
